|
Getting your Trinity Audio player ready...
|
Cybercriminals are now targeting WordPress websites using malicious plugins to plant cryptojacking malware. According to a new report, the plugins are also being used to give the attackers access to the compromised server. These plugins have been increasing over the past few months, probably as a result of their success.
The report by website security company Sucuri revealed that interest in WordPress plugins by attackers has steadily risen in the past few months. These plugins always appear harmless at first glance, but they are used by the attackers as “a backdoor for the attacker to maintain access to the compromised website environment, even after the initial infection vector has been cleaned up.”
Fake #WordPress #plugins are being installed on compromised sites to upload scripts used for #bruteforce attacks via @unmaskparasites . https://t.co/eItjBbe0Hf #infosec #websitesecurity
— Sucuri Security (@sucurisecurity) October 17, 2019
In the past, these plugins have been used for different purposes, including in August this year when Sucuri discovered that they were being used to encrypt blog content.
The blog post stated, “We recently discovered a number of compromised websites containing a plugin called “wpframework”. This plugin is being planted by bad actors to gain and maintain unauthorized access to the site environment.” The plugin contains the following information on its header:
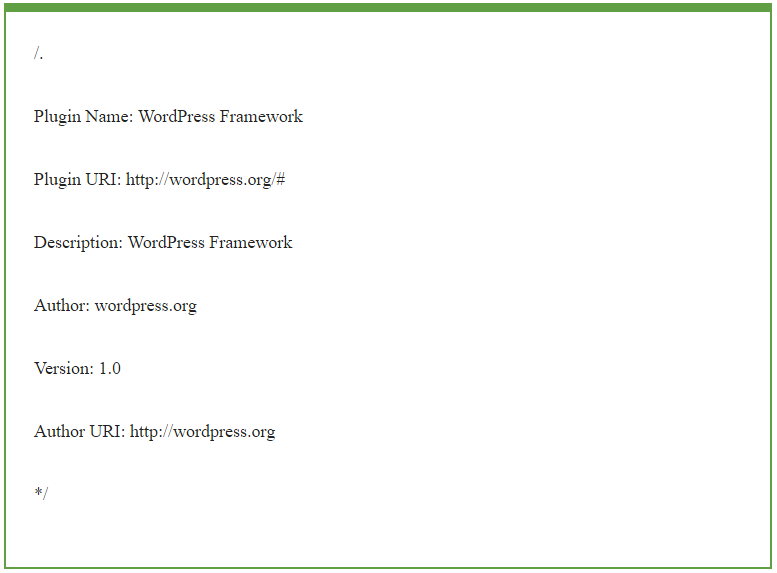
Once a website owner installs the plugin, it first checks to see if there are any disabled functions. It then scans for the usual, including system and passthru functions which give the attackers command execution ability on the compromised server.
Unlike most backdoors that only focus on a PHP execution, this plugin changes permissions upon downloading and runs a Linux executable binary file which the researchers identified as a cryptominer.
The report concluded, “What is especially concerning about this particular fake plugin is that it can be easily used to just run just about any code through the eval function. The good news is that monitoring for changes to the active plugins on your website and unauthorized access is a good way to mitigate risk and prevent this from happening.”
As CoinGeek recently reported, last week saw the discovery of the first cryptojacking worm known as Graboid as well as the use of WAV files to spread cryptojacking malware.

 03-02-2026
03-02-2026 




