|
Getting your Trinity Audio player ready...
|
Another day…another DeFi attack. This time around, the DeFi project Compounder.Finance did not even try to hide the fact that they were defrauding their users; the Compounder team had a function in their smart contract that allowed them to withdrawal all of the funds from the project. The contract launched on November 9th, and 22 days later (December 1st) the Dev team decided that there was enough money locked up in their platform and that it was time for them to execute the function that sends Compounder user’s money to the developer team’s wallets–the classic developer rug pull.
In total, the dev team was able to steal over $10 million from its users; $5.066 million in DAI, 4.8 million in ETH (8,080 ETH), $745,000 Wrapped BTC (39 WBTC), and insignificant amounts (below one dollar) worth of the DeFi tokens COMP, UNI-V2, and CP3R.
To add insult to this rug-pull induced injury, Compounder.Finance was an audited DeFi project. Compounder.Finance was audited by Solidity Finance. The Solidity Finance team has even published documentation of their correspondences with Compounder.
During the initial audit, Solidity Finance did mention that a few functions within the Compounder project were unusual and created unnecessary risk; specifically, Solidity pointed out that the “treasury contract and updating of the strategy pools” remained in the control of the Compounder team.
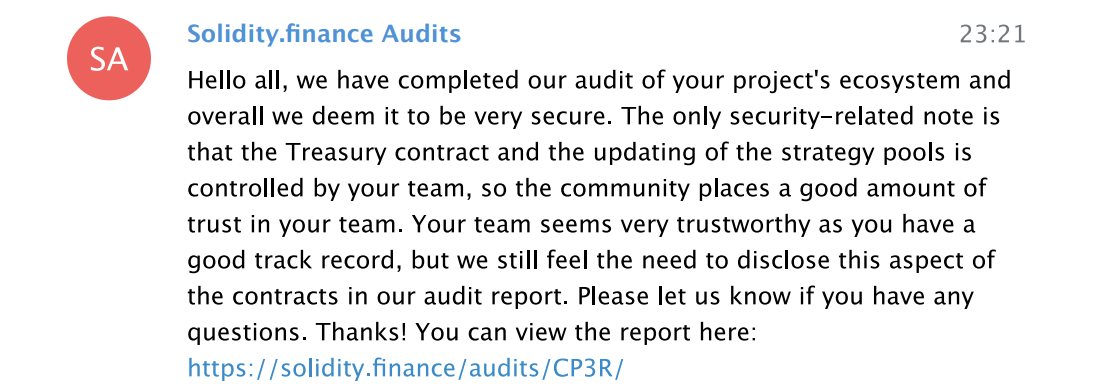
But after going back and forth with the Compounder team about the function in question, Solidity Finance ultimately finished their audit and said that Compounder Finance was safe from outside attacks… which is true, but they neglected to discuss the internal attack vector that they were worried about.
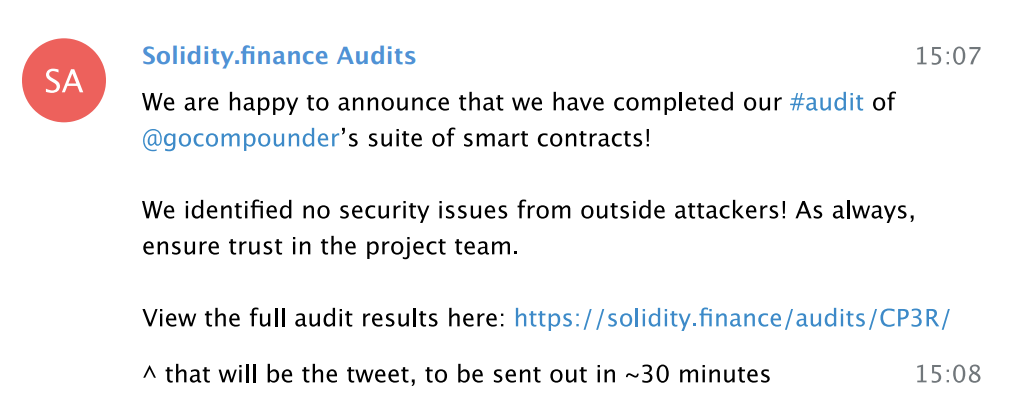
“We disclosed the fact that the compounder team could update the strategies through the timelock in our audit report, where we even linked to the timelock so users would know where to watch,” the Solidity Finance team told CoinGeek, before going on to say that,
The Compounder team swapped the safe/audited Strategy contracts and replaced them with malicious ‘Evil Strategy’ contracts that allowed them to steal users funds. They did this through a public, though clearly unmonitored, 24-hour timelock. Historically, our audits have focused on the risks to projects from external attackers, with some discussion on risks posed by project teams as we did here. We will take this unfortunate event as a learning opportunity, and moving forward will provide more robust details in easy to understand language on risks stemming from developers’ control.
What’s next?
The Compounder.Finance website and team have disappeared without a trace, like the other DeFi exploits and attacks that have taken place this year, it is highly unlikely that the true identities of the dev team will be discovered and that Compounder Finance investors will ever get their money back.
When it comes to investing in DeFi projects, you must proceed with caution; a majority of the projects in that space have insecure infrastructure and numerous attack vectors. The only way to stay dry in such a high risk environment is to not get involved.
Update (December 3rd 4:10 pm EST)
this article was updated to include two statements that the Solidity Finance team gave CoinGeek as well as the link to the audit report.

 03-02-2026
03-02-2026 




