|
Getting your Trinity Audio player ready...
|
This article was first published on Dr. Craig Wright’s blog, and we republished with permission from the author.
We propose a solution to the double-spending problem using a peer-to-peer network…
The solution to the double-spending problem involves more than merely noticing that an attempted attack was made; it required that the system could be traced (Lee et al., 2003). Bitcoin broadcasts every transaction, and every transaction attempt, to every node (Wright, 2008, p. 3). Such a requirement is the first step in running a node; for a network node to function, it must ensure that “New transactions are broadcast to all nodes”. While nodes don’t require that a transaction is immediately found, the primary purpose of Bitcoin nodes is to act as a “time-stamp server to generate computational proof of the chronological order of transactions” (Wright, 2008, p. 1).
Brands (1994) discussed the capability of integrating traceability of double-spending into blind signature schemes. The author noted that protections against double-spending “may be trivially attained in systems with full traceability of payments” (Brands, 1994, p. 1). Yet, it was argued that introducing traceability would “require either a great sacrifice in efficiency or seem to have questionable security, if not both”. At the same time, the requirement to address the double-spending problem does not necessitate everyone participating in the network seeing all transactions.
The problem that Brands (1994) noted is associated with blind signature schemes for privacy. Implementing a system that is designed not to reuse keys and to be able to form private key pairs based on the ECDH properties associated with ECDSA (Wright & Savanah, 2022) allows a solution to the double-spending problem. In requiring new keys derived from a master key, privacy is maintained while linking identity. As the participants in a transaction can securely create new keys without interacting, based on information such as PKI-based identity keys, privacy can be maintained between the individuals while broadcasting information to observers.
Ferguson (1994) extended an earlier electronic cash scheme to provide for coins that could be spent multiple times. The system incorporated observers into the protocol. By having entities validate and watch transactions, the process enabled double-spending to be captured and stopped or, at the worst, found and traced after the event. For example, Ferguson (1994, p. 296) explained that when two parties, Alice and Bob, are transacting, there “is no cryptographic way in which we can prevent Alice from spending the same coin twice in an off-line system”. Here, adding observers makes it possible to monitor the system for double-spending and stop any attempt.
Ferguson (1994, p. 296) argued that an observer must be produced by a central authority, with its own native digital signature scheme. The problem with such an approach is the necessity to incorporate a trusted third party and increase the cost of transacting, making micropayments prohibitive. In such schemes, blind signatures were used, incorporating anonymous transactions that would only be traceable in the case of a double-spending attempt (Hou & Tan, 2004), minimizing the ability to trace illicit activity because of the anonymous nature of the system.
Other authors noted that anonymity was a critical component of electronic commerce (Camenisch et al., 1997), and sought to use a trusted third party as a trustee, or a set of trustees, that could selectively revoke the anonymity of participants. The authors argued that trustees would only operate in cases of justified suspicion. Yet, the revocation of anonymity has proven to be an ongoing problem, and such a system would reduce anonymity and privacy in general. Importantly, when a government is allowed to interact with the privacy of individuals in a system, it is likely that they will end up abusing such privilege. Critically, the introduction of a trusted third party acting as a trustee provides the opportunity for malicious attackers to compromise the privacy of the system.
As Ferguson (1994, p. 296) observed, the only protection against double-spending attacks lies in identifying the attack or, subsequently, the user who did it. The requirement of an observer has been predicated on the necessity to have some sort of trusted third party or central authority. Hoepman (2006; J.-H. Hoepman, 2010) looked at implementing a peer-to-peer distributed network instead of using a central authority. Hird (2002) noted that reverse “cost shifting” could be implemented to reduce spam attacks on email, and discussed the problem of generating tokens for setting a price function. Bitcoin integrates a difficulty adjustment to ensure that the pricing is maintained evenly.
The process in Bitcoin utilises a proof-of-work algorithm (Aura et al., 2001). The system discussed by Hird (2002) showed how the distributed systems proposed by Back (2002) would suffer from the problem demonstrated by Hird (2002, pp. 212–213), where the difference in processing power between computer systems would allow some users to generate tokens faster than others. The economic difference between computational power would favor large operators and botnet facilitators over honest users. Consequently, bitcoin was designed as an economically saleable token. By premising the security on an economic process where the individuals are doing the work to validate transactions—when tokens are paid—a commercial system can be built where economically incentivized nodes compete to validate solutions, deanonymizing such observer systems.
In the process, a cooperative P2P system is developed to register the first transaction sent and alert the observer network to any double-spending attempts. Osipkov et al. (2007) created a system based on a cooperative peer-to-peer network designed to provide observers that combat double-spending. The problem with their approach was that the authors, again, sought to create untraceable, anonymous digital cash. One of the problems with digital cash in the past had been the problem of anonymity, and the inability of the police or the justice system to trace offenders. Consequently, the use of blinded signatures was rejected, despite it being the primary approach to creating electronic cash systems in the past.
Osipkov et al. (2007) demonstrated that a trusted third party created a single point of failure and introduced administrative and equipment expenses. Alternatively, the online detection of double-spending, while decreasing the time required to detect such an attack, increases the cost further. The approach taken by the authors was to “demand double-spending to be non-prosecutable, a natural requirement is to make e-cash completely anonymous and untraceable” (2007, p. 2). Such an approach differs from the one promoted through Bitcoin, which enables the complete traceability of all transactions, for the entire life of the system.
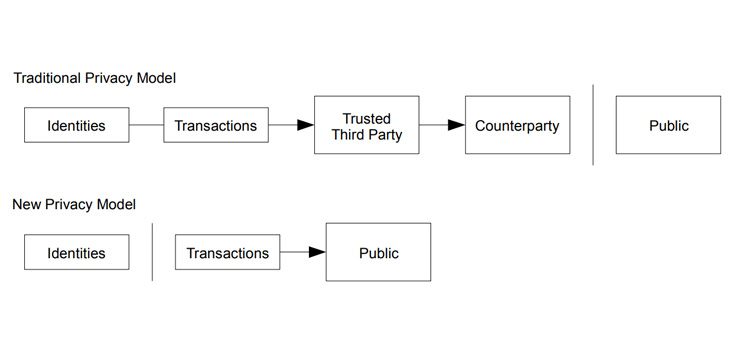
The balance sought in Bitcoin lay in creating a system that was private but not anonymous. Using disposable keys, that can be generated using the homomorphic properties of ECDSA, provides a means to incorporate identity while protecting privacy. Yet, it does not remove the necessity to develop a system that observes double-spending and reports on such attacks. Creating an observer that does not maintain control over the system, or the ability to deanonymize users by removing their privacy, allows a type of observer different from ones implemented in prior electronic cash systems. The difficulty lies in creating a means to incentivize the honest behavior of the observer.
Incentivising observers
The Bitcoin network involves the decentralized exchange of transactions between users, where Alice and Bob can negotiate, using IP-to-IP transactions, directly. In addition, the node network acts as an incentivized and commercialized observer. While Ferguson (1994, p. 296) demonstrated that such a system could be implemented, there was the requirement of a central authority, introducing cost and reducing resilience across the system. Additionally, such a trusted observer needed to be monitored to ensure that they did not compromise the general privacy of the users of the system.
Osipkov et al. (2007, p. 2) promoted using a cooperative peer-to-peer system. Yet, such a methodology cannot provide micropayments as low as a fraction of a cent. The system was also designed to provide untraceability, anonymity, and the ability to transact without money being frozen or alerts in the case of criminal activity. By contrast, Bitcoin enforces rules and can be constructed “to accept alerts from network nodes when they detect an invalid block” (Wright, 2008, p. 5). The enforcement of rules includes law and, as such, the ability to quickly alert other users—not only to ‘double-spent’ coins but also to court orders or any illicit activity, including theft.
Creating a timestamping system solves part of the problem (Haber & Stornetta, 1991). Yet, the implementation of such systems retained a centralized approach, leading to single points of failure. In addition, the timestamping and ordering system does not have a built-in payment functionality. The use of a peer-to-peer payment system is not new with Bitcoin. MojoNation and, subsequently, Mnet incorporated a payment system referred to as ‘crypto credits’ (Barr et al., 2001). Yi-chun (2007) released a peer-to-peer transaction system designed to stop double-spending without a trusted third party.
Palaka et al. (2004) extended an earlier protocol design for an anonymous peer-to-peer cryptocurrency designed for both “micro-payments (under 1 Euro) as well as macro-payments” (Daras et al., 2003, p. 2). Even peer-to-peer versions of eCash had been developed (Camenisch et al., 2007). Other authors attempted to create incentive-based systems that allowed the transfer of value in peer-to-peer systems and networks while removing double-spending (Figueiredo et al., 2004). As with all the other mentioned systems, the authors sought to remove traceability and introduce anonymity in the payment systems.
Across many forms of electronic payment that worked over peer-to-peer systems, the networks would be referred to as observers (Nambiar & Lu, 2005). Most of the observers acted without adequate incentivization (Weber, 1998). The lack of incentives leads to free-riding (Feldman & Chuang, 2005) and whitewashing (Feldman et al., 2006) in peer-to-peer systems. While researchers have promoted alternative methodologies to track and trace free riders in peer-to-peer networks (Karakaya et al., 2008), and noted how “the free rider problem poses a serious threat to their proper operation” (Karakaya et al., 2009), none of them separated the observer function from the functioning of the payment system.
Bitcoin created a decentralized payment mechanism, and allowed individuals to directly communicate IP-to-IP without an intermediary or a trusted third party. The necessity for an observer generally makes micropayments too expensive. Consequently, Bitcoin introduced a commercial, competitive node system. Such nodes provide resilience, and act to form a consensus on which transaction occurred first. The nodes validate transactions, but do not decide on but rather enforce existing rules (Wright, 2008, p. 8). This way, users can be assured that the transaction is valid and alerted if a double-spending attempt occurs.
The system incentivizes the honest activity of nodes by producing a visible audit trail and an immutable record of all activity. If a user receives a double-spent transaction, it can immediately be detected. The nodes are incentivized through the payment of tokens used in the system. The early deployment was bootstrapped with the subsidy, diminishing over time. As the subsidy diminishes, nodes are expected to collect larger numbers of transactions and harvest the fees paid in each transaction. Over time, the block size in Bitcoin is expected to increase significantly, to a point where the nodes are running in data centers (Wright in Donald, 2008).
Section 6 (Wright, 2008, p. 4) defines the process through which nodes are incentivized. Nodes support the network as observers for consideration; done through a commercial payment. The issue of a unilateral contract (Wormser, 1916) is set against a predefined issue of an absolute number of tokens. There is no ongoing trusted third party or issuer following the initial creation of tokens. Once the system has been launched, all aspects of the protocol, including the initial issuance, are set in stone, and no changes to the operation of the system are allowed.
As Wormser (1916, p. 136) demonstrated in an early treatise on unilateral contract, “a unilateral contract is created when the act is done”. In the case of a Bitcoin node, the payment is received as a combination of subsidies and fees when other nodes verify—to a depth of 100 further blocks—the block that a node has created. At this point, the creation of a unilateral contract has occurred (Pettit, 1983). A unilateral contract is accepted as soon as the offer has been completed. A system that does not create a block, or even a system that creates a block that is orphaned and thereby not accepted, does not fulfil the terms required by the network to receive payment (Smith, 1930).
A unilateral contract can be distinguished from a bilateral agreement (Fox, 1939). The offer to those using the system differs from the offer made to the nodes. Nodes are incentivized to support the network. The methodology used for distributing the coins also incentivized investment in the network. Without a central authority able to continue minting or issuing new coins, Bitcoin has a fixed supply that needs to be augmented using increasing volumes of fees. As the white paper notes, “the incentive can also be funded with transaction fees” (Wright, 2008, p. 4). This becomes the primary method for nodes to earn revenue. Through such a process, nodes are incentivized to act as “observers.”
In section 6 of the white paper, we can also see that nodes and users are separate entities. As the paper defines, the incentive for nodes to support the network is provided by the coinbase transaction that starts a new coin. The coin is owned by the creator of the block (Wright, 2008, p. 4). The creator of a block is defined as a node that finds a valid hash solution, validating a block built upon by other nodes, to a depth of 100 blocks. Eventually, the only revenue model provided to nodes lies in the collection of fees.
Nodes will also be users of the Bitcoin system and utilize the tokens. As a node is paid in Bitcoin tokens, it will be necessary for the node operator to exchange the tokens for other forms of money (Feldman & Chuang, 2005). Doing so will be required to pay bills and taxes and to maintain the business operated by the node. As such, the node is both a user of the system and an operator of the system. The incentives provided in this economic model maintain the security of Bitcoin. Other systems have been developed to monitor peer-to-peer networks, provide digital cash, and prevent double-spending using a combination of observers and exchange systems.
The distinction in Bitcoin lies in the implementation of a digital cash system based on privacy, not anonymity, and a requirement for the system to maintain traceability. The previous attempts at a peer-to-peer system have required non-economically incentivized observers, who acted altruistically. Such a model is not sustainable (Feldman & Chuang, 2005). Yet, while people have made the claim that Bitcoin is the first peer-to-peer or distributed digital cash system, it is in error (Figueiredo et al., 2004). Rather, Bitcoin is the first economically incentivized system that distributes payments through a unilateral contract-based automated system that does not require a central operator.
The reason that Bitcoin does not require a central operator is that the issue of tokens was completed at the launch of the product, and the distribution is automated. The requirements for maintaining the system are defined and set in stone. In other words, the protocol does not change. As the protocol does not change, and the incentive system is defined to operate without interaction, the system becomes the first system developed to continue operating without the continuous interaction of a third party. It is only because the system does not change, and the protocol is fixed, that it is possible. If Bitcoin, or any analogous system, could be changed and the protocol was not fixed, parties such as developers would have the right to alter the system and thereby maintain power over it. Such entities would become fiduciaries and trusted third parties.
Alternative concepts explaining ‘peer-to-peer’
Other researchers promoted the concept of censorship resistance (Waldman & Mazières, 2001). Yet, the claim was only associated with Bitcoin in 2011 and never part of the original system (Barok, 2011; Reitman, 2011). Along with making the claim, and a desire to make Bitcoin censorship-resistant, many BTC Core developers would start working to alter the protocol (Todd, 2013) and limit increases in the block size. The desire was to create a system that Endsuleit et al. (2006), Ngan et al. (2003), and Goldberg (2007) touted as being necessary to stop the encroachment of government. What each of them ignored, though, is the primary requirement of democratic systems for citizens to be engaged and politically active.
Bitcoin is not censorship-resistant in the manner often promoted, or in the way other researchers, including Dingledine and Mathewson (2006), Roussopoulos et al. (2005), or Wallach et al. (2003), espoused. Bitcoin explicitly included the ability to prune transactions from a block (Wright, 2008, p. 4). The argument that transactions may never be removed is not based on the original technology. Rather, Bitcoin’s model is one of recording all transactions and logging all data. Information can be altered or removed from the Bitcoin blockchain. But, such an action leaves a log and record of the change. For instance, if a transaction is removed following a court order, the court order itself would form a permanent aspect of the blockchain, and researchers could monitor and analyse how many court orders had been issued.
Those who say Bitcoin is the first peer-to-peer distributed system for electronic cash ever haven’t done their homework or are just outright deceitful. The simple answer is that it is very easy to determine that peer-to-peer digital cash systems existed well before the advent of Bitcoin. As explained, Osipkov et al. (2007), for instance, described how the introduction of observers can help provide action against double-spending. Such observers are peer-to-peer nodes.
Other researchers have used the term ‘peer-to-peer payments’, analogous to Bitcoin (Havinga et al., 1996). Peer-to-peer payments here are referenced in the context of providing transferability between individual users. Such a system would mirror the IP-to-IP functionality included in the original Bitcoin protocol. Yet, Havinga (1996, p. 3) also references cash as an anonymous system and not as one that is merely private. While Bitcoin utilised a system of creating new keys so a “bank, or any other party should not be able to determine whether two payments were made by the same user” (Havinga et al., 1996, p. 3), other authors have made the presumption that traceability should not be a function of money.
Bitcoin differs in being a private system that maintains a complete ability to trace transactions end-to-end. The ability of Bitcoin to maintain immutability lies in its logging feature and not in the so-called ‘censorship resistance’ functionality that some people promote (Barok, 2011). The “desire of regulators and intermediaries to be able to trace any transaction in the economy”, which contemporary cryptocurrency and digital money researchers (Havinga et al., 1996, p. 3) have noted, is of valid concern. The balance must be maintained between privacy and the ability to trace money and protect the public from crime.
Bitcoin balances such dichotomy by achieving privacy through scale. While every transaction retains full traceability, the cost of monitoring all users globally is prohibitive. Moreover, suppose users maintain separate keys for every transaction and firewall their identities. In that case, it becomes infeasible for people to randomly determine other people’s identities or even to link identities. The creation of filters, controls, and software can simplify the issue and allow payments that are not joint and hence do not expose the identity of the user or link transactions (Wright, 2008).
Introducing resilience
A trusted third party or central authority creates a single point of failure. The decentralization of Bitcoin is achieved through the interaction of individuals across the network, which is primarily facilitated through direct IP-to-IP communications. The ability of parties like Alice and Bob to directly communicate, without going through a node, is essential if the system is to maintain decentralization. Additionally, a peer-to-peer observer network is more resilient than a trusted central party. Such resilience means it is more difficult to attack the Bitcoin network (Palaka et al., 2004). The ability to withstand attacks and provide the fair provision of services forms one of the core aspects of Bitcoin.
Nodes do not set the rules within the Bitcoin protocol. They were fixed when the protocol was launched. Rather, nodes enforce the rules. The ability to alert the network and act within a legal framework is a key requirement for any system, including Bitcoin. Other entities have looked at coin tracing as a system that can be conducted through trusted third parties (Hou & Tan, 2004) or a self-deanonymizing protocol. Neither option is adequate. Instead, Bitcoin creates a set of independent commercial nodes that act as observers of the network. The resilience of the system is achieved through a distributed set of competing operators.
Each node acts independently in a peer-to-peer timestamping network (Voulgaris et al., 2005). In such a process, the nodes that fail or are attacked successfully make it more economically viable for other nodes to join. The fees will be distributed between a small number of nodes if one disappears. Consequently, the profitability of all remaining nodes increases significantly. The process incentivizes new nodes to join, filling the gap left by the departing node. The continuing incentivization structure ensures that the peer-to-peer observer network is maintained and operates openly, with auditability.
Conclusion
Bitcoin solved the double-spending problem robustly and securely. It did so by forming a peer-to-peer observer network that is economically incentivized. While other networks have existed to provide observer capabilities (Hou & Tan, 2004), and peer-to-peer digital cash was proposed multiple times (Daras et al., 2003; Figueiredo et al., 2004; Palaka et al., 2004), all sought to form an electronic cash system that was untraceable and anonymous. Bitcoin is not the first peer-to-peer digital cash system. Likewise, Bitcoin is not the first decentralized digital cash system. Bitcoin is the first system to use a peer-to-peer network created using economic incentives, and, importantly, one that maintains complete traceability—using privacy instead of anonymity.
This article was lightly edited for clarity purposes.
References
Aura, T., Nikander, P., & Leiwo, J. (2001). DOS-Resistant Authentication with Client Puzzles. In B. Christianson, J. A. Malcolm, B. Crispo, & M. Roe (Eds.), Security Protocols (pp. 170–177). Springer. https://doi.org/10.1007/3-540-44810-1_22
Back, A. (2002). Hashcash-amortizable publicly auditable cost functions. Available HTTP: http://www.hashcash.org/papers/amortizable.pdf
Barok, D. (2011). Bitcoin: Censorship-resistant currency and domain name system to the people. Piet Zwart Inst.
Barr, K., Batten, C., Saraf, A., & Trepetin, S. (2001). pStore: A Secure Distributed Backup System. Technischer Bericht, LCS, Massachusetts Institute of Technology.
Brands, S. (1994). Untraceable Off-line Cash in Wallet with Observers. In D. R. Stinson (Ed.), Advances in Cryptology—CRYPTO’ 93 (pp. 302–318). Springer. https://doi.org/10.1007/3-540-48329-2_26
Camenisch, J., Lysyanskaya, A., & Meyerovich, M. (2007). Endorsed E-Cash. 2007 IEEE Symposium on Security and Privacy (SP ’07), 101–115. https://doi.org/10.1109/SP.2007.15
Camenisch, J., Maurer, U., & Stadler, M. (1997). Digital payment systems with passive anonymity-revoking trustees. Journal of Computer Security, 5(1), 69–89. https://doi.org/10.3233/JCS-1997-5104
Daras, P., Palaka, D., Giagourta, V., & Bechtsis, D. (2003). A novel peer-to-peer payment protocol. The IEEE Region 8 EUROCON 2003. Computer as a Tool., 1, 2–6 vol.1. https://doi.org/10.1109/EURCON.2003.1247967
Dingledine, R., & Mathewson, N. (2006). Design of a blocking-resistant anonymity system. Technical report, The Tor Project. https://r.jordan.im/download/technology/Design%20of%20a%20blocking-resistant%20anonymity%20system.pdf
Donald, J. A. (2008, November 3). Bitcoin P2P e-cash paper [Metzdowd.com.]. Bitcoin P2P E-Cash Paper. https://www.metzdowd.com/pipermail/cryptography/2008-November/014819.html
Endsuleit, R., & Mie, T. (2006). Censorship-resistant and anonymous P2P filesharing. First International Conference on Availability, Reliability and Security (ARES’06), 7–65. https://doi.org/10.1109/ARES.2006.41
Feldman, M., & Chuang, J. (2005). Overcoming free-riding behavior in peer-to-peer systems. ACM SIGecom Exchanges, 5(4), 41–50. https://doi.org/10.1145/1120717.1120723
Feldman, M., Papadimitriou, C., Chuang, J., & Stoica, I. (2006). Free-riding and whitewashing in peer-to-peer systems. IEEE Journal on Selected Areas in Communications, 24(5), 1010–1019. https://doi.org/10.1109/JSAC.2006.872882
Ferguson, N. (1994). Extensions of Single-term Coins. In D. R. Stinson (Ed.), Advances in Cryptology—CRYPTO’ 93 (pp. 292–301). Springer. https://doi.org/10.1007/3-540-48329-2_25
Figueiredo, D. R., Shapiro, J. K., & Towsley, D. (2004). Payment-based incentives for anonymous peer-to-peer systems. Computer Science Department, University of Massachusetts. ftp://128.119.245.9/pub/Anon_Incentive_04-62.pdf
Fox, J. H. Jr. (1939). Contracts—Offer of Unilateral Contract Distinguished from Unilateral and Bilateral Contract—Effect of Beginning Acceptance of Offer of Unilateral Contract Recent Decision. Mississippi Law Journal, 12(3), 374–377.
Goldberg, I. (2007). Privacy-Enhancing Technologies for the Internet III: Ten Years Later. In Digital Privacy (pp. 25–40). Auerbach Publications. https://doi.org/10.1201/9781420052183-7
Haber, S., & Stornetta, W. S. (1991). How to Time-Stamp a Digital Document. In A. J. Menezes & S. A. Vanstone (Eds.), Advances in Cryptology-CRYPTO’ 90 (pp. 437–455). Springer. https://doi.org/10.1007/3-540-38424-3_32
Havinga, P. J. M., Smit, G. J. M., & Helme, A. (1996). SURVEY OF ELECTRONIC PAYMENT METHODS AND SYSTEMS. 8.
Hird, S. (2002). Technical solutions for controlling spam. Proceedings of AUUG2002. https://books.google.co.uk/books?hl=en&lr=&id=CPXLz_zkhgwC&oi=fnd&pg=PA205&dq=Technical+Solutions+for+Controlling+Spam.+&ots=rN9Q3Uaoqm&sig=WOsugqcrnrRbPeiBJ_goUjkwrr0#v=onepage&q=Technical%20Solutions%20for%20Controlling%20Spam.&f=false
Hoepman, J. (2006). Distributed Double Spending Prevention. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.183.6025
Hoepman, J.-H. (2010). Distributed Double Spending Prevention. In B. Christianson, B. Crispo, J. A. Malcolm, & M. Roe (Eds.), Security Protocols (pp. 152–165). Springer. https://doi.org/10.1007/978-3-642-17773-6_19
Hou, X., & Tan, C. H. (2004). Fair traceable off-line electronic cash in wallets with observers. The 6th International Conference on Advanced Communication Technology, 2004., 2, 595–599. https://doi.org/10.1109/ICACT.2004.1292939
Karakaya, M., Körpeoğlu, İ., & Ulusoy, Ö. (2008). Counteracting free riding in Peer-to-Peer networks. Computer Networks, 52(3), 675–694. https://doi.org/10.1016/j.comnet.2007.11.002
Karakaya, M., Korpeoglu, I., & Ulusoy, Ö. (2009). Free Riding in Peer-to-Peer Networks. IEEE Internet Computing, 13(2), 92–98. https://doi.org/10.1109/MIC.2009.33
Lee, H. J., Choi, M. S., & Rhee, C. S. (2003). Traceability of double spending in secure electronic cash system. 2003 International Conference on Computer Networks and Mobile Computing, 2003. ICCNMC 2003., 330–333. https://doi.org/10.1109/ICCNMC.2003.1243063
Nambiar, S., & Lu, C.-T. (2005). M-Payment Solutions and M-Commerce Fraud Management [Chapter]. Advances in Security and Payment Methods for Mobile Commerce; IGI Global. https://doi.org/10.4018/978-1-59140-345-6.ch009
Ngan, T.-W. “Johnny”, Wallach, D. S., & Druschel, P. (2003). Enforcing Fair Sharing of Peer-to-Peer Resources. In M. F. Kaashoek & I. Stoica (Eds.), Peer-to-Peer Systems II (pp. 149–159). Springer. https://doi.org/10.1007/978-3-540-45172-3_14
Osipkov, I., Vasserman, E. Y., Hopper, N., & Kim, Y. (2007). Combating Double-Spending Using Cooperative P2P Systems. 27th International Conference on Distributed Computing Systems (ICDCS ’07), 41–41. https://doi.org/10.1109/ICDCS.2007.91
Palaka, D., Daras, P., Petridis, K., & Strintzis, M. (2004). A Novel Peer-to-Peer Payment System. (p. 250).
Pettit, M. Jr. (1983). Modern Unilateral Contracts. Boston University Law Review, 63(3), 551–596.
Reitman, R. (2011). Bitcoin—A Step Toward Censorship-Resistant Digital Currency. In Electronic Frontier Foundation. https://www.eff.org/deeplinks/2011/01/bitcoin-step-toward-censorship-resistant
Roussopoulos, M., Baker, M., Rosenthal, D. S. H., Giuli, T. J., Maniatis, P., & Mogul, J. (2005). 2 P2P or Not 2 P2P? In G. M. Voelker & S. Shenker (Eds.), Peer-to-Peer Systems III (pp. 33–43). Springer. https://doi.org/10.1007/978-3-540-30183-7_4
Smith, W. A. (1930). Acceptance of Offer for Unilateral Contract—Necessity of Notice to Offeror Editorial Notes. University of Cincinnati Law Review, 4(1), 57–85.
Todd, P. (2013, March 7). [Bitcoin-development] Large-blocks and censorship. https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2013-March/002199.html
Voulgaris, S., Jelasity, M., & van Steen, M. (2005). A Robust and Scalable Peer-to-Peer Gossiping Protocol. In G. Moro, C. Sartori, & M. P. Singh (Eds.), Agents and Peer-to-Peer Computing (pp. 47–58). Springer. https://doi.org/10.1007/978-3-540-25840-7_6
Waldman, M., & Mazières, D. (2001). Tangler: A censorship-resistant publishing system based on document entanglements. Proceedings of the 8th ACM Conference on Computer and Communications Security, 126–135. https://doi.org/10.1145/501983.502002
Wallach, D. S. (2003). A Survey of Peer-to-Peer Security Issues. In M. Okada, B. C. Pierce, A. Scedrov, H. Tokuda, & A. Yonezawa (Eds.), Software Security—Theories and Systems (pp. 42–57). Springer. https://doi.org/10.1007/3-540-36532-X_4
Weber, R. (1998). Chablis—Market Analysis of Digital Payment Systems. https://mediatum.ub.tum.de/1094458
Wormser, I. M. (1916). True Conception of Unilateral Contracts. Yale Law Journal, 26(2), 136–142.
Wright, C. S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. SSRN Electronic Journal. https://doi.org/10.2139/ssrn.3440802
Wright, C. S., & Savanah, S. (2022). Determining a common secret for the secure exchange of information and hierarchical, deterministic cryptographic keys (United States Patent No. US11349645B2). https://patents.google.com/patent/US11349645B2/en?assignee=nchain&before=priority:20160301
Yi-chun, L. (2007). An Optimistic Fair Peer-to-Peer Payment System. 2007 International Conference on Management Science and Engineering, 228–233. https://doi.org/10.1109/ICMSE.2007.4421852
Watch: The BSV Global Blockchain Convention presentation, Blockchain for Data Integrity & Business Process Management

 03-03-2026
03-03-2026