|
Getting your Trinity Audio player ready...
|
One of the most underappreciated technological developments that have been vastly overlooked since the advent of blockchain technology is that of threshold signatures. As a mostly academic technology, obscure to anyone outside of the cryptography community, it has been around since the mid-90s, with Rosario Gennaro publishing the first threshold DSS (digital signature standard) in 1996. In this paper he outlined how a ECDSA signature could be produced without ever having a private key, but instead through the combination of a certain ‘threshold’ of key shares (parts[1] of a key). This combination of required shares through some multiparty computational process is then able to generate a valid signature, which by itself is indecipherable from a standard signature generated by a single party with possession of an actual private key.
This stands to be one of the most underutilized, but revolutionary technologies that could be used in the digital asset space, due to its ability to do mostly everything that multi-signature techniques can presently do but have some significant additional security benefits. So much so in fact, that even NIST has started looking into the tech for its practical applications and uses.
To illustrate how this tech can benefit businesses, let’s step into the shoes of a fictitious cryptocurrency exchange, called BitExchange. BitExchange allows their customers to trade digital currencies on their platform, and act as a custodial exchange, meaning that while their customers assets are under their control, they guarantee their deposits, and are entrusted with keeping their assets safe.
In order to do this, they employ an unofficial industry standard of running a hot wallet/cold wallet system, in which their servers which process client withdrawal/deposit requests use hot wallets, meaning they are connected to the internet and are the most exposed to potential hacking attacks. The cold wallets are where the operating funds of the day are moved back to for safe keeping, usually offline storage devices.
The business of managing the movement of funds between cold and hot wallets to facilitate the flow of daily client deposits and withdrawals is a big part of the operational tasks that an exchange must undertake, which is a high risk, high security concern. Keep in mind, any access to this process must be closely monitored as exchange hacks are usually inside jobs, with attack vectors relying on social engineering of employee accounts within the operations department. Also, complicating the process, is the fact that different blockchains have different confirmation times and APIs. While a move of BSV funds from a cold wallet to the hot wallet servers may take some fractions of a second, some other chains may take longer or cost more, especially when the network load on the particular blockchain is high.
This necessitates different processes to be put in place for each and every blockchain token that the exchange offers trading on, which is a large and growing operational cost, as well as risk. This risk is also what we in the industry call “wrong-way-risk,” in that the risk increases in exactly the situation where you want it least to, in this case, when the markets experience more volatility, this is exactly when the volumes of withdrawals and deposits will spike, causing a backup due to blockchain congestion and thus causing withdrawals and deposits to take longer.
To manage this problem, BitExchange constantly monitors the levels of their hot wallets, and has a process which moves funds over from cold wallets when it gets low. Additionally, when deposits come into the exchange, there is a process that immediately moves the funds and splits it into smaller coin amounts (for Bitcoin-like UTXO blockchains) so that regular moves from the cold wallet can be done in a relatively regular manner.
Finally, to ensure security through all this coin shuffling, BitExchange uses a multi-signature system which requires 2 out of 3 signatures (of 2 different servers) in order to make any changes. Because each one of these internal transfers are actual blockchain transactions, the exchange itself needs to pay transaction costs to the blockchain miners, and this whole process is subject to slowdown risk when the blockchain volume spikes (at least for non-BSV blockchains which have a model in which fees increase when the network is overloaded by volume increases, such as BTC and ETH). As such the exchange may end up paying a high cost in fees just to execute all of these internal wallet ’housekeeping’ transactions. This is just the currently accepted cost of operating an exchange.
Now imagine, you can offer the COO of said exchange a solution, which would allow them to maintain the security and separation of hot wallet/cold wallets, but without having to actually move their assets from one address to the next? This means that any internal move from a cold wallet to hot wallet or vice versa will not actually be a blockchain transaction, which means 1) no blockchain fees incurred 2) no slowdown in transaction processing when the blockchain is experiencing volume congestion lag.
Also, all of this can be done, while maintaining the security model of multi-signature wallets! How? Well of course you know, because that is the title of this article, via threshold signatures! So why then, has the entire industry only just recently started looking at threshold signatures[2]? Well, it may be that in cryptography and cybersecurity, you can’t really trust new technology.
Counter-intuitively, the older the technology is, the generally more secure it is, due to the fact that the public domain has had more time trying to attack and break the protocol. New protocols are most likely to have undiscovered exploits or attack vectors that the designers did not foresee. And unlike the world of real physical locks, once a crypto-graphic protocol has been publicly broken or a vulnerability exposed, it is widely dropped from common use. So the longer something has been in common use without any successful attacks exposed, the safer it objectively is.
This partially explains why although thresholds signature technology has been around for almost 20 years, it still isn’t widely adopted. Secondly, before the advent of bitcoin and blockchains, there simply weren’t many practical use cases where threshold signatures could be used, thanks to bitcoin and digital assets being valuable, cryptographic protocols (and thus techniques like threshold signatures) have finally found a market. Lastly, when compared to common multi-signature protocols, threshold signatures have always been a bit more finicky.
For instance, there was always the need for a lot of communication rounds between the signing participants to generate a signature, and they also had some quirky restrictions[3]. This made it a bit clunky to implement, and coupled with the fact that the simplest use case of a 2-of-3 multi-signature scheme, which means two out of a possible three participants must coordinate to generate a signature, could not be implemented in a fashion that would be able to produce a signature in reasonable time[4], exchanges likely opted for the simpler, tried and tested multi-sig tech instead.
clunky to implement, and coupled with the fact that the simplest use case of a 2-of-3 multi-signature scheme, which means two out of a possible three participants must coordinate to generate a signature, could not be implemented in a fashion that would be able to produce a signature in reasonable time[4], exchanges likely opted for the simpler, tried and tested multi-sig tech instead.
But thanks to the recent interest in threshold signatures, (likely brought about by a desire for digital asset companies to shore up their custodial wallet systems in the light of an increasing amount of interest in the digital assets space; this is now pushing the AUM of companies beyond what their lawyers feel comfortable holding), the number of breakthroughs in the technology have literally doubled in the last two years. While it took 22 years to produce seven significant developments, in the last two years alone has seen an addition of 10 new innovations in the technology.
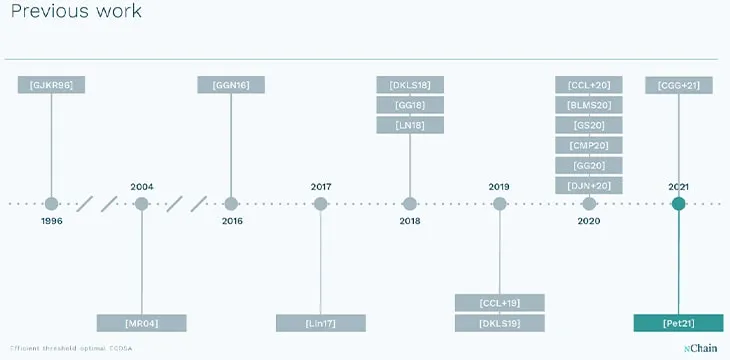
This tech innovation is being led by nChain AG in Switzerland, with one of their latest patent filings Pet21 by Dr. Michaella Pettit is an increased efficiency method of generating threshold signatures, which when compared to other competing methods, shows a dramatic increase in speed and usability. Not only does an efficient method allow for consistently fast signature generation times regardless of threshold size (number of required share participants), but also it allows for the most common 2-of-3 signature threshold scheme. This is generally the most common setup for exchange hot wallet/cold wallet systems, with two of the participants being the exchange hot wallet system and the operational administrative system, with the third being a backup or recovery key.
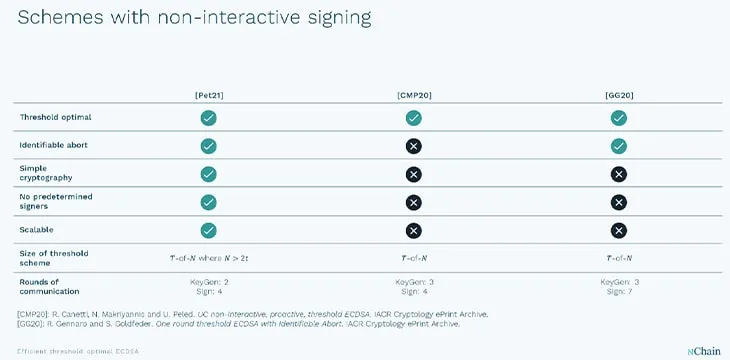
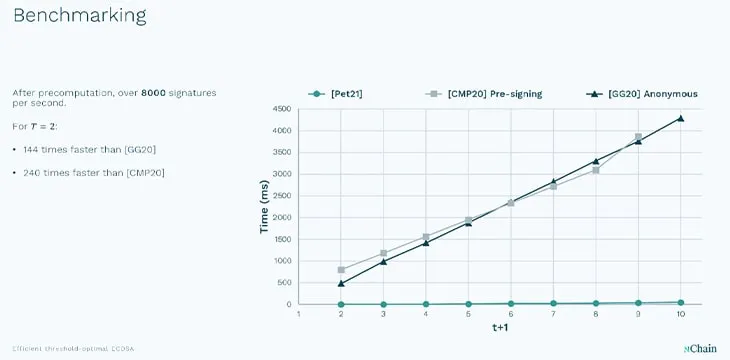
With an efficient threshold system, instead of an exchange moving their assets around on-chain, bearing the cost of complexity and the on-chain blockchain fees, they could just shift the threshold shares of their servers and have the benefit of multi-sig in terms of access control, etc., being able to shift funds, among other benefits5. Using this scheme any cold wallet can be turned into a hot wallet and vice versa, without actually moving funds, or paying any fees.
I hope you now can start to appreciate how useful this technology will be and how it stands to revolutionize and improve the security models of companies working with digital assets. Coinbase, the largest U.S. based exchange has already started looking into doing exactly this, so threshold signatures is likely set to be the hot technological advancement of the 2022 in the crypto industry.
/jerry
***
Notes:
[1] Actually not simple parts, because the private key never actually existed, but portions of data which when combined through a multiparty computational process, can be used effectively as a private key in order to produce a valid signature. So, semantics, but you get what I mean. It acts similarly like a multi-signature signing scheme, without having each part its own private key, so the parts cannot be used for anything else but to collectively sign to produce valid signatures for the group.
[2] Coinbase acquired Unbound Security, a security company specializing in threshold signatures.
[3] For instance GJKR96 required that the number of participants needed to generate a signature always needed to be an odd number, and was more than the number needed to reconstitute the private key.
[4] The schemes that could do 2-of-3 did not exist prior to 2016.
[5] It is cheaper to record threshold on chain compared to multisig. If you want to ensure security over time of a threshold scheme without moving funds to a new key, you can just reissue shares of the current key. This is not possible in multisig—either you keep the same key and have a wide attack window but cheaper costs, or you change the keys to reduce the attack window, but it is more expensive. Lastly, there is more privacy with TS over multisig—an attacker cannot identify TS over a normal DS.

 07-02-2025
07-02-2025