|
Getting your Trinity Audio player ready...
|
This post was first published on Medium, and we republished with permission from its author, Gregory Ward. To learn more about Sentinel Node, check out their website here.
In the fast-paced realm of technology, cybersecurity has become a critical challenge that organizations must actively confront. In this article, I will recount an unsettling incident our team recently encountered. This incident emphasized the invaluable role played by Sentinel Node, a groundbreaking cybersecurity detection assurance tool, in safeguarding our platform from a potential cyber threat originating from China.
The unexpected connection:
Our story begins with setting up Sentinel Node on a newly launched application of our company. Within days of deployment, we started receiving continuous alerts from Sentinel Node regarding our Syslog. Investigating further, a routine netstat command alerted us to an SSH connection that we hadn’t authorized or expected. This connection originated from IP address 180.101.88.245 in China, raising immediate concerns regarding the security of our system.
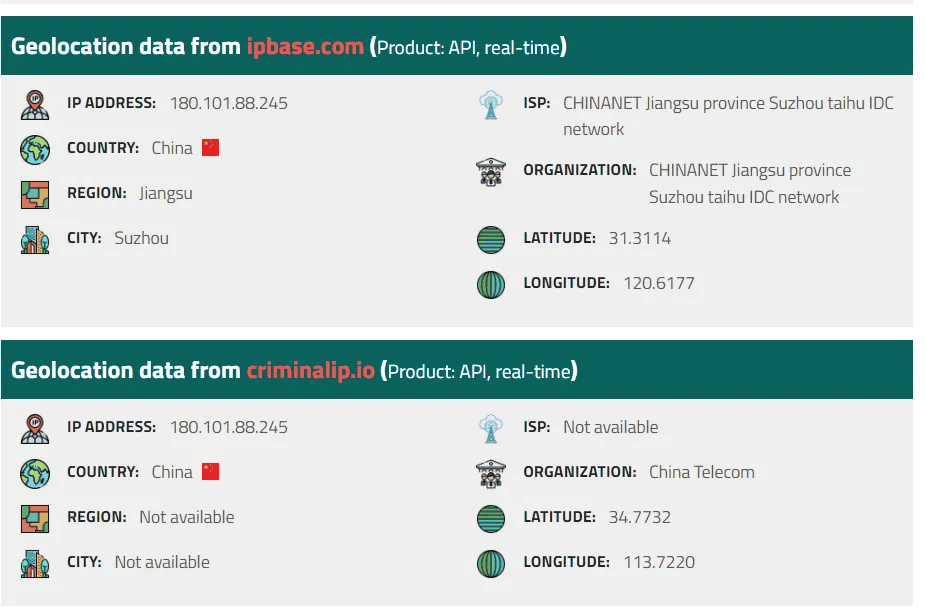
Digging deeper:
Understanding the context behind this connection is crucial in assessing its potential threat. Geolocation of the IP revealed that it belonged to various cities within China’s Jiangsu province. This discovery, coupled with evidence from AbuseIPDB indicating previous association with dubious activities, deepened our concern.
Sentinel Node to the rescue:
As a team that prioritizes cybersecurity, we were reassured by the pivotal role played by Sentinel Node in this incident. Sentinel Node not only alerted us to the unauthorized syslog changes but also provided us with the necessary warnings to take proactive measures.
Emphasizing accountability:
What sets Sentinel Node apart from other cybersecurity tools is its near-instant alerts and its commitment to transparency and accountability. Every action taken post-alert was meticulously logged, providing us with a clear view of the administrator’s activity on our platform. We were not dependent on external validation; Sentinel Node enabled us to maintain complete control and visibility.
Reflection:
This experience reaffirmed the unpredictable nature of the cyber landscape and underscored the importance of preemptive alert systems like Sentinel Node. In the face of both visible and hidden threats, Sentinel Node acted as our digital guardian, protecting us during a potentially dire situation.

Sentinel Node is the first application by CERTIHASH, in a suite of tools based on the NIST cybersecurity framework. Its SHA-256 collision-resistant cryptographic hash function provides unparalleled security. Furthermore, instant alerts and immutable transactions eliminate the need for third-party trust entities, ensuring an auditable, stable, and secure infrastructure for your organization.
With its capability for log monitoring, detection assurance, and accountability, Sentinel Node offers superior cybersecurity. In an era where cybercrime costs are projected to reach a staggering $10.5 trillion annually by 2025, embracing tools like Sentinel Node is essential in the fight against such threats. Not only does it provide advanced and effective solutions for modern information security, but it also offers sustainable measures to safeguard your data in the long term.
Conclusion:
In conclusion, the incident involving the unexpected SSH connection highlighted the real-time, preemptive alert system Sentinel Node provides. As organizations navigate the ever-increasing digital landscape, embracing tools like Sentinel Node is essential to mitigate the risks associated with cyber threats. With its cutting-edge technology and focus on accountability, Sentinel Node stands as a crucial component in safeguarding enterprises from potential cyber threats, ensuring near-instant detection, transparency, auditability, and reassurance in an increasingly vulnerable world.
Watch: Gregory Ward: BSV blockchain is an absolute fit for cybersecurity

 02-26-2026
02-26-2026