|
Getting your Trinity Audio player ready...
|
What is a network “node” in basic IT terms? TechTarget describes it as, “a point of intersection/connection within a data communication network. In an environment where all devices are accessible through the network, these devices are all considered nodes. The individual definition of each node depends on the type of network it refers to.”
Interesting that the definition includes the caveat that the “node” can be defined by the creator of the network based on the “type” of network on which it operates. Curiously, Satoshi Nakamoto uses the word “honest” 16 times in the Bitcoin white paper to describe security and attack vectors. However, most of the times he uses the word, it’s directly before the word “node;” which occurs 38 times in the white paper. So what does a node do?
Ok, but what about “Honest Nodes?”
Bitcoin is a consensus network designed to solve the Byzantine Generals Problem with proof of work. If that sounds insane, sorry. Fortunately, it’s not as crazy as it sounds. Picture five generals surrounding a city under siege in the era of ancient Byzantium. They can’t talk directly, so they have to send riders or some other low-tech means of communication between each other. When the message arrives, they can’t know if it was tampered with, so they have a fundamental trust problem with their communications.
The solution to solving this is proof of work (and a few other things that Bitcoin solves with a public network) which is essentially to add a side-quest to the rider. If the rider can solve a complicated puzzle that only a Byzantine would know, it is more likely that he is an honest rider. Or, at the very least, if he is dishonest, he will struggle to perform as well as the other honest riders among the other generals. This acts as a filter for bad actors, and works probabilistically often enough that it functions near perfection in practical application.
But here’s the issue with the allegory: to a pure technocrat (like a BTC small blocker), they operate under the assumption that the generals are dishonest or that they become less honest as they gain the ability to generate more proof of work over time. This leads them to want newer “generals” or nodes on the network which don’t generate proof of work because, for some reason, they have decided that lots and lots of altruism across communication channels makes them more robust. That’s actually insane.
Something I realized a few years ago is that Byzantine Generals know each other. In order to be a general in the Byzantine military, they would have come up together. They would have protected each others’ backs in battle, and likely saved each others’ lives both directly and indirectly for their entire careers. The generals are very unlikely to be dishonest. They can trust each other. They have earned that trust. The overwhelming majority of their trust problem is with the communication channel itself. If they had direct peer connections and gigabit ethernet, they wouldn’t have a problem at all. Why? Because they are “honest nodes.”
Under attack, or under pressure, or amid a battle, consensus about the truth is the job of an “honest node.” The rest of bitcoin’s functions can be managed simply by “nodes.”
In realizing that Byzantine Generals are people, I realized too that while “nodes” are computers, “honest nodes” are actually people. A node will do whatever it is programmed to do. It cannot choose to be honest or dishonest any more than a car can cause an accident, or a gun can shoot a person. Curiously enough, people seem to agree that a malicious or an attacker node is definitely run by a human, but why not an honest node?!
Only. Humans. Act.
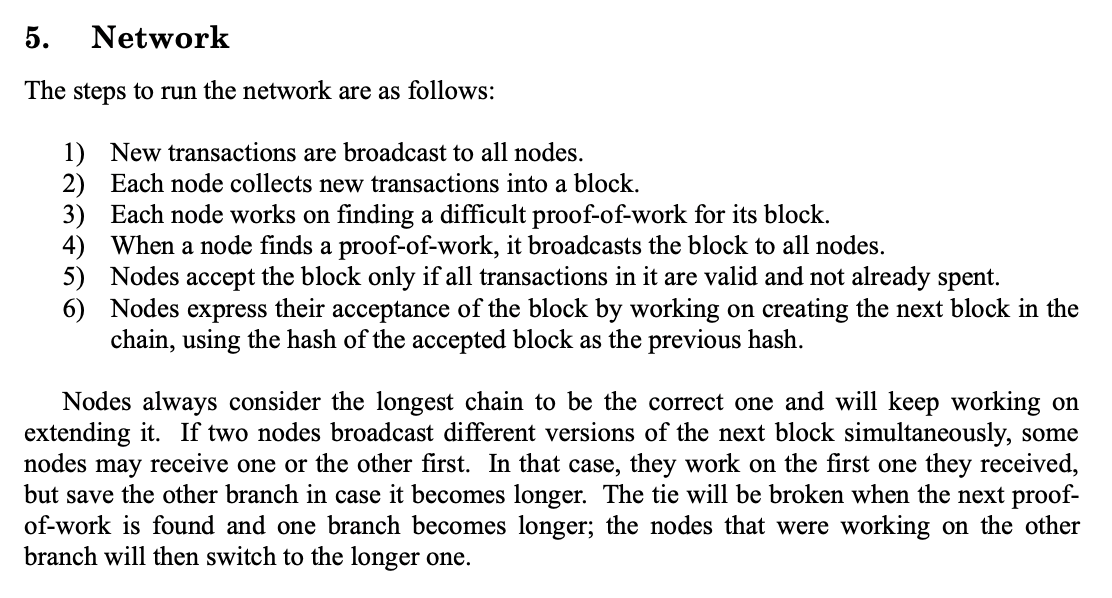
Satoshi did not trust humans that vote for the truth with their IP address rather than with their proof of work, and described the problem of a sybil attack in Bitcoin while assuming that the network would persist even under attack as long as “honest nodes” control a majority of CPU.
But what if Bitcoin used IP addresses to vote, and the majority of CPU was not controlled by honest nodes? Well, UASF is exactly that. It’s a sybil attack subverting consensus, and a majority of nodes follow the dishonest signal of an IP address voting in a flag day with no proof of work. Hence the Bitcoin Civil War and emergence of BSV as the chain with honest nodes.
So act, human!
Under attack, the operator of a node becomes a crucial part of consensus. It’s these moments when the network sees why the node operator has been spending incredible money to secure the network on cruise control because they care about the integrity of the network’s data and the reputation of their own business/node. But on a day to day basis, nodes secure their network according to a set of rules defined by the protocol.
This is why honest nodes split the network to retain the UTXO set from the IP/sybil attack, and it’s why BSV exists to solve the Byzantine Generals problem in the way described by Satoshi Nakamoto.
Here’s where big blockers and small blockers diverge in their worldview:
- A small blocker believes in a technocratic perfection expressed in code so that the network is flawless and requires no human intervention under the assumption that all humans are corrupt and that governance by machines is desirable in all circumstances. Code is law, and machines enforce justice perfectly.
- Big blockers believe that Bitcoin was designed as a flexible, extensible business tool that requires human interaction in order to achieve something truly valuable. Therefore, governance by machines is great as long as humans remain vigilant in managing them, but when things get crazy, humans act to secure the system and enforce rules.

In closing summary, a Bitcoin node is a computer that contributes proof of work and validates block by building blocks. But an honest node and an attacker node are both steered by human action, and the Bitcoin white paper assumes this human action in the protocol! So we should embrace it, and perhaps run a Bitcoin node, honestly.
Just something to think about.
Recommended for you
The views expressed in this article are those of the author and do not necessarily reflect the position of CoinGeek.

 03-06-2026
03-06-2026 




