|
Getting your Trinity Audio player ready...
|
fIt is likely that the recent SolarWinds hack will become known as the worst cybersecurity breach in United States history—affecting the most sensitive government networks and critical U.S. infrastructure, including top agencies and thousands of the biggest international brands.
Yes, you read that correctly.
Since at least March 2020, an unknown hacking entity had gained access through an unsecured update server of a monitoring and management software made by SolarWinds called Orion IT. This allowed the attackers to gain access to any of the SolarWinds clients connected through the popular monitoring tool—including the National Nuclear Security Administration, which maintains the U.S. nuclear weapons stockpile.
Believe it or not, it is a familiar story, one that is all too common during this tumultuous past year of pandemic lockdowns and our heavy reliance of the internet. A year that has introduced new vernacular into our vocabulary such as zoom bombings, spearfishing and clickjacking.
Year-over-year, cybersecurity budgets and spending continue to increase for both the private and public sectors. According to Gartner, Information security spending is expected to grow 2.4% to reach $123.8 billion in 2020.
Technology manufacturers and service providers have also responded with new security-featured hardware and software offerings—yet these “upgrades” do not seem too capable to impede the frequency or success of the cyber-attacks.
The truth is that 90% of all cyber-attacks are the result of human error—whether it is visiting the wrong website, trusting the wrong email, using weak authentication, ignoring updates, misconfigurations, and patches. When someone gains unauthorized access to a network, it is typically through a human-made mistake.
But can the human element of data-security be mitigated to help prevent mistakes and outside interference from occurring in the future?
Enter blockchain
Up until early 2020, the “blockchain as a solution” answer to many of today’s data challenges had been an unrealized promise. Issues with scalability, misunderstandings about privacy, high transaction fees, lack of interoperability and an ever-changing ruleset by tinkering blockchain developers who are prone to disagree about how to overcome the challenges has prevented any significant adoption or global standardized protocol.
On a broad development level, there have been many great ideas on how to solve today’s cybersecurity flaws with blockchain, including focused efforts on mitigating the human element and reliance on centralized third-part certificate authorities.
Some of these efforts utilizing blockchain technology for cybersecurity solutions include:
- Secure Private Messaging
- Improved IoT and Edge Device Security
- Boosting or even replacing current PKI
- Reducing DDoS attacks
- Decentralized and Encrypted Storage
- Provenance of Software
- Verification of Cyber-Physical Infrastructures
- Data Transmission
Unfortunately, all of these semi-matured efforts are currently left without any real ability to scale and meet the demands and needs of today’s enterprise cybersecurity applications—they are just too expensive and inefficient to implement due to the blockchains they have been built on.
The good news is that recent innovative scaling breakthroughs in the original Bitcoin protocol is making these solutions possible today!
In February of 2020, the Bitcoin SV (BSV) blockchain activated the Genesis update which ushered in the return to the original, limitless, unbounded Bitcoin Satoshi Vision.
It is now entirely possible to take on these cybersecurity challenges with the BSV blockchain.
Back to SolarWinds
As I previously mentioned, SolarWinds used a compromised open-source library that allowed hackers to imprint and access “God-View” privileges into any of the client networks that downloaded the standard security update of Orion monitoring software.
As unsuspecting customers installed the update and malicious payload, their network opened the door to further undetected compromise and unauthorized surveillance—for months. The damage may not have stopped there, any other unsecured outside networks that an infected company was connected to such as vendors or partners could also possibly be compromised.
Worse yet, further malicious time-based payloads could have been deployed and be dormant in all of these infected systems—even after a thorough “clean up.”
The total cost and consequences of this specific hack is completely unknown and to be quite honest, unfathomable—but it will certainly be considered the most expensive cyber-incident in global history.
Bitcoin SV solves this now
What if software updates like these occurred in an entirely different, more secure, and efficient way? One that could guarantee the integrity of the file and reduce the security concerns in deployment?
What if I suggested that by using the public, enterprise-grade blockchain Bitcoin SV, this specific hack may have prevented for less than $5.
Meet Roy Murphy, CEO of Veribit, a Bitcoin SV based identity and verification platform launching in Q1 of 2021. As a computer scientist and enterprise architect, he works closely with large organizations teaching them how to leverage the unbounded scaling and power of Bitcoin scripting in their applications.
Through his various experiments of testing use-cases and chain limitations, Roy has also found time to upload some of his favorite retro games to run on the Bitcoin SV blockchain—including PacMan.
“I have uploaded various UI and Javascript libraries to BSV to create onchain games. Versioning of these libraries can be a single use transaction, so no need for downloading and checking the payload with a PGP key to see if the downloaded copy is the same as the origin file.”
Bitcoin SV libraries can have just one file as a transaction allowing anyone to reference. Common libraries can hold the transaction in local memory, much like a cookie expires today, without the security issues.
“Progeny of files and common libraries is key to scaling applications. It has provable provenance and unlike a CDN, only one copy exists in a distributed system, but all node only requires the digest, not the whole file. Very few people understand the implications of this yet, or how powerful this can be.”
Extremely powerful.
Let’s use Roy’s PacMan game for an example.
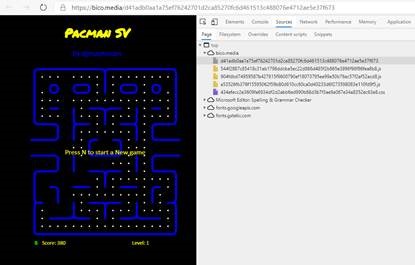
The entire game is served through a series of one-time, low-cost (less than 1/100th of a cent) Bitcoin SV transactions that are merged using a free BSV protocol called Bico.Media.
As the nature of blockchain technology is to store records immutably across its distributed, time-stamped ledger, this provides the perfect file system and distribution method for all sorts of content—but more on that later.
As you can see with inspecting the PacMan game, it is not difficult to visualize how the Bitcoin SV-based game completely replaces the traditional folder for JS and CSS. If these files needed to be updated, a new transaction could be securely sent providing an audit trail and timestamp of the change.
As PacMan isn’t gobbling up cyber-criminals just yet, this example should serve as Proof of Work that Bitcoin SV has the infrastructure and capabilities to take on these challenges right now.
Smart contracts, tokenization and even basic encryption technics could be used to protect and obfuscate any data that a software or content distributor may require hidden from using a public blockchain like Bitcoin SV.
This is further evidenced by the recent news of the release of sCrypt, a high-level, turing complete smart contract language and The Game of Life.
Blockchain technology has always had the potential to solve some of humanities toughest challenges as well as empower people and businesses across our global landscape, now we have a universal source of Truth that has been unleashed from limitation and is ready to serve.
The biggest challenge we face now is breaking away from traditional deployment and legacy infrastructure and having the imagination to redesign them using Bitcoin SV.
The question is, who will build it?

 03-10-2026
03-10-2026 




