|
Getting your Trinity Audio player ready...
|
This post originally appeared on Medium as part of a three-part series on Bitcoin smart contracts, and we republished with permission from Xiaohui Liu. Read part 1 here and part 2 here.
We introduce a generic approach to skip on-chain computation in Bitcoin smart contracts, while ensuring security in the presence of malicious parties. In this approach, honest contracting parties can reach agreements peer to peer off chain and opportunistically decide to short-circuit complex computational alternative.
Outsource example
Alice asks Bob to compute an input/witness x which makes function f(x) return true. For example, f can be a hash puzzle, a solution to a Sudoku puzzle or a Travelling Salesman Problem (TSP). If Bob can provide x, he is paid in Tx1 as shown below. Otherwise, Alice can cancel and get her fund back in Tx2 after time t, which is pre-signed by Bob. This is dual to Timed Commitment Scheme (TCS) we introduced before, in the sense that Bob has to respond in time, not Alice.
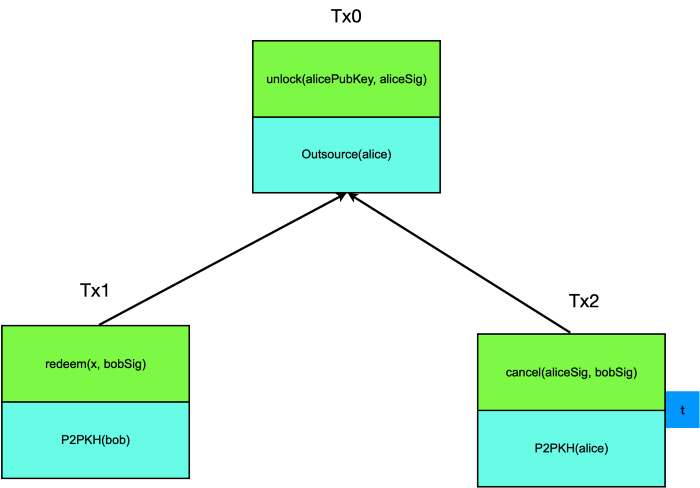
Outsource with cooperation
Now let us modify the above contract/protocol slightly. Bob, instead of redeeming Alice’s fund by broadcasting Tx1, shares his witness x with Alice directly. Alice can validate it off chain and ensure it is expected (i.e., f(x) evaluates to true). Afterwards, she has two choices:
- She refuses to sign even though she obtains Bob’s secret x.
- She signs a new transaction Tx3 without timelock and sends it to Bob, who signs and broadcasts it to take the fund, as shown below. This is possible because the onchain part of the contract, in the form of Bitcoin Script Outsource(alice), can be cancelled as long as Alice and Bob both sign, regardless of timelock. Outsource(alice), having identical code structure as TCS, simply does not check locktime of the transaction spending the UTXO it resides in.
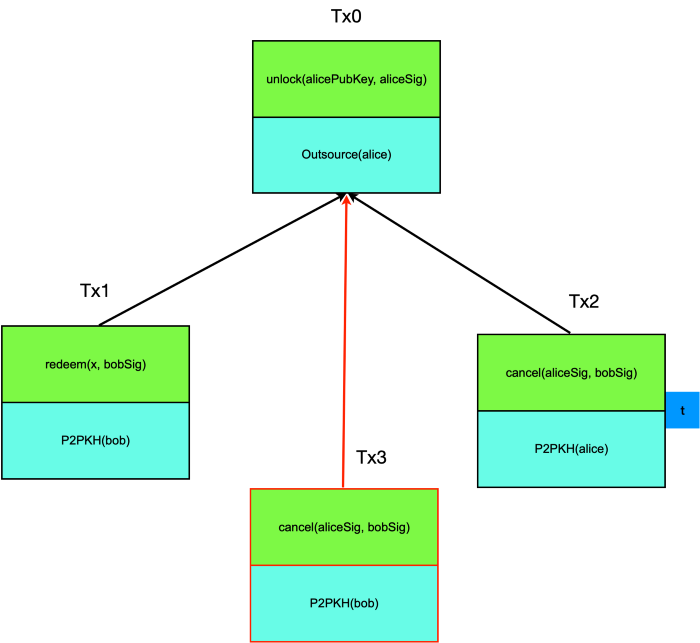
In choice 1, Bob can still create Tx1 and redeem Alice’s fund. Alice cannot cheat and does not gain anything.
In choice 2, Alice chooses to be honest and can enjoy significant benefits.
Privacy
Often, Alice does not want x to be public. Maybe it is the preimage in a hash puzzle, acting as token to access her rental car, or the answer to the TSP’s problem is secret of her logistics company’s route. x would be exposed in Tx1 and be shielded in Tx3.
Efficiency
f can be a computationally intensive function, which has to be evaluated by all miners if Tx1 is used. If Tx3 is used, f is not evaluated by miners at all, since a contract function is only called when it is used in the spending transaction to unlock. Instead, only two signatures have to be checked, which can be many orders of magnitude smaller and independent of the complexity of f.
From Alice’s perspective, she is incentivized to act honestly and choose 2 to gain privacy. Her honesty also offloads heavy computation off chain, reducing overall tasks on the Bitcoin network.
Generalization
The idea is applicable to all types of smart contracts where multiple parties can reach mutual agreements off chain, thus avoid heavy on-chain computation and gain additional privacy by following the contract/protocol honestly. This is achieved with no loss of security and fairness, even if some parties try to cheat. It is expected to gain wide adoption in practice.

 02-25-2026
02-25-2026 




