|
Getting your Trinity Audio player ready...
|
Cybersecurity researchers are warning of a recent spike in activity of a stealthy digital currency mining botnet. Known as Lemon Duck, it targets Windows users and spreads by sending rich text format (RTF) files via email.
Lemon Duck has been around since December 2018. However, researchers at Cisco-owned Talos Intelligence Group have noticed a sharp rise in DNS requests connected with its command-and-control (C2) servers since the end of August.
In a blog post, the researchers revealed that Lemon Duck has 12 independent infection vectors, making it more potent than most malware. They include sending emails containing exploit attachments and brute-forcing a system’s SMB protocol. Once it infects a computer, it downloads a PowerShell loading script which disables the Windows Defender’s real-time protection. It also includes powershell.exe on the list of processes excluded from scanning.
Once installed, the botnet downloads and activates a mass-mailing module and then sends emails to all the victim’s contacts through Microsoft Outlook. These emails contain two malicious files, readme.doc and readme.zip, that download and install Lemon Duck on the target computer. To entice their targets, the emails contain COVID-19 related text.
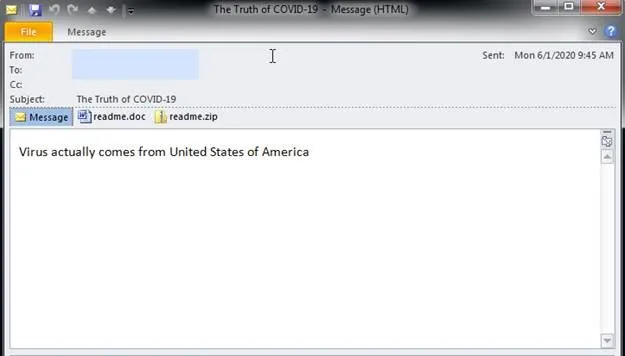
Source: Talos Intelligence Group
Lemon Duck combines code taken from several open-source projects with code specifically designed by the hacker, “showing moderate level of technical skills and understanding of security issues in Windows and various network protocols,” according to the report.
Talos researchers revealed that there were a number of overlaps between Lemon Duck and yet another cryptojacking malware dubbed Beapy that targeted East Asia in 2019. The two botnets also share emails and a number of URLs.
The resurgence of Lemon Duck is consistent with an uptick in digital currency mining malware recently observed by Talos, including the return of PowerGhost, Tor2Mine and Protemei.
Lemon Duck, like most other cryptojacking malware, mines Monero, a dark coin whose relative anonymity makes it the go-to for hackers. The botnet’s most popular targets are Egypt, China, Iran, Vietnam and India.
Watch Dr. Craig Wright’s CoinGeek Live presentation, Outsourced Computation on Bitcoin: How One World Blockchain Powers a New Future for Computing & Cloud System.
https://www.youtube.com/watch?v=FAEoXeN0b8M&feature=youtu.be&t=26697

 09-16-2025
09-16-2025 





