|
Getting your Trinity Audio player ready...
|
This post was first published on Medium.
Everything on a blockchain is publicly accessible. This gives rise to privacy concerns, when working with sensitive data. To ensure data on chain remains confidential and secure, we employ a technique called homomorphic encryption (HE). It allows computations to be performed on encrypted data without decrypting it, opening up new possibilities for privacy-preserving computations on the blockchain. We have developed an example implementation of the ElGamal encryption scheme in sCrypt and discussed its potential use cases.
Homomorphic encryption
Homomorphic encryption is a magical form of encryption that allows computation on encrypted data without the need for decryption. In other words, it enables certain computation to be performed on encrypted data directly, preserving its confidentiality. This advanced encryption technique has significant implications for secure data processing and privacy, especially in the context of cloud computing and machine learning.
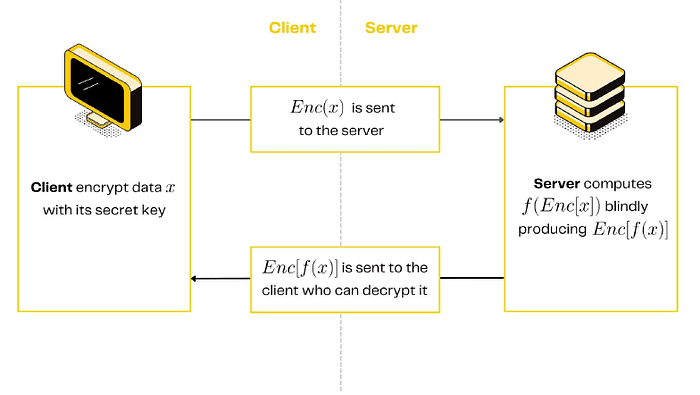
Let’s say, a client wants to compute a function f on data x and she wants to run the computation on a remote server, since it is resource demanding. However, she does not want the server to know x, because it is deemed sensitive. How could the server compute over x, without knowing it?
Thanks to homomorphic encryption, she would encrypt x and send the ciphertext to the server, which can compute on it without knowing x. Upon completion, the server sends the encrypted result back to her, which she can decrypt and get f(x).
In the context of blockchain, miners act as the server.
In a homomorphic encryption, the following homomorphic relationships hold on ciphertexts:
- addition: Encrypt(x) + Encrypt(y) = Encrypt(x + y)
- multiplication: Encrypt(x) * Encrypt(y) = Encrypt(x * y)
Accordingly, there are different types of homomorphic encryption:
- partially homomorphic: supports addition or multiplication, but not both
- fully homomorphic: supports both addition and multiplication
Fully Homomorphic Encryption (FHE) has long been considered as the holy grail of cryptography. It allows arbitrary computations to be performed on encrypted data, as any program can be represented as a circuit of additions and multiplications.
In the context of blockchain and smart contract development, partially homomorphic encryption is currently more practical, as fully homomorphic encryption is currently more computationally intensive, even though recent breakthroughs are starting to making it possible.
ElGamal Encryption
The most commonly used partially homomorphic encryption schemes are the ElGamal encryption scheme and the Paillier encryption scheme. Both allow for the addition of encrypted numbers and also the multiplication of an encrypted number by a plaintext scalar.
We have implemented the ElGamal encryption below, extending our previous ElGamal implementation. We use it in a toy smart contract that tracks the business expenses of employees:
- Each day, employees submit their expenses to the contract. They encrypt it before sending it to the contract, as they don’t want other employees to know their expenses.
- The contract adds the expense, encrypted, to the current total expense, also encrypted.
- Monthly, the company accesses the total expense by decrypting the encrypted total expense from the contract locally.
Other more realistic use cases include:
- Blind Auctions: place bids on items without disclosing the bid amount or the identity of the winning bidder.
- Confidential Voting: deter bribery and blackmailing by keeping votes private, while ensuring they are counted correctly.
We have also implemented Paillier encryption.
Compare to Zero-Knowledge Proof
An alternative technique to preserve privacy is Zero-Knowledge Proof (ZKP), which we have covered extensively.
There are several major differences:
- data availability: HE keeps data on chain encrypted, while ZKP may keep data off chain.
- composability: in HE, after data in encrypted and put on chain in one application, it can be combined and integrated to another application, due to the homomorphic property. In ZKP, it is harder to do so.
In practice, HE and ZKP are often used together, where ZKP ensures the plaintext to HE is known and well-formed.
Conclusion
Safeguarding data privacy is essential in blockchain and smart contract systems, demanding developers to be mindful of the sensitivity of the data they manage. Utilizing methods such as homomorphic encryption, sCrypt developers can elevate the confidentiality and safety of their decentralized applications. This approach unlocks fresh opportunities for conducting secure computations on the blockchain while preserving user privacy.
Watch: Sentinel Node partners with IBM to Improve Cybersecurity

 07-05-2025
07-05-2025 




