|
Getting your Trinity Audio player ready...
|
In this article, Marquez Comelab looks into the power and flexibility of combining BSV with the Secret Slices tool. Secret Slices is a standout tool, offering unparalleled functionality and adaptability to cater to a diverse range of use cases tailored to individual needs and circumstances.
We unveil a groundbreaking method to safeguard your BSV and ensure it’s passed on securely to your loved ones or protected in your business dealings. Discover how the ingenious combination of BSV and Shamir’s Secret Sharing, using a tool called Secret Slices, can revolutionize the way we handle secret private keys to BSV addresses, offering unprecedented security and control. From ensuring your children’s inheritance to protecting your hard-earned business income in developing countries, this article explores real-life scenarios that showcase the power and flexibility of combining BSV with cutting-edge solutions.
Imagine you have BSV stored on the blockchain. You are using it in your life and your business. You have the private key or access codes for the address where your BSV tokens are stored; naturally, you want to keep it safe. You may wish to share it or leave it for someone special in the future. Applying the concept of Shamir’s Secret Sharing, there is an innovative way to protect and control your private keys using a free tool called Secret Slices. In this article, we are going to consider what it would be like if people used BSV tokens as cash and explore how they can protect and access BSV tokens for personal use as well as in their various businesses.
Examples of how Secret Slices using Shamir’s Secret Sharing is useful
Use-case 1: Saving money for the future
Imagine David and Jill, parents with a vision of securing their children’s future by accumulating BSV tokens to pass on to them as they mature or in the event of unforeseen circumstances. Traditionally, parents facing this scenario might opt for the cumbersome and expensive route of establishing a will or trust.
But what if there were a simpler alternative? What if David and Jill could bypass the legal and technical complexities associated with wills and trusts?
Enter a straightforward solution: enlisting the support of trusted family members or relatives. By entrusting a select few with the knowledge of the private key required to access BSV tokens stored in a address, David and Jill can give BSVs as gifts to their children.
No need for intricate legal maneuvers or costly setups. Just a network of trusted individuals standing ready to reveal the parts needed to disclose a private key to a BSV address when the time is right—whether it be when the children reach adulthood or in the unfortunate event of David and Jill’s absence.
This approach not only simplifies the process but also reinforces the importance of family bonds and trust, providing David and Jill with peace of mind knowing that their children’s financial security is in capable hands.
Use-case 2: Securing small business earnings in a developing country
In many developing countries, street vendors and small business owners face the constant threat of losing their hard-earned income to theft, particularly in high-crime areas. Traditional cash is vulnerable, and while digital currencies offer an alternative, they, too, need protection against digital theft or coercion.
Consider Pepito, a seasoned street vendor in the Philippines known for selling balut, a popular delicacy made from duck eggs. Pepito has set up his makeshift stall on various streets for over four decades, diligently serving his customers. However, his earnings are not always secure. There have been instances where he was robbed of his day’s earnings while packing up or on his way home.
Opening and maintaining a bank account is prohibitively expensive for Pepito, a reality shared by many adults in the Philippines and other developing countries. Cash transactions dominate, with no paper trail of invoices or receipts and no reliance on bank accounts for settlement.
However, if Pepito were to accept payments in BSV, the digital token would be sent directly to his BSV address. What sets this apart is that the BSV stored in his address is inaccessible to both Pepito and potential robbers. Accessing these funds would require cooperation from Pepito’s family members and relatives, creating a significant barrier to quick theft.
By integrating BSV payments into his business, Pepito not only mitigates the risk of physical theft but also ensures the security of his earnings through a decentralized and tamper-resistant system. This innovative approach not only safeguards Pepito’s livelihood but also sets a precedent for leveraging digital tokens to empower small businesses in developing economies.
Use-case 3: Protecting money in businesses even in developed countries
Imagine Ramilo, the owner of a bustling Italian pizzeria, where teamwork and collaboration are essential to serving thousands of pizzas across Italy. Picture this: all the waiters diligently attend to guests, receiving payments in the form of BSV tokens for the delicious pizzas and drinks they serve.
Now, consider a unique system in place to safeguard these earnings. The BSV tokens collected from transactions are deposited into a secure BSV address and are accessible only under specific conditions. For instance, access may be granted when Ramilo authorizes it, his accountant concurs, and one of his trusted store managers approves.
This ingenious setup ensures that any expenditure of the funds requires unanimous agreement from all parties involved. By implementing such a system, the risk of theft or misuse is significantly reduced. Each individual involved in the process serves as a checkpoint, adding layers of security to the pizzeria’s finances.
In this way, Ramilo not only protects the hard-earned money of his business but also fosters a culture of trust and accountability among his team. It’s a testament to the power of collaboration and innovation in safeguarding assets in the modern business landscape.
How to use Shamir’s Secret Sharing method using SecretSlices.com
Shamir’s Secret Shares (SSS) is a mathematical method devised by the esteemed Israeli cryptographer Adi Shamir, renowned as one of the co-inventors of the widely utilized RSA encryption algorithm. Picture this: envision slicing a secret message into fragments (parts or shares), where each individual fragment holds no meaning on its own. However, when a specific number of these fragments (parts or shares) are brought together, they seamlessly reconstruct the original message. This ingenious concept is the essence of Shamir’s Secret Sharing!
In practical terms, SSS divides a secret into multiple shares, ensuring that the complete information remains concealed unless a sufficient number of shares are combined. This innovative approach safeguards sensitive data, even when individual shares may inadvertently land in unauthorized hands.
SecretSlices.Com harnesses the power of Shamir’s Secret Shares method and is meticulously crafted by the collaborative efforts of SmartLedger & Codenlighten. These two teams specialize in developing tools tailored for use with the BSV blockchain and secure data management.
This website boasts a streamlined one-page interface, accessible across various browsers. Notably, its HTML functionality enables offline usage, ensuring your input data remains confidential and impervious to interception or online transmission. Furthermore, Secret Slices has inscribed its HTML file to the BSV Blockchain to ensure that years or decades from now, even if they are no longer in operation, you can still download the tool they have developed from the BSV blockchain and still be able to reveal your ‘secret.’
How to split a secret, and share its parts
In the “Split Secret” section, you will encounter the following interface1:
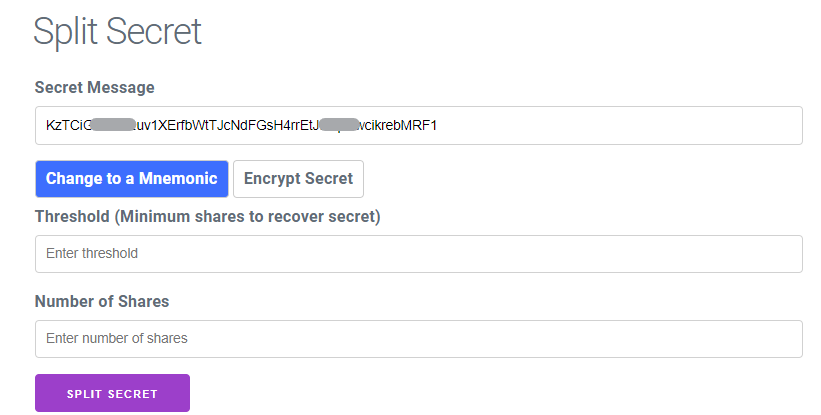
- Enter your “Secret Message” into the designated field. You have the flexibility to input any combination of text, numbers, or even paragraphs of text. However, for purposes, let’s assume you’re entering a private key to the BSV address.
- In the “Threshold (Minimum Shares to Recover Secret)” field, specify the minimum number of ‘shares/parts/fragments’ required to reconstruct the ‘secret.’ Each ‘share’ is allocated to an individual or legal entity like a company or a Trust. For instance, if you wish to mandate that two individuals or legal entities are needed to reconstruct the private key of a Bitcoin address, input “2” to indicate two shares or two parts.
- Consider the consequences of distributing only the minimum number of ‘shares’ required. If one or both of these individuals or entities become unavailable in the future, it could hinder the recovery process. Hence, it’s advisable to distribute ‘shares’ to more individuals or entities, increasing the likelihood of having the necessary ‘shares’ available when needed. For example, if you want to distribute four ‘shares’ to four different individuals or entities, of which only two are required to reconstruct your ‘secret,’ input “4” in the “Number of Shares” field.
- After clicking the “SPLIT SECRET” button, you will observe that the ‘secret’ is divided into three distinct ‘parts.’ Each ‘part’ represents a ‘share’ of the original secret message. These ‘shares’ are essential for reconstructing the ‘secret’ when needed.
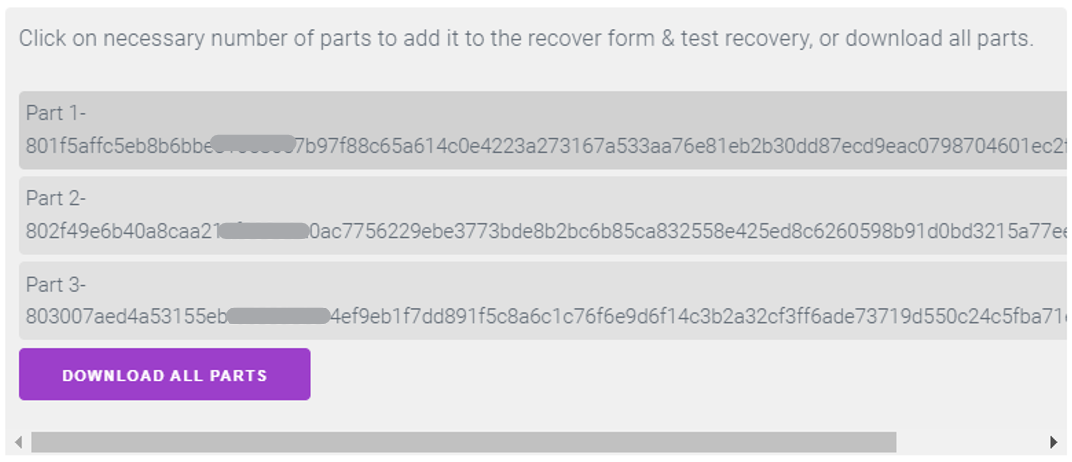
- Allocate one ‘part’ of the ‘secret’ to each of the three selected individuals or legal entities.
- Each recipient will retain their assigned ‘part’ of the ‘secret’ until there arises a need to reconstruct the ‘secret.’ In our scenario, this could involve revealing the private key to access a BSV address.
- For our earlier examples:
-
- David and Jill may distribute ‘part’ of the ‘secret’ to relatives, as well as their children.
- Pepito could distribute ‘part’ of the ‘secret’ to his family and relatives.
- Ramilo might allocate ‘parts’ of the ‘secret’ to himself, his managers, and their accountants, bookkeepers, or financial controllers.
How to recover a ‘Secret’
When the time comes to recover a ‘secret’ (such as revealing the private key to access a BSV address), you have several options for accessing Secret Slices:
Simply revisit the website, secretslices.com, using any web browser.
Alternatively, you can load a saved copy of the HTML file from your hard drive or USB stick. This ensures offline access and mitigates the risk of data interception.
If the website ceases to exist or you lose your saved HTML file, don’t fret. You can always retrieve the HTML file from the BSV blockchain2, ensuring perpetual access to the Secret Slices functionality.
Once you’ve loaded the HTML file, navigate to the designated section to recover the secret. From there, you can input the necessary ‘shares/parts/fragments’ to reconstruct the original ‘secret,’ allowing you to access the private key and unlock the BSV address.
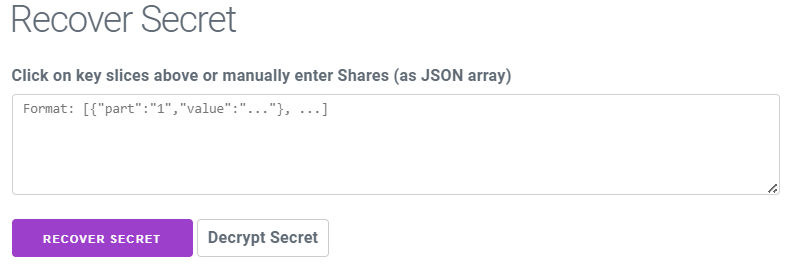
Assuming you possess the first and third ‘parts/shares/fragments’ from the individuals or legal entities you previously allocated ‘shares’ to, you would input the ‘shares’ into the designated field using the syntax provided in the image above:
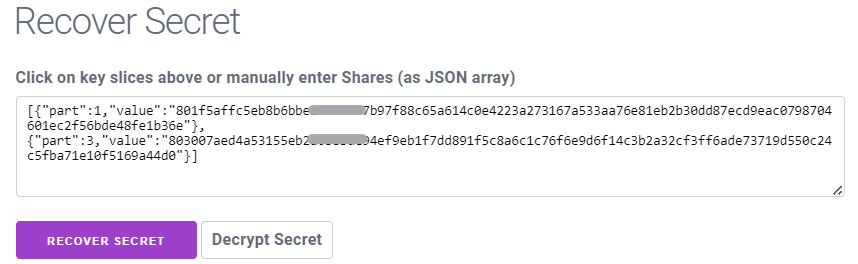
After correctly inputting the ‘shares’ into the designated field, you would then proceed to click on the “RECOVER SECRET” button. Upon doing so, the website will initiate the process of reconstructing the original secret message. Once completed, you will successfully recover your ‘secret,’ enabling you to access the private key associated with the BSV address.

As an additional option, you may also want to encrypt your ‘secret’ (Private Key) using a password and decrypt it using that same password, using the “Encrypt/Decrypt Secret” button. This adds an extra layer of flexibility so that, even if the ‘parts/shares/fragments’ have been collected, a password will still be required to reveal the ‘secret’/Private Key.
Conclusion
In this article, we delved into various hypothetical scenarios confronting individuals and businesses seeking to safeguard their BSV tokens while also ensuring controlled access to private keys associated with BSV addresses. We explored the versatility of Secret Slices in addressing these challenges and providing tailored solutions.
For parents like David and Jill, Secret Slices offers a means to securely entrust the keys to a BSV address containing savings for their children until they reach adulthood.
In the case of Pepito, a street vendor, Secret Slices becomes a vital tool in safeguarding his BSVs from theft, ensuring his hard-earned earnings remain secure.
Additionally, we examined how Secret Slices can cater to the needs of business owners even in developed countries, like the pizza chain proprietor, Ramilo, enabling his employees to accept payments in BSVs while ensuring access to the associated BSV address, is controlled by specific conditions set by management.
Secret Slices is a standout tool, offering unparalleled functionality and adaptability to cater to a diverse range of use cases tailored to individual needs and circumstances. As a free resource, it doesn’t promise any guarantees and cannot insure against any unforeseen malfunctions or losses, but its transparent code invites scrutiny and evaluation from anyone interested. The absence of complex setup, installations, or ongoing maintenance significantly reduces potential failure points, enhancing reliability. Its inherent simplicity infuses it with the robustness it needs to remain functional longer. Secret Slices solidifies its longevity by having been inscribed on the immutable BSV blockchain. As long as the BSV blockchain endures, Secret Slices will be downloadable from the blockchain decades into the future.
NOTES:
[1] Please note that certain parts of the private key, the ‘secret,’ the ‘shares/parts/fragments’ have been blocked out to minimize risk on the infinitesimally small chance that someone ends up using this same wallet in the future.
[2] https://plugins.whatsonchain.com/api/plugin/main/8d24a5defe5c3d67862fea08e5942b2c
64fd4afc332babcc06ec0d136d3c6a33, last accessed March 24, 2024.
Watch: Unleashing data rebellion—How Web3 is reshaping the Internet

 03-04-2026
03-04-2026 




