|
Getting your Trinity Audio player ready...
|
Beware of downloading these three applications—Jamm, DaoPoker and eTrade—as they will allegedly steal your digital currencies. According to cybersecurity experts, the three are disguised as digital currency trading and management apps, but end up stealing your private keys.
Cybersecurity experts from Intezer Labs discovered the malware and detailed it in a recent report.
[1/7] Operation #ElectroRAT is a new campaign that takes sizable measures to steal crypto wallets. For more information about the operation – https://t.co/CWLnOevKir
The following is a technical analysis->@IntezerLabs
— Avigayil Mechtinger (@AbbyMCH) January 5, 2021
According to the report, the Remote Access Trojan (RAT) malware became quite active in December when most digital currencies started recording huge price rises. ElectroRAT is written in the Golang programming language, allowing it to target multiple operating systems including Windows, MacOS and Linux.
The report notes that while its common for attackers to use information stealers to target victims’ private keys, it’s rare to see tools written from scratch and targeting multiple operating systems.
To lure victims, the attackers have been promoting them in dedicated online forums such as bitcointalk and SteemCoinPan. In one post on Chinese Hive forum, the attackers touted Kintum as a digital currency management platform that has “freedom and no trouble.” They falsely claim to have partnered with Coinbase, Bitfinex, Kraken, Binance and over 20 other exchanges.
For DaoPoker, the attackers went even further; creating social media accounts for the fake app. Twitter has since then suspended the account, however. The attackers allegedly used social media influencers to promote their fake apps.
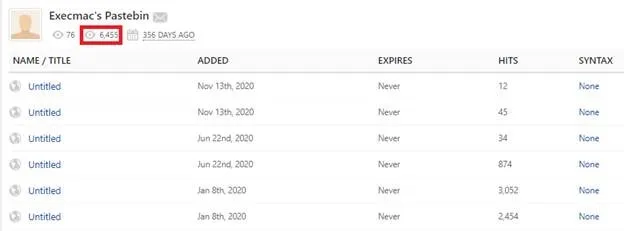
ElectroRAT contacts raw pastebin pages to retrieve the command and control (C&C) IP addresses. As Intezer Labs reveals, the number of unique visitors to the attackers’ pastes stands just short of 6,500. The pastebin page also indicates that the malware has been active for at least 356 days.
Once the victim runs any of the three fake apps, an innocent graphical user interface (GUI) opens while ElectroRAT runs in the background as “mdworker”.
“ElectroRAT is extremely intrusive. It has various capabilities such as keylogging, taking screenshots, uploading files from disk, downloading files and executing commands on the victim’s console. The malware has similar capabilities for its Windows, Linux and MacOS variants.”
The malware has remained under the radar for almost a year now. This is largely because the attackers wrote the malware from scratch. On VirusTotal, DaoPoker for instance is completely undetected.
See also: CoinGeek Live panel, Future of Digital Asset Security & Custody

 07-12-2025
07-12-2025 





