|
Getting your Trinity Audio player ready...
|
If you want to understand Bitcoin, sooner or later you’ll have to get to grips with questions of privacy, anonymity, pseudonymity and other tricky matters. Craig Wright, the Chief Scientist of nChain, has always insisted that Bitcoin wasn’t designed to be anonymous – because that would make it the natural choice of criminals: “at best, an anonymous system forms a methodology for black markets and illicit and illegal trade,” he wrote, earlier this year, “I was never interested in creating a dark-web money.”
Instead, Bitcoin is pseudonymous, meaning that transactions are linked. Unlike cash, whose history is hard to trace as soon as a coin is paid to someone else, Bitcoin histories are there on the blockchain for all to see. Whilst you can’t tell who is moving a coin on the blockchain, you can see all the transactions it’s been part of. So if you can link that coin to a person, their Bitcoin activity can be followed. Pseudonymity is a compromise, making the system private enough for individuals to feel secure, while leaving an immutable evidence trail that can be followed if something goes wrong.
Some cryptocurrencies are not satisfied with the level of privacy provided by pseudonymity. The cryptographic technique they use to further anonymise transactions is called zero knowledge proofs (ZKP). For Bitcoin SV, ZKPs are still a valuable tool, but not for financial transactions, for the reasons mentioned above. Instead, they can be a useful feature of applications that are developed for the BSV blockchain.
Zero knowledge proofs are so called because they provide proof of something without revealing all the important details that would normally be needed to confirm an event or transaction. In other words, they allow the prover to show someone that an event has taken place while giving them ‘zero knowledge’ of those important details.
So how could that be possible? How can you be sure that someone is telling you the truth without being able to see for yourself the information they’re talking about? Well, here’s an example to illustrate the principle:
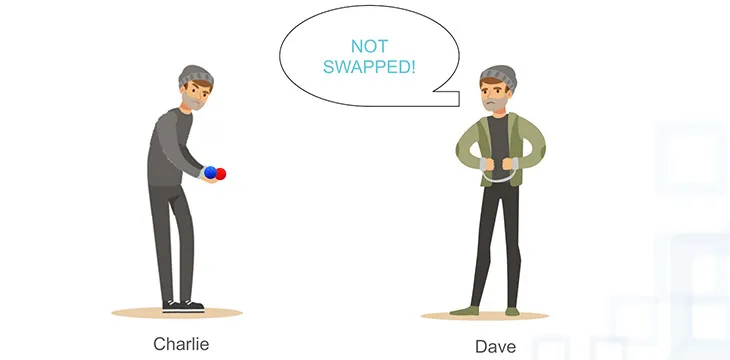
If you’re colour blind, could you ever confirm that two balls your friend gives you are different colours, when they look exactly the same to you?
Well, you could put the balls behind your back and then bring them out to show your friend – and ask whether you have swapped them round or not since the last time you showed them.
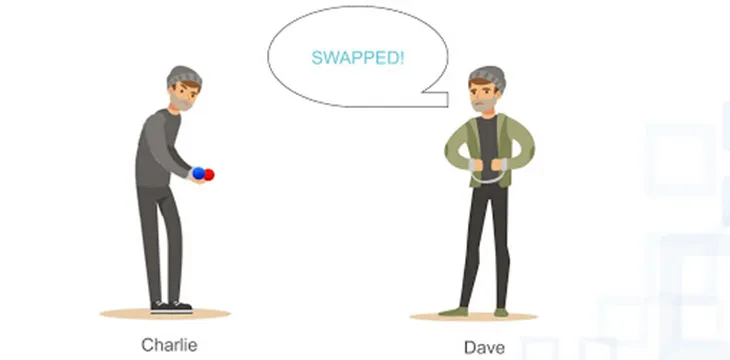
If your friend can consistently get this test right – knowing whether the balls have been swapped or not – then you can be sure that he was telling you the truth when he said they are different colours.
One important feature of this ZKP scenario is that it only works for Charlie and Dave. Someone else – a colour-blind Alice, say – could watch any number of successful demonstrations in which Dave gets the swap question right. But even if she could see whether Charlie was swapping the balls or not, she couldn’t be sure that the balls are different colours because Dave and Charlie may have colluded on the sequence of swaps and answers they were going to perform in front of her. Only by being able to decide on making the swaps herself and asking Dave to respond, could she have confidence in the conclusions.
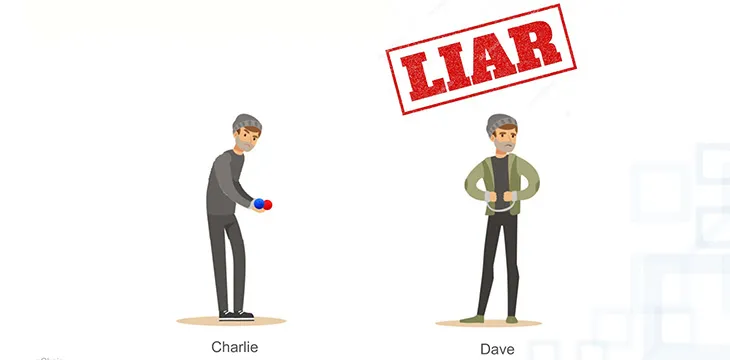
So that’s a ZKP: you can’t recognise a difference between the two balls but you have a proxy for that difference that you can use for purposes of verification.
Translating this principle to the world of blockchain requires some complicated maths, but the principle is the same: you’re trying to confirm information without allowing the recipient to see the details – when they’re confidential, for instance.
Jad Wahab of nChain has been studying ZKPs and offers these examples of possible use cases where they could provide a critical part of an app design using the BSV blockchain:
ZKPs could be useful in identity checks or selective disclosure and access control: you might want to be able to confirm that you’re above a certain age, for instance, without revealing your actual age.
In ballots or polls, you may want to only be able to confirm that someone is eligible to vote but for reasons of confidentiality, you wouldn’t want to create a list of those individuals.
ZKPs could also be useful when committing to some information on the blockchain without revealing anything about the information (which would happen with a hash of the information for example). Or for auditing processes where you would like to prove something to a specific auditor without necessarily revealing any information to anyone else.
Jad says that developers won’t necessarily need to understand the exact mechanisms behind the ZKP that they want to incorporate into their product. He believes that ‘off the shelf’ software could soon be developed that can be plugged into a design and provide the functionality required.
With thanks to Jad Wahab. Jad has written about the unlinkable polling system design mentioned above, which was the subject of his dissertation project at UCL.

 07-02-2025
07-02-2025