|
Getting your Trinity Audio player ready...
|
This post was first published on Medium.
Oracles are indispensable for smart contracts to access external real-world data. Data fidelity is paramount for these smart contracts to function. One way to increase data fidelity is to require an oracle to deposit some collateral against the data they provide. If the oracle misbehaves and provides fraudulent data, he forfeits the collateral (called slashing). If the collateral is escrowed at a third party, we merely shift the trust issue from the oracle to the third party, whom we entrust to judiciously monitor and punish fraud.
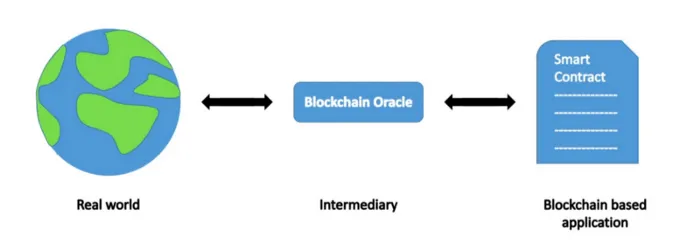
Our innovation in this article is to lock up the collateral directly into a smart contract as a public bounty and anyone can collect it as long as he can find proof of fraud, without any trusted third party. By making sure any dishonest behavior will be caught and penalized financially, we incentivize oracles to behave honestly and thus make smart contracts depending on them more secure. We illustrate using Sensible oracles as an example.
Sensible contracts and oracles

Sensible contract is a way to develop and organize Bitcoin smart contracts. It allows a contract to backtrack to its issuance transaction, as well as identify neighboring contracts in the inputs of the same transaction. It relies on a specific type of oracles to verify data integrity off chain, called Signature Service. Particularly, a Sensible oracle signs the following tuple:
(txid, index, satoshis, scriptHash)
Basically, it authenticates the index-th output in a transaction with txid has that many satoshis in it and its script hashes to scriptHash.
Slashing contract
We notice that all information in the tuple is publicly available and everyone can independently check. If we can find a transaction with the given txid but contains a different satoshi amount or script at the indexed output, we have found proof of fraud and can confistigate the oracle’s collateral. To achieve this, an oracle locks up collateral into the following contract:
Contract SlashSensibleOracle
Line 20 ensure the data is indeed signed by a Sensible oracle. Line 23 parses the data into a desired format. Line 26 validates the transaction containing the fraud proof matches the txid. After retrieving the specified output from the transaction at Line 29, Line 32 verifies the oracle has cheated by signing erroneous amount or script.
Anyone can call the contract and redeem the oracle’s collateral if he can find fraud.
Extension
A Sensible oracle can sign another tuple:
(txid, index, satoshis, scriptHash, spendByTxID)
It verifies not only the output identified by the pair (txid, index) has the specified satoshi amount and script, but also it is spent by a transaction with txid spendByTxID. To detect such a fraud, we can find a transaction with a different txid spending it, in addition to what is done in contract SlashSensibleOracle. We can use the technique, Access Blockchain Data from Bitcoin Smart Contracts Without Oracles, to validate the transaction is indeed on chain.
Summary
We have only showed how to use smart contract to slash cheating Sensible oracles. It is applicable to any oracle where evidence of fraud can be verified in a smart contract.
For example, an oracle can conduct pure/stateless but complex calculations and sign the results. A smart contract can thus import the signed result and get the result without rerunning all the expensive calculations. At the same time, whenever the oracle cheats, he loses his collateral locked in a contract, which simply calculates the different but correct result.
Watch: CoinGeek New York presentation, Smart Contracts & Computation on Bitcoin

 06-30-2025
06-30-2025