|
Getting your Trinity Audio player ready...
|
This post was first published on Medium.
ZK Key-Statement Proof
Previously, we have showed how to construct zero-knowledge proof (ZKP) for the following statement, using a technique called ZK Key-Statement Proof (ZKKSP).
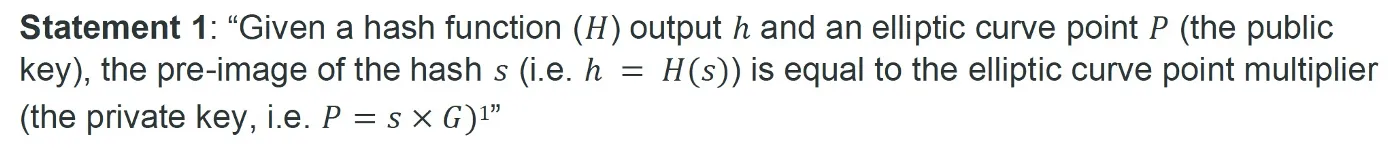
Basically, it proves not only the prover knows a secret key to a given public key, but also the secret hashes to a given digest, without leaking the secret.

Although ZKKSP works, it has a severe limitation: it only works for one specific form of statement, i.e., a secret is the private key of a given public key, and it is also the preimage of a given hash. It is unclear how to extend it to a slightly modified statement, say, the secret is also an even number, besides being a private key and preimage. Furthermore, coming up with it requires patent-level knowledge of cryptography, such as ∑-protocol and commitment schemes.
ZKKSP using zkSNARKs
We reimplement ZKKSP by leveraging the programmability of zkSNARKs. We simply combine elliptic curve point multiplication used in Part 2 and hashing library. The resulting Circom code is listed below:
As before, we use ECDSAPrivToPub to derive a public key at Line 15 from the private key at Line 14 (note it is declared private). Then we hash the same private key using Sha256 from sha256 library imported at Line 3, to ensure the result matches the given hash at Line17. We have just “programmed” ZKKSP, no prior knowledge of advanced cryptography required. In addition, we can easily extend it to add constraints on the secret, e.g., being even, thanks to the composability of zkSNARKs.
A test can be found here.
Watch: The BSV Global Blockchain Convention presentation, Smart Contracts and Computation on BSV
https://www.youtube.com/watch?v=c_zAlkImgTU&feature=youtu.be

 07-18-2025
07-18-2025 





