|
Getting your Trinity Audio player ready...
|
This article was first published on Dr. Craig Wright’s blog, and we republished with permission from the author.
Abstract. Cybercrime has become a pervasive and complex issue in today’s interconnected world, posing significant threats to individuals, businesses, and governments. This paper aims to provide a comprehensive overview of the diverse aspects related to cybercrime, including its historical context, demographic and geographic dimensions, environmental influences, and preventive strategies. This review provides a holistic overview of the multifaceted dimensions of cybercrime. By understanding its historical context, demographic and geographic aspects, environmental influences, and preventive strategies, policymakers, law enforcement agencies, and researchers can work collaboratively to combat cyber threats effectively. Such a comprehensive approach will help create a safer digital environment and protect individuals, organizations, and societies from the adverse impacts of cybercrime. Moreover, through ongoing research and collaboration, it is possible to develop innovative solutions and adapt to the evolving landscape of cyber threats, ensuring a secure and resilient digital future.
1. Geographical Aspects of Cybercrime: A Literature Review
Cybercrime has become a pervasive and complex issue in today’s interconnected world (Chen et al., 2023), posing significant threats to individuals, businesses, and governments. This literature review aims to provide a comprehensive overview of the diverse aspects related to cybercrime, including its historical context, demographic and geographic dimensions, environmental influences, and preventive strategies (Dupont, 2019).
Beginning with a historical perspective, this literature review outlines the evolution of cybercrime, highlighting its global reach and impact. It emphasizes the need for a proactive approach to combat cyber threats and protect digital ecosystems. Next, the literature review explores the demographic and geographic aspects of cybercrime. First, it delves into the demographic profiles of cybercriminals, considering factors such as age, gender, education level, and socioeconomic status (Onyeneke & Karam, 2022).
Understanding these demographic patterns helps policymakers develop targeted interventions and educational initiatives to mitigate cybercrime risks effectively. Additionally, it examines the geographic distribution of cybercrime, acknowledging the influence of internet connectivity, economic disparities, and geopolitical factors. By mapping the spatial patterns of cybercrime incidents, authorities can allocate resources, strengthen cross-border cooperation, and implement tailored enforcement strategies (Zagaris & Mostaghimi, 2022).
As explored in this literature review, environmental factors play a crucial role in understanding cybercrime. It addresses the influence of the online environment on criminal behavior, including virtual spaces and the creation of pseudo-identities in online criminal activities. Moreover, it highlights the role of technology, socioeconomic conditions, and political dynamics in facilitating cybercriminal operations. Analyzing these environmental influences contributes to a comprehensive understanding of cybercrime and aids in developing preventive measures (Burke, 2014).
Lastly, this literature review discusses the significance of prevention strategies and the application of environmental criminology concepts in addressing cybercrime. It explores the development of prevention strategies, emphasizing the need for interdisciplinary approaches incorporating environmental factors into cybersecurity frameworks. By applying crime and place approaches, authorities can identify high-risk areas, enhance security measures, and disrupt cybercriminal networks (Frank & Mikhaylov, 2020).
In conclusion, this literature review provides a holistic overview of the multifaceted dimensions of cybercrime. By understanding its historical context, demographic and geographic aspects, environmental influences, and preventive strategies, policymakers, law enforcement agencies, and researchers can work collaboratively to combat cyber threats effectively (Choo, 2011). This comprehensive approach will help create a safer digital environment and protect individuals, organizations, and societies from the adverse impacts of cybercrime.
1.1 Introduction and research focus
Investigating cybercrime linked to digital currency systems or “crypto” presents an opportunity to develop comprehensive models that combat fraud and aid in tracing funds associated with illicit activities. Moreover, with the increasing popularity and use of cryptocurrencies, it has become imperative to address the emerging challenges posed by cybercriminals who exploit these systems for their illegal gains (Foley et al., 2019).
By focusing on human geography issues within cybercrime, we can gain valuable insights into the patterns and dynamics of criminal activities. For example, Buil-Gil and Saldaña-Taboada (2022) have highlighted that a small proportion of offenders are responsible for a disproportionately large number of crimes. This finding emphasizes the presence of highly active and influential individuals or groups involved in fraudulent practices and money laundering.
Analyzing criminal activities associated with fraud and money laundering within geographically isolated and concentrated groups is crucial to combat cybercrime. These groups often exploit specific vulnerabilities or localized conditions that make their illicit operations easier. By focusing investigative efforts on these geographically defined clusters (Lusthaus et al., 2020), law enforcement agencies and regulatory bodies can better understand the social, economic, and cultural factors contributing to the prevalence of cybercrime within those areas.
Through rigorous analysis of these concentrated groups, authorities can identify key individuals or networks involved in cybercriminal activities. This information can then be used to implement targeted interventions, such as improved surveillance, enhanced cybersecurity measures, and specialized training for law enforcement personnel in those regions. In addition, by specifically targeting these high-risk areas, resources can be allocated more efficiently, maximizing the impact of crime prevention efforts (Dupont, 2019).
Furthermore, investigating cybercrime associated with digital currencies can lead to developing advanced technological solutions and models. These models can help detect suspicious transactions, identify potential fraudsters, and facilitate the tracing of funds through the complex network of digital currency transactions. By leveraging data analytics, artificial intelligence, and machine learning algorithms, law enforcement agencies can enhance their capabilities to uncover hidden connections and disrupt criminal networks operating in the digital realm (Faubert et al., 2021).
The presence of a company within a particular country or jurisdiction significantly impacts its cyber threat profile (Chen et al., 2023). Geographic factors play a crucial role in shaping cybercrime, as demonstrated by Chen et al. (2023). Their research highlights that cybercrime is influenced by political, economic, and social factors that extend beyond technological considerations, encompassing concepts such as cyber terror and cybercrime. In contrast, traditional cyber threats are not limited to specific geographic targets.
The study by Chen et al. (2023) emphasizes the importance of understanding the geographical context in which cybercrime occurs. By considering the political landscape, economic conditions, and social dynamics of a region, researchers can understand the multifaceted nature of cybercrime. Furthermore, this broader perspective helps identify cybercriminals’ various motivations, strategies, and tactics, enabling the development of targeted interventions and prevention strategies.
Moreover, the influence of geographic factors on cybercrime extends beyond the traditional boundaries of nation-states. With the growing interconnectedness of digital networks, cyber threats have become increasingly transnational. This implies that the cyber threat landscape is not confined to specific geographic locations but operates globally. Cybercriminals exploit vulnerabilities and target victims across borders, highlighting the need for international cooperation and collaboration in combating cybercrime (Stein, 1982).
The findings of Chen et al. (2023) underscore the significance of incorporating geographic factors into the analysis and prevention of cybercrime. Understanding the geopolitical, economic, and social dimensions of cyber threats provides a comprehensive framework for developing effective strategies to mitigate and respond to cybercriminal activities. Policymakers, law enforcement agencies, and cybersecurity professionals can leverage this knowledge to strengthen their efforts to combat cybercrime, enhance global cybersecurity, and safeguard digital ecosystems.
In conclusion, the study by Chen et al. (2023) highlights the influence of geographic factors on cybercrime. The combination of political, economic, and social aspects extends beyond technological considerations and encompasses cyber terror and crime. Traditional cyber threats do not adhere to fixed geographic targets. Understanding the geographical context is crucial in comprehending the motivations and strategies employed by cybercriminals. Moreover, the transnational nature of cyber threats emphasizes the need for international cooperation in addressing cybercrime. Incorporating geographic factors into cybercrime analysis and prevention strategies enhances the effectiveness of efforts to combat cybercriminal activities and protect global digital systems.
The geographical profiling of cybercrime groups has been highlighted to understand the spatial aspects of these activities (Butkovic et al., 2019). Furthermore, this approach allows for the modeling of the geography of crime, as discussed by Vandeviver and Bernasco (2017). For example, Mustapha and Bensalah (2019) conducted a study analyzing cybercrime in Morocco, providing an example of cybercrime modeling within a specific geographic context. In addition, reports from United States law enforcement agencies have documented cases of transnational fraud, highlighting the relevance of geographic factors in understanding cybercrime (Zagaris & Mostaghimi, 2022).
Exploring concepts of cyber warfare is an extension of this investigation (Stoddart, 2022). The development of darknet markets, organized crime, and ransom activities involving proxy actors and states are interconnected with cybercrime. The geographical aspects of transnational fraud schemes are directly linked to cybercrime and dark market payment schemes (Faccia et al., 2020). The lack of research on the geographic location of individuals involved in criminal activities contributes to increased incidents of money laundering and terrorist funding.
While the online environment extends globally over the internet, it remains connected to specific individual locations worldwide (Miró-Llinares & Moneva, 2020). The uneven geographic distribution of different types of cybercrime offers opportunities for macro-level analyses, including integrating environmental criminology studies (Miró-Llinares et al., 2020). Geographic information has been utilized to profile e-crimes for several decades (Tompsett et al., 2005). However, the dynamic nature of cybercriminal activities necessitates continuous research and updates to maintain the viability of geographic profiling in understanding and combating cybercrime.
Environmental criminology, a subfield of human geography, focuses on studying the behavior of specific groups within the global population (Hayward, 2012). In the context of cybercrime, integrating geographic studies has emerged as a new trend in profiling criminal activity conducted over the Internet (Bada & Nurse, 2021). The geographical dimension allows for a deeper understanding of the spatial aspects and patterns of cybercriminal behavior.
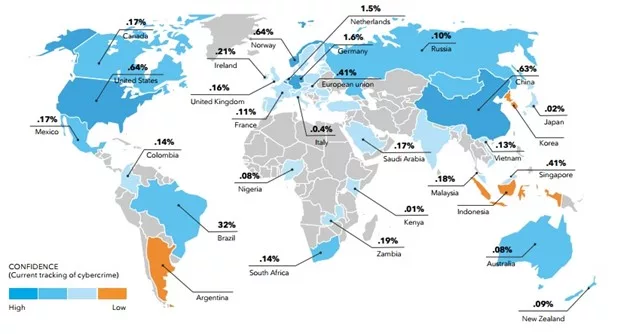
Sharma (2019) highlights China and Brazil as prominent players in global cybercrime, possessing significant digital attack capabilities and engaging in economic espionage. These regions, when combined with the use of digital currency and crypto payments, can cultivate highly capable cyber mercenary forces that have the potential to disrupt the global economy.
In conclusion, investigating cybercrime associated with digital currency systems or “crypto” can lead to the development of robust models that mitigate fraud and enable the tracing of funds related to illicit activities. In addition, by considering human geography issues, law enforcement agencies can effectively combat cybercrime by focusing on geographically isolated and concentrated groups. Through targeted investigations, leveraging advanced technological solutions, and implementing strategic interventions, significant progress can be made in reducing cybercrime and ensuring the security and integrity of digital currency systems.
1.2 Study area
Studying cybercrime from a geographical perspective involves exploring several key areas intersecting human geography. This approach provides valuable insights into the spatial dynamics, social factors, and regional variations associated with cybercriminal activities (Hall et al., 2021). By examining these areas of interest, researchers can understand the multifaceted nature of cybercrime and develop effective strategies to combat it. The concept of the digital divide also holds relevance in studying cybercrime from a geographical perspective. Examining disparities in access to and usage of digital technologies among different regions and social groups sheds light on how unequal access may contribute to vulnerabilities and criminal opportunities (Asmar et al., 2022). Understanding the impact of digital divides helps develop targeted interventions and policies to bridge the gap and reduce cybercrime risks.
Spatial patterns in the distribution of cybercrime incidents offer valuable insights into the concentration of criminal activities within specific geographic areas. By employing mapping techniques and conducting thorough analyses of cybercrime locations, researchers can identify hotspots and gain a deeper understanding of the spatial factors contributing to the prevalence of cybercrime in different regions (Lusthaus et al., 2020). This investigation involves mapping the locations of cybercrimes and analyzing their spatial distribution to identify clusters or areas with higher concentrations of criminal activities. Furthermore, by examining the spatial patterns of cybercrime, researchers can uncover geographical hotspots where cybercriminal activities are more prevalent, thereby shedding light on the spatial factors that contribute to such patterns (Qi et al., 2022). Such an approach enables a comprehensive understanding of the spatial dynamics and factors influencing the occurrence of cybercrime, providing a foundation for targeted interventions and prevention strategies (Ife et al., 2022).
Moreover, considering local contexts and cultures is crucial when studying cybercrime geographically. Cultural norms, legal frameworks, social networks, and regional-specific circumstances shape cybercriminal activities (Márquez Carrasco et al., 2016). Analyzing these factors helps understand the motivations, tactics, and strategies employed by cybercriminals in different regions, aiding the development of context-specific prevention and intervention measures.
The effectiveness of law enforcement and regulatory approaches in addressing cybercrime varies across jurisdictions, making it another important area of interest (Koziarski & Lee, 2020) and aiding in implementing evidence-based policing. In addition, comparative studies of different regions’ legislative frameworks, enforcement efforts, and international cooperation contribute to a better understanding of successes and challenges in combating cybercrime. With this, the distributions of cybercrime displayed in figure 1 allow researchers to understand how cyber criminals target victims.
Furthermore, examining digital infrastructure and its spatial distribution plays a significant role in understanding cybercrime dynamics (Kethineni et al., 2018). The availability of internet connectivity, data centers, and online platforms varies geographically, affecting the opportunities and vulnerabilities related to cybercrime. Therefore, analyzing the spatial aspects of digital infrastructure helps identify potential weak points and improve cybersecurity measures.
Lastly, understanding the transnational dimensions of cybercrime is crucial due to its cross-border nature (Broadhurst, 2006). Investigating the flows of illicit funds, the role of virtual jurisdictions, and the complexities of international cooperation in addressing cybercrime provides insights into the global implications of this phenomenon. Studying cybercrime from a geographical perspective involves examining various areas of interest, including spatial patterns, geodemographics, the digital divide, local contexts and cultures, law enforcement and regulatory approaches, digital infrastructure, and transnational dimensions. Analyzing these areas provides a comprehensive understanding of cybercrime dynamics, enabling the development of targeted interventions, policies, and strategies to effectively prevent and combat cybercriminal activities (Ho et al., 2022).
Geodemographics involves analyzing the characteristics of populations in various geographic areas to gain insights into cybercrime. By examining the demographic profiles of regions with higher rates of cybercrime, researchers can identify potential correlations between specific socioeconomic factors, such as income levels, education, and employment, and the propensity of individuals to engage in cybercriminal activities (Robinson et al., 2015). This analysis provides valuable information about the social and economic influences that may contribute to cybercriminal behavior in different areas, thereby aiding in developing targeted prevention and intervention strategies (Onyeneke & Karam, 2022).
The concept of the digital divide encompasses the inequalities in access to and utilization of digital technologies among diverse regions and social groups (Park et al., 2019). Analyzing the correlation between digital divides and cybercrime provides insights into how uneven technology access and limited digital skills might increase vulnerabilities and create criminal opportunities (Ragatz & Fremouw, 2010). Understanding this relationship is essential in comprehending the underlying factors contributing to cybercriminal behavior. By examining the influence of digital divides on cybercrime, researchers can develop a deeper understanding of the societal implications of unequal access to technology and formulate targeted strategies to address these disparities and mitigate associated cybercrime risks.
The local context and cultural factors substantially impact shaping cybercriminal activities (Dijk, 2020). Cultural norms, legal frameworks, social networks, and region-specific circumstances influence both the prevalence and nature of cybercrime (Abdulai, 2022). Analyzing these local contexts provides a deeper understanding of the motivations, strategies, and tactics employed by cybercriminals in different regions (Nouh et al., 2019). Furthermore, researchers can gain insights into the socio-cultural dynamics contributing to cybercriminal behavior by examining the interplay between cultural factors and cybercrime. This knowledge is crucial for developing targeted interventions and strategies sensitive to the local context and cultural nuances, thereby enhancing efforts to prevent and combat cybercrime (Boes & Leukfeldt, 2017).
Law enforcement and regulatory approaches to combating cybercrime exhibit variations across jurisdictions, leading to differences in their effectiveness (Friend et al., 2020). Comparative studies examining how different regions tackle cybercrime, encompassing legislative measures, enforcement strategies, and international cooperation, offer valuable insights into the successes achieved and challenges encountered (Collier et al., 2022). These comparative analyses shed light on the diverse approaches adopted by authorities worldwide, aiding in identifying best practices and areas for improvement in combating cybercriminal activities (Kraemer-Mbula et al., 2013). Furthermore, understanding the strengths and weaknesses of different law enforcement and regulatory frameworks facilitates the development of more effective strategies and policies to address cybercrime on a global scale (Dupont, 2019)
The spatial distribution of digital infrastructure, including internet connectivity, data centers, and online platforms, has a significant impact on the dynamics of cybercrime (Dupont, 2017). Investigating the spatial aspects of digital infrastructure provides insights into the intersection of physical and virtual layers and the potential vulnerabilities that may influence cybercrime patterns (Mohebbi et al., 2020). By studying the geographic distribution of digital infrastructure, researchers gain a deeper understanding of how the availability and accessibility of technology shape the opportunities and risks associated with cybercriminal activities (Barn & Barn, 2016). This analysis aids in identifying geographic areas where cybercrime may be more prevalent due to variations in digital infrastructure, informing the development of targeted strategies and interventions to mitigate cybercrime risks (Choo, 2011).
Cybercrime extends beyond national borders, making it a significant transnational issue (Maghaireh, 2009). Investigating the transnational dimensions of cybercrime entails examining various aspects, including the flow of illicit funds, the role of virtual jurisdictions, cross-border cooperation among law enforcement agencies, and the geopolitical factors that influence cybercrime dynamics (Jahankhani et al., 2014). Understanding the flow of illicit funds is essential in comprehending the global nature of cybercrime and the mechanisms cybercriminals employ to transfer and launder money across international boundaries (Horgan et al., 2021). Moreover, the role of virtual jurisdictions, often used as safe havens or operating bases by cybercriminals, must be examined to grasp the complexities of transnational cybercrime (Boes & Leukfeldt, 2017).
Cross-border cooperation among law enforcement agencies is crucial in addressing transnational cybercrime (Ruohonen, 2023). Collaboration between different countries’ law enforcement agencies is necessary to share intelligence, coordinate investigations, and apprehend cybercriminals who operate across borders (Menon & Guan Siew, 2012). Additionally, understanding the geopolitical aspects that impact cybercrime dynamics helps identify the interplay between political, economic, and social factors and their influence on cybercriminal activities (Lavorgna, 2020). Investigating the transnational dimensions of cybercrime provides a comprehensive understanding of its global reach and the challenges associated with combating it (Peters & Jordan, 2019).
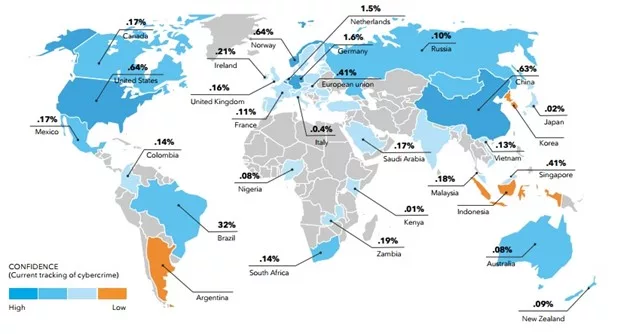
Analyzing the flows of illicit funds, the role of virtual jurisdictions, cross-border law enforcement cooperation, and geopolitical influences enable policymakers, law enforcement agencies, and international organizations to develop effective strategies and frameworks to address transnational cybercrime (Nukusheva et al., 2022). O’Callaghan (2014) demonstrates that real-time mapping provides actionable information that can be used in determining the source of attacks and further that such an approach may foster international collaboration, enhance legal frameworks, and promote information sharing, efforts to combat transnational cybercrime can be strengthened (Croasdell & Palustre, 2019).
By considering these geographical areas of interest, researchers, policymakers, and law enforcement agencies can better understand the spatial dynamics, socioeconomic factors, cultural influences, and regulatory challenges associated with cybercrime. This knowledge can inform targeted interventions and strategies to effectively prevent and mitigate cybercriminal activities. Moreover, understanding cyber-criminal activity and the demographics of these groups becomes essential in creating political policies and strategies to address cybercrime and cyber warfare (Whyte & Mazanec, 2023).
2. Background
Cybercrime and online criminal activity have become pervasive in today’s digital age, posing significant threats to individuals, organizations, and nations. Understanding the historical context of cybercrime is essential for comprehending its evolution and the challenges it presents to law enforcement agencies, policymakers, and society. This section of the paper provides an overview of the historical information behind cybercrime and online criminal activity, drawing on various scholarly sources.
2.1 Historical Information
2.1.1Emergence of Cybercrime
The origins of cybercrime can be traced back to the early days of computer technology. As computers became more accessible and interconnected, individuals with malicious intent began exploiting vulnerabilities for personal gain. As a result, the term “hacking” emerged to describe unauthorized access to computer systems, with notable cases such as the 1988 Morris Worm attack showcasing the potential impact of cybercrime (Anderson, 2020).
2.1.2 Evolution of Online Criminal Activity
The proliferation of the internet and technological advancements led to the development of sophisticated malicious software (malware) and exploits. The emergence of viruses, worms, Trojans, and other forms of malware posed significant threats to individuals and organizations worldwide (Sudhakar & Kumar, 2020). Notable instances like the ILOVEYOU virus and the Conficker worm demonstrated the devastating consequences of online criminal activities (Raff & Nicholas, 2020).
As online transactions and digital financial systems expanded, cybercriminals focused on fraud and identity theft. Techniques such as phishing, online scams, and credit card fraud became prevalent, causing substantial financial losses and compromising personal information (Holt, 2023). High-profile cases, including the Target and Yahoo data breaches, highlighted the magnitude of cyber fraud and its impact on individuals and corporations (Gundur et al., 2021).
2.1.3 Government-sponsored cyber attacks
In recent years, government-sponsored cyber attacks have gained significant attention. State actors, including intelligence agencies, engage in cyber espionage, sabotage, and disruption of critical infrastructure (Durojaye & Raji, 2022). In addition, notable incidents like the Stuxnet attack on Iranian nuclear facilities and the Russian hacking of the Democratic National Committee demonstrated the use of cyber capabilities by nation-states for political and strategic purposes (Smeets, 2022).
2.1.4 Dark web and underground marketplaces
The advent of the dark web and underground marketplaces has provided a platform for illegal activities, including selling drugs, weapons, stolen data, and hacking services. In addition, the anonymity and encryption technologies employed within these hidden online spaces have posed significant challenges to law enforcement agencies attempting to combat cybercrime (Faubert et al., 2021).
2.1.5 Conclusion
The historical information behind cybercrime and online criminal activity reveals the ever-evolving nature of these threats. From the early days of hacking to the sophisticated techniques employed by cybercriminals today, the landscape of cybercrime has continuously adapted to exploit technological advancements. In addition, government-sponsored attacks and the rise of the dark web further complicate the efforts to combat cybercrime effectively.
Understanding the historical context of cybercrime is crucial for policymakers, law enforcement agencies, and individuals to develop proactive measures and strategies. By analyzing past trends and patterns, stakeholders can gain valuable insights into the motivations, techniques, and vulnerabilities associated with cybercrime. This knowledge can inform the development of robust cybersecurity measures, international collaborations, and legal frameworks to mitigate the risks and ensure a safer digital environment.
2.2 Demographic information
Understanding the demographic and geographic aspects of cybercrime is crucial for developing effective preventive measures, allocating resources, and targeting enforcement efforts. Demographic factors, such as age, gender, education level, and socioeconomic status, can provide insights into the profiles of cybercriminals and their potential motivations. For example, research has shown that certain demographic groups, such as young adults and individuals with advanced technical skills, may be more likely to engage in cybercriminal activities. By identifying these demographic trends, law enforcement agencies and policymakers can tailor their strategies to target high-risk populations and implement educational programs to raise awareness and promote responsible online behavior.
In addition to demographics, geographic information is vital in understanding the spatial patterns and distribution of cybercrime. Geographical factors, including internet connectivity, regional economic disparities, and geopolitical dynamics, can influence the prevalence and nature of cybercriminal activities. For example, certain regions or countries may serve as cybercrime hotspots due to weak law enforcement, limited internet regulations, or political instability. Researchers can identify geographic clusters of cybercrime incidents and develop targeted interventions by analyzing geographic data, such as IP addresses, network traffic, and digital footprints. This information can help direct resources to areas with higher cybercrime rates, strengthen international cooperation in combating cyber threats, and inform policy decisions regarding cybersecurity infrastructure and regulations.
Considering both demographic and geographic aspects of cybercrime enables a comprehensive understanding of the phenomenon and facilitates effective responses. By studying the demographic characteristics of cybercriminals, policymakers can implement preventive measures that address the specific needs and vulnerabilities of different groups. Understanding the geographic distribution of cybercrime allows for targeted enforcement efforts, collaboration between jurisdictions, and the development of international frameworks to combat cyber threats effectively. Incorporating demographic and geographic perspectives in cybercrime research and policy-making ensures a more nuanced understanding of the dynamics of cybercriminal activities and supports the development of evidence-based strategies to mitigate the risks associated with cybercrime.
2.2. Socioeconomic factors
Research by Chen et al. (2023) highlights the influence of social, economic, political, and technological factors on cybercrime. The socioeconomic conditions of individuals and communities, including income disparities, unemployment rates, and educational levels, play a role in shaping the propensity for engaging in cybercriminal activities. Understanding these factors can help policymakers identify vulnerable populations and develop targeted interventions.
2.2.2 Psychological profiling
Mustapha and Bensalah (2019) provide valuable insights into the psychological profiles of cybercriminals. Their analysis of cybercriminal behavior among Moroccan youth reveals certain psychological traits and motivations, such as a desire for recognition, financial gain, and anonymity. This information aids in understanding the psychological factors that contribute to cybercriminal involvement, enabling the development of strategies to address these underlying issues.
2.2.3 Geographic profiling and targeting
The integration of geographic representation and visualization of crime scenes in cybercrime investigations, as discussed by Butkovic et al. (2019), highlights the importance of geographic data analysis. Analyzing geographic information helps identify cybercrime activity patterns, hotspots, and trends. In addition, it allows for the development of criminal geographic targeting systems, which enable law enforcement agencies to focus their resources on specific geographic areas prone to cybercrime.
2.2.4 Global distribution of cybercrime
Chen et al. (2023) emphasize using the FireHOL IP blocklist to map the global distribution of cybercrime IP addresses. This approach helps identify the geographic origins of cyberattacks and the regions with the highest concentration of cybercriminal activity. By understanding the geographic distribution, policymakers can strategically allocate resources, enhance international cooperation, and effectively implement targeted measures to combat cybercrime.
2.2.5 Conclusion
Analyzing the demographic and geographic dimensions of cybercrime provides valuable insights into the factors influencing cybercriminal behavior and the distribution of cybercrime activities. Socioeconomic factors and psychological profiling offer a deeper understanding of the individuals and communities at higher risk of engaging in cybercriminal activities. In addition, geographic profiling and the mapping of cybercrime IP addresses aid in targeting law enforcement efforts and resource allocation.
Policymakers, law enforcement agencies, and cybersecurity professionals can devise proactive strategies to prevent and combat cyber threats by comprehending the demographic characteristics and geographic patterns associated with cybercrime. In addition, collaborative international efforts, informed by this demographic and geographic analysis, can help create a safer digital environment, protect individuals and organizations, and ensure the integrity of online systems.
2.3 Environmental information
From a human geography standpoint, the environmental aspects of cybercrime play a significant role in understanding the spatial patterns and contextual factors associated with cybercriminal activities. Human geography examines the relationships between human activities and their physical and social environments. When applied to cybercrime, this perspective provides valuable insights into the geographic distribution, spatial patterns, and contextual factors that influence cybercriminal behavior. As a result, researchers and practitioners can better understand how the physical and social environment shapes cybercrime dynamics by considering the environmental dimensions.
Through human geography, the spatial patterns of cybercrime can reveal important information about its prevalence and distribution. By analyzing the geographic concentration of cybercriminal activities, researchers can identify hotspots where cybercrime incidents are more likely to occur. Factors such as population density, access to technology, and socioeconomic conditions can contribute to the spatial clustering of cybercrime. Understanding these spatial patterns allows law enforcement agencies to target resources effectively and implement localized prevention strategies.
Contextual factors, such as social and cultural environments, influence cybercriminal behavior. Human geography provides insights into the social networks, online communities, and virtual spaces where cybercriminals operate. These virtual environments offer opportunities for anonymity, collaboration, and exchanging illicit goods and services. By examining the contextual factors within these virtual spaces, researchers can better understand the motivations, interactions, and techniques cybercriminals employ.
Additionally, the physical environment can play a role in cybercrime. The availability of technology infrastructure, internet connectivity, and cyber hubs or data centers can shape the landscape of cybercriminal activities. Understanding the environmental factors that enable or facilitate cybercrime can inform policymakers and law enforcement agencies in designing effective preventive measures and regulatory frameworks.
In conclusion, the environmental aspects of cybercrime, analyzed through a human geography lens, provide valuable insights into the spatial patterns and contextual factors associated with cybercriminal activities. Researchers and practitioners can enhance their understanding of cybercrime dynamics by considering the geographic distribution, social networks, virtual spaces, and physical environment. This knowledge can inform the development of targeted prevention strategies, allocation of resources, and policy interventions to mitigate cyber threats effectively. Adopting a human geography perspective is crucial in comprehending the intricate relationship between the environment and cybercriminal behavior, ultimately contributing to developing a safer digital landscape.
2.3.1 Prevention strategies and environmental criminology in cybercrime
Miró-Llinares and Moneva (2020) emphasize the importance of developing prevention strategies for cybercrime based on environmental criminology concepts. Environmental criminology examines how the physical and social environment influences criminal behavior. By understanding the environmental factors that contribute to cybercrime, such as the availability of technology, the structure of online communities, and the accessibility of vulnerable targets, effective prevention strategies can be developed to mitigate cyber threats.
2.3.2 Application of Crime and Place Approach
Miró-Llinares and Moneva (2020) advocate applying the crime and place approach in cybercrime analysis. This approach focuses on identifying specific locations or virtual spaces where cybercrime activities are more likely to occur. By analyzing the environmental characteristics of these locations, such as the presence of online platforms, digital marketplaces, or dark web networks, law enforcement agencies can allocate resources effectively and implement targeted interventions to disrupt cybercriminal operations.
2.3.3 Impact of virtual space on criminal behavior
Hayward (2012) explores the virtual space and its impact on criminal behavior. The anonymity and global reach provided by the internet create new opportunities for cybercriminals to operate across geographical boundaries. The virtual space blurs traditional physical boundaries and enables criminal activities, such as fraud, identity theft, and hacking, to occur globally. Understanding the geographical dimensions of these virtual spaces is crucial for developing effective regulatory frameworks and international cooperation in combating cybercrime.
2.3.4 Creation of pseudo-identities in online criminal activities
Hayward (2012) also highlights interactional space in online criminal activities, wherein individuals create pseudo-identities to engage in illegal behaviors. In addition, the virtual environment allows offenders to adopt multiple online personas, making tracking their real-world identities and geographic locations difficult. Examining the interplay between virtual space and the creation of pseudo-identities provides insights into the mechanisms used by cybercriminals to evade detection and the challenges law enforcement faces in investigating and prosecuting these crimes.
2.3.5 Conclusion
Considering the environmental dimensions of cybercrime through a human geography lens provides valuable insights into the spatial patterns, contextual factors, and environmental characteristics associated with cybercriminal activities. Understanding the role of the physical and social environment in cybercrime enables the development of targeted prevention strategies, allocation of resources, and implementation of effective regulatory measures. Additionally, recognizing the impact of virtual spaces and the creation of pseudo-identities sheds light on the challenges law enforcement faces in investigating and prosecuting cybercrimes in the digital realm.
By integrating environmental perspectives from human geography, policymakers, law enforcement agencies, and cybersecurity professionals can enhance their understanding of the geographical aspects of cybercrime. This knowledge can inform the design of proactive strategies, regulations, and international collaborations to combat cyber threats effectively and create a safer digital environment for individuals and organizations.
3. Review
Cybercrime has emerged as a significant threat in the digital age, necessitating a comprehensive understanding of its various dimensions and factors. This essay synthesizes multiple studies to explore different aspects of cybercrime, including geographic profiling, socioeconomic factors, money laundering, the TOR network, virtual spaces, prevention strategies, psychological profiling, and the case study of North Korea. Each of these studies provides valuable insights into the complexities of cybercrime and contributes to developing effective countermeasures.
Geographic profiling plays a crucial role in cybercrime investigations. Butkovic et al. (2019) highlight the integration of geographic representation and visualization of crime scenes in cybercrime, enabling investigators to identify patterns and hotspots of criminal activities. Additionally, they emphasize the importance of analyzing geographic data and developing criminal geographic targeting systems, which allow for more targeted and effective law enforcement strategies.
Cybercriminal profiling is an emerging field that aims to understand the behavior and characteristics of individuals engaged in cybercrime. While traditional criminal profiling has received significant attention in the literature, cybercriminal profiling has been relatively neglected (Bada & Nurse, 2021). This essay provides an overview of the current state of cybercriminal profiling, discussing the lack of emphasis on this topic compared to traditional profiling, the research methods employed, and the introduction of GeoCrime software for geographic profiling in cybercrime investigations.
According to Bada and Nurse (2021), the existing literature predominantly focuses on criminal or offender profiling rather than cybercriminal profiling. Only a limited number of reviewed papers explicitly addressed cybercriminal profiling. This lack of emphasis highlights the need for further research and understanding in this domain (Bada & Nurse, 2021). The authors note that the reviewed papers utilized various research methods to investigate cybercriminal profiling. These methods included data collection from surveys, interviews, and existing literature. Twenty-two articles examined in the study relied on new data from surveys, interviews with criminals, law enforcement agencies, and court records. In contrast, other papers primarily relied on existing literature to explore established approaches to cybercrime (Bada & Nurse, 2021).
A significant development in cybercriminal profiling discussed by Bada and Nurse (2021) is the introduction of GeoCrime software. This software offers a valuable tool for geographic profiling in cybercrime investigations. Understanding the geographical context becomes crucial given the anonymous and location-obscuring nature of cybercrime. GeoCrime enables investigators to analyze geographic data and gain insights into the offenders’ identity and location. Its integration into cybercrime investigations enhances the ability to track and apprehend cybercriminals (Bada & Nurse, 2021).
The research on cybercriminal profiling has implications for human geography, particularly in understanding the geography of cybercrime activity. By providing a framework to determine the state-of-the-art and research position in criminological theories and the modeling of geographic data, this paper contributes to the field (Bada & Nurse, 2021). The authors argue that the limited availability of large data sets hinders the analysis of cybercrime systems across different jurisdictions. They emphasize the importance of collaboration among law enforcement officials to enhance data collection and sharing. This collaborative approach can facilitate more comprehensive investigations and aid in combating cybercrime (Bada & Nurse, 2021).
Bada and Nurse (2021). provided an overview of cybercriminal profiling, highlighting the lack of emphasis on this topic compared to traditional criminal profiling. It discussed the research methods, including data collection from surveys, interviews, and existing literature. Additionally, the introduction of GeoCrime software for geographic profiling in cybercrime investigations was examined. The implications of cybercriminal profiling for human geography were also discussed, emphasizing the need for collaborative efforts and enhanced data sharing among law enforcement officials. By understanding the behavior and characteristics of cybercriminals, we can develop effective strategies to prevent and combat cybercrime more effectively (Butkovic et al., 2019). Therefore, further research and interdisciplinary collaboration are essential to advance the cybercriminal profiling field and ensure online environment security.
The geographic concentration of cybercrime is crucial in understanding the dynamics of online criminal activities. This essay examines a study by Buil-Gil and Saldaña-Taboada (2022) that explores the analysis of criminal activity related to Bitcoin and the concentration of cybercriminals in specific geographic locations. Furthermore, it discusses the implications of these findings for law enforcement coordination and recovery procedures.
Examining the socioeconomic factors and geographic distribution of cybercrime is essential to comprehend its underlying dynamics. Chen et al. (2023) comprehensively examine the social, economic, political, and technological effects of cybercrime. Their study emphasizes using the FireHOL IP blocklist to map the global distribution of cybercrime IP addresses, providing insights into the geographical spread of cybercriminal activities.
The dark side of fintech and its relationship with money laundering is another critical aspect of cybercrime. Faccia et al. (2020) provide an overview of money-laundering scandals and the challenges existing anti-money-laundering systems face. They also highlight the role of geographic factors in facilitating illegal financial transactions, shedding light on the geographical dimensions of money laundering in the digital realm.
Analyzing the TOR network and its role in anonymizing cybercriminal activities is crucial to understanding the challenges law enforcement agencies face. Ghazi-Tehrani (2023) explores the Onion Router (TOR) network and its impact on cybercrime. Additionally, the study discusses quantifying real-world TOR usage without unmasking users, providing insights into the prevalence and characteristics of anonymous online activities. Virtual spaces have become breeding grounds for various forms of cybercrime. Hayward (2012) introduced a concept of interactional space, where individuals create pseudo-identities in online criminal activities. Understanding these virtual spaces and the creation of pseudo-identities is crucial for combating cybercrime effectively.
Developing prevention strategies and applying environmental criminology concepts are essential in combating cybercrime. Miró-Llinares and Moneva (2020) discuss developing prevention strategies and applying the crime and place approach to cybercrime analysis. Furthermore, by incorporating environmental criminology principles, such as target hardening and situational crime prevention, efforts can be made to create a more resilient digital environment.
Psychological profiling provides valuable insights into the behavior of cybercriminals. Mustapha and Bensalah (2019) analyze cybercriminal behavior among Moroccan youth, contributing to understanding the psychological factors driving their engagement in illegal online activities. The study also proposes a framework for understanding the psychological profiles of cybercriminals, facilitating the identification and targeting of individuals involved in cybercrime.
Finally, the case study of North Korea highlights the unique relationship between limited Internet connectivity and high cybercriminal activity. Pagliery (2014) examines North Korea’s restricted access to the internet and the government’s utilization of cybercrime. This case study offers insights into the geopolitical factors contributing to cybercriminal activities and law enforcement’s challenges in addressing such threats. The synthesis of various studies provides a comprehensive understanding of the multifaceted nature of cybercrime. By exploring geographic profiling, socioeconomic factors, money laundering, the TOR network
3.1.1 Analysis of criminal activity related to bitcoin
Buil-Gil and Saldaña-Taboada (2022) conducted a comprehensive analysis of criminal activity associated with Bitcoin, a popular cryptocurrency frequently exploited by cybercriminals. Their study aimed to identify geographic concentrations of cybercriminals and understand the underlying factors contributing to such concentrations. By analyzing transaction data and identifying patterns, the researchers found that specific regions exhibited higher cybercrime activity involving Bitcoin. Furthermore, this geographic concentration sheds light on the hotspots where cybercriminals are more likely to operate (Buil-Gil & Saldaña-Taboada, 2022).
3.1.2 Implications for law enforcement coordination
The study findings have significant implications for law enforcement agencies combating cybercrime. The geographic concentration of cybercriminals allows law enforcement to allocate resources effectively and prioritize their efforts in the regions most affected by cybercrime. By identifying these hotspots, law enforcement agencies can establish specialized units, develop targeted strategies, and coordinate their operations more efficiently to tackle cybercrime effectively (Buil-Gil & Saldaña-Taboada, 2022).
3.1.3 Recovery procedures and victim support
Another important aspect that Buil-Gil and Saldaña-Taboada (2022) highlight is the need to enhance recovery procedures and victim support in regions with high concentrations of cybercrime. Victims residing in these areas are more likely to be targeted, and their recovery process can be challenging. Therefore, law enforcement agencies should collaborate with local authorities, financial institutions, and support organizations to ensure swift and effective recovery for the victims. By providing necessary resources, guidance, and assistance, law enforcement can alleviate the impact of cybercrime and aid in the recovery of affected individuals and organizations (Buil-Gil & Saldaña-Taboada, 2022).
3.1.4 Collaboration and information sharing
The geographic concentration of cybercrime also highlights the importance of collaboration and information sharing among law enforcement agencies at the national and international levels. Effective coordination among agencies operating in different jurisdictions is vital to combat cybercrime and apprehending cybercriminals effectively. By sharing intelligence, best practices, and expertise, law enforcement agencies can bridge gaps in knowledge and improve their overall response to cybercrime (Buil-Gil & Saldaña-Taboada, 2022).
The geographic concentration of cybercrime provides valuable insights into the locations where cybercriminals are most active. Analyzing criminal activity related to Bitcoin helps identify these concentrations, enabling law enforcement agencies to allocate resources, coordinate efforts, and develop targeted strategies accordingly. Furthermore, these findings emphasize the need for enhanced recovery procedures and victim support in regions with high cybercrime rates. Collaboration and information sharing among law enforcement agencies are essential for effectively combating cybercrime across different jurisdictions. By understanding the geographic concentration of cybercrime, law enforcement can enhance their response and work towards creating a safer online environment (Buil-Gil & Saldaña-Taboada, 2022). Further research and continued collaboration are vital to stay ahead of cybercriminals and mitigate the risks they pose to individuals and organizations in the digital realm.
3.1.5 Geographic profiling
Geographic profiling has been used in traditional crime investigations for several decades. Recently, researchers have begun to apply geographic profiling techniques to cybercrime investigations. Butkovic et al. (2019) explain that cybercrime investigations can benefit from integrating geographic representation and visualization of crime scenes. Further, the researchers argue that geographic profiling can improve the accuracy and efficiency of cybercrime investigations.
Butkovic et al. (2019) emphasize the importance of analyzing geographic data in cybercrime investigations. They argue that analyzing geographic data can help investigators identify patterns and connections between cybercrimes. The researchers also stress the importance of developing criminal geographic targeting systems. These systems can help investigators focus on specific geographic areas or individuals likely to be involved in cybercrime.
Integrating geographic profiling in cybercrime investigations can improve the effectiveness of law enforcement efforts in combating cybercrime. By analyzing geographic data, investigators can gain insights into the behavior and patterns of cybercriminals. These insights can then be used to develop targeted prevention and intervention strategies. However, further research is needed to explore the potential of geographic profiling in cybercrime investigations fully.
3.1.6 Socioeconomic factors related to cybercrime
Technological factors do not solely influence cybercrime but are also intertwined with socioeconomic dynamics and geographic distribution. Chen et al. (2023) comprehensively examined the social, economic, political, and technological effects of cybercrime. Their research highlights the intricate relationship between these factors and the prevalence of cybercrime. By understanding these influences, policymakers and law enforcement agencies can develop more effective strategies to combat cybercriminal activities.
In their study, Chen et al. (2023) also explored using the FireHOL IP blocklist to map the global distribution of cybercrime IP addresses. This approach provides valuable insights into the geographic patterns of cybercrime activities. By analyzing the geographic distribution of cybercrime IP addresses, researchers and investigators can identify regions or countries that serve as hotspots for cybercriminal operations. This information can aid in developing targeted interventions and collaboration between jurisdictions to address cybercrime effectively.
Money laundering is a significant concern in cybercrime, particularly in fintech. Faccia et al. (2020) provide an overview of money-laundering scandals and the challenges existing anti-money laundering systems face. Their research sheds light on the vulnerabilities that cybercriminals exploit within the financial system. Furthermore, the authors emphasize the role of geographic factors in facilitating illegal financial transactions. Therefore, understanding the geographic dynamics and the influence of various jurisdictions on money laundering practices is crucial for strengthening anti-money laundering measures and international cooperation.
The synthesis of these studies demonstrates the multifaceted nature of cybercrime, highlighting the socioeconomic factors and the geographic dimension that contribute to its occurrence and proliferation. By considering the social, economic, political, and technological effects of cybercrime, policymakers can formulate comprehensive strategies to address its root causes. Moreover, using IP blocklists and examining geographic factors aid in identifying cybercrime hotspots and developing targeted interventions. Lastly, recognizing the connection between money laundering, fintech, and geographic factors is vital for enhancing anti-money laundering systems and promoting international collaboration to combat financial crimes in the digital age.
Many cyber criminals utilize the TOR (The Onion Router) network to avoid blocklists, which significantly facilitates anonymity for cybercriminal activities. Ghazi-Tehrani (2023) conducted a detailed analysis of the TOR network and its impact on cybercrime. This research sheds light on the mechanisms and techniques used within the TOR network to anonymize the activities of cybercriminals. Understanding the functionality of the TOR network is crucial for law enforcement agencies and policymakers in their efforts to combat cybercrime effectively.
Ghazi-Tehrani (2023) also explores the challenge of quantifying real-world TOR usage without unmasking users. This aspect is crucial as it allows researchers and investigators to gather insights into the prevalence and extent of TOR usage in cybercriminal activities without compromising the anonymity of TOR users. Furthermore, stakeholders can better understand the scale and scope of cybercriminal operations that leverage the TOR network by quantifying TOR usage.
Considering the previous discussion on socioeconomic factors, geographic distribution, and money laundering concerning cybercrime, the analysis of the TOR network and its role in anonymizing cybercriminal activities adds another layer of complexity to the landscape. The TOR network enables cybercriminals to obfuscate their identities and locations, making it even more challenging for law enforcement agencies and policymakers to investigate and prosecute cybercrimes effectively.
By examining the TOR network and developing methods to quantify TOR usage without unmasking users, researchers can enhance their understanding of the magnitude of cybercriminal activities occurring within this anonymizing network. This knowledge can inform the development of targeted strategies and collaborative efforts among international stakeholders to address the challenges posed by the TOR network in combating cybercrime.
Hence, the analysis of the TOR network and its anonymity features contributes to our understanding of cybercrime by highlighting the mechanisms employed by cybercriminals to evade detection. In addition, the examination of the TOR network and the ability to quantify its usage without compromising user anonymity provides valuable insights for researchers, investigators, and policymakers. Integrating this knowledge with the previously discussed socioeconomic factors, geographic distribution, and money laundering considerations will contribute to more effective strategies in combating cybercrime and ensuring a safer digital environment.
3.1.7 Prevention strategies and environmental criminology in cybercrime
Developing effective prevention strategies is crucial in combating cybercrime, which continues to pose significant threats to individuals, organizations, and societies. Miró-Llinares and Moneva (2020) explore developing prevention strategies and applying environmental criminology concepts to cybercrime analysis, shedding light on innovative approaches to address this ever-evolving challenge.
In their study, Miró-Llinares and Moneva (2020) delve into developing prevention strategies specifically tailored to cybercrime. Recognizing the dynamic nature of cyber threats, the researchers emphasize the need for proactive measures encompassing a comprehensive understanding of the cybercriminal landscape. By integrating insights from various fields, including criminology, psychology, technology, and law enforcement, the study identifies key strategies to mitigate cybercrime risks effectively. These strategies encompass technological measures, such as robust security systems and encryption protocols, and educational initiatives to raise awareness among individuals and organizations. By adopting a multifaceted approach, prevention strategies can address the diverse range of cybercriminal activities and adapt to emerging threats.
Furthermore, Miró-Llinares and Moneva (2020) explore applying environmental criminology concepts to cybercrime analysis. The crime and place approach, widely used in traditional criminology, is adapted to the cyber realm. This approach focuses on understanding the spatial and temporal patterns of cybercriminal activities, identifying the factors contributing to their occurrence. This approach provides insights into the situational contexts that enable cybercriminal behaviour by examining the physical and virtual environments, including the characteristics of online platforms, social networks, and communication channels. Understanding these environmental factors can guide the development of targeted interventions and the implementation of preventive measures to disrupt cybercrime networks effectively.
The insights gained from developing prevention strategies and applying environmental criminology concepts have significant implications for addressing cybercrime. By adopting a proactive and multi-disciplinary approach, prevention strategies can stay ahead of evolving cyber threats. Integrating environmental criminology concepts allows for a deeper understanding of the contextual factors that influence cybercriminal behavior, facilitating the design of targeted interventions. Collaboration between stakeholders, including law enforcement agencies, policymakers, industry professionals, and academia, is vital in implementing and continuously adapting these strategies to the ever-changing cyber landscape.
It is important to note that the field of cybercrime prevention and environmental criminology in the digital realm is still evolving. Therefore, continued research, innovation, and knowledge-sharing are essential to stay abreast of emerging cyber threats and develop effective prevention strategies. Furthermore, as cybercriminals constantly adapt their tactics, it is crucial for prevention efforts to keep pace with technological advancements and address the socio-technical aspects of cybercrime.
In conclusion, developing prevention strategies and applying environmental criminology concepts to cybercrime analysis, as Miró-Llinares and Moneva (2020) explored, offer valuable insights into combating cyber threats. By integrating insights from various disciplines and understanding the situational contexts of cybercriminal activities, prevention strategies can be tailored to address the diverse challenges of cybercrime. The proactive and multi-disciplinary nature of these strategies emphasizes the need for collaboration among stakeholders to effectively protect individuals, organizations, and societies from the detrimental impacts of cybercrime. Continued research and innovation are crucial to adapt prevention efforts to the ever-changing cyber landscape and ensure a safer digital environment.
Understanding the psychological profiles of individuals engaged in cybercriminal behavior is crucial for developing effective prevention strategies and interventions. In their study, Mustapha and Bensalah (2019) conducted an analysis specifically focusing on cybercriminal behavior among Moroccan youth, providing valuable insights into this domain. Furthermore, they proposed a framework for comprehending the psychological profiles of cybercriminals. The analysis by Mustapha and Bensalah (2019) examined the behavior of Moroccan youth involved in cybercrime. The study shed light on the factors contributing to their engagement in such activities, including social, economic, and technological influences. Furthermore, by investigating the motivations, risk factors, and modus operandi of these individuals, the researchers were able to identify patterns and characteristics that shape their cybercriminal behavior. The study’s findings contribute to a better understanding of the underlying psychological dynamics involved in cybercriminal activities among Moroccan youth.
In addition to the analysis, Mustapha and Bensalah (2019) proposed a framework for understanding the psychological profiles of cybercriminals. This framework provides a structured approach to identifying and analyzing key psychological factors that may influence individuals to engage in cybercrime. By examining various dimensions, such as personality traits, motivations, cognitive processes, and social interactions, the framework helps construct a comprehensive understanding of the psychological profiles of cybercriminals. This knowledge can guide the development of targeted interventions, prevention strategies, and rehabilitation programs to reduce cybercriminal behavior.
The insights gained from the analysis and the framework proposed by Mustapha and Bensalah (2019) have important implications for addressing cybercrime effectively. Understanding the psychological profiles of cybercriminals enables law enforcement agencies, policymakers, and cybersecurity professionals to tailor their approaches accordingly. By targeting the underlying psychological factors, interventions can be designed to deter potential cybercriminals, rehabilitate those involved in cybercrime, and create a safer digital environment for individuals and organizations.
Moreover, this research emphasizes the need for interdisciplinary collaboration in combating cybercrime. Integrating psychological profiling with other fields, such as criminology, sociology, and technology, allows for a comprehensive understanding of the multifaceted nature of cybercriminal behavior. In addition, it highlights the importance of considering individual vulnerabilities, societal influences, and technological factors in developing effective prevention and intervention strategies.
In conclusion, the analysis of cybercriminal behavior among Moroccan youth conducted by Mustapha and Bensalah (2019) and their framework for understanding the psychological profiles of cybercriminals provide valuable insights into this complex field. By identifying key factors and proposing a structured approach, the research contributes to a better understanding of the psychological dynamics underlying cybercriminal activities. This knowledge can inform the development of targeted interventions, prevention strategies, and rehabilitation programs. Furthermore, the interdisciplinary nature of this research emphasizes the importance of collaboration among different disciplines to effectively address cybercrime and foster a safer digital environment for individuals and societies.
North Korea’s unique case study provides valuable insights into the relationship between limited Internet connectivity and high cybercriminal activity. Pagliery (2014) explores the examination of North Korea’s restricted access to the Internet and its impact on cybercrime. The country’s limited connectivity presents an intriguing scenario, where despite the constraints, North Korea has been associated with various cybercriminal activities.
North Korea’s government has been found to utilize cybercrime as a tool for different purposes. While specific details may be limited due to the secretive nature of the regime, there have been indications of state-sponsored cyberattacks originating from North Korea. These cyberattacks have targeted various entities, including governments, organizations, and individuals, for espionage, disruption, or financial gain. The government’s involvement in cybercrime demonstrates how connectivity restrictions can lead to the concentration of cybercriminal activities, where a state-sponsored approach can exploit vulnerabilities and launch sophisticated attacks.
The combination of limited Internet connectivity and government utilization of cybercrime in North Korea presents a complex and challenging environment. Restricted access to the Internet can act as a barrier to cyber defense mechanisms and international cooperation in combating cybercrime. Moreover, the government’s involvement introduces a state-sanctioned dimension to cybercriminal activities, further complicating the landscape and highlighting the need for global collaboration to address such threats effectively.
Understanding the case study of North Korea offers valuable lessons in dealing with the interplay between connectivity and cybercrime. It emphasizes the importance of striking a balance between promoting connectivity for societal benefits and implementing robust cybersecurity measures to mitigate the risks associated with cybercriminal activities. Governments and international organizations must work together to address the challenges posed by states that exploit cybercrime for their strategic objectives.
In conclusion, examining North Korea’s limited Internet connectivity and government utilization of cybercrime sheds light on the complex dynamics between connectivity and cybercriminal activities. The case study highlights the need for a comprehensive approach combining technological advancements, policy measures, and international cooperation to combat cybercrime from countries with limited connectivity effectively. By understanding the nuances of such scenarios, stakeholders can develop strategies and frameworks that enhance cybersecurity and protect individuals, organizations, and nations from the adverse effects of cybercrime in both connected and less-connected environments.
4. Conclusion
The comprehensive exploration of various aspects of cybercrime and its geographical dimensions provides valuable insights into the nature and dynamics of online criminal activities. Researchers have highlighted the significance of analyzing geographic data and developing criminal geographic targeting systems by integrating geographic profiling into cybercrime investigations. For example, the works of Butkovic et al. (2019) emphasize the importance of incorporating geographic representation and visualization of crime scenes in cybercrime investigations.
Furthermore, socioeconomic factors play a pivotal role in the geographic distribution of cybercrime. Chen et al. (2023) shed light on the social, economic, political, and technological effects influencing cybercrime activities. Their use of the FireHOL IP blocklist to map the global distribution of cybercrime IP addresses demonstrates the relevance of geographic factors in understanding the spread and prevalence of cybercriminal activities.
The dark side of fintech and money laundering in cybercrime pose significant challenges to existing anti-money laundering systems. Faccia et al. (2020) provide an overview of money-laundering scandals and emphasize the role of geographic factors in facilitating illegal financial transactions. In addition, the examination of the TOR network and anonymity in cybercrime by Ghazi-Tehrani (2023) highlights the critical role played by the Onion Router network in anonymizing cybercriminal activities while presenting methodologies for quantifying real-world TOR usage without compromising user identities.
Virtual spaces have also emerged as a prominent arena for cybercriminal activities, where creating pseudo-identities and exploring interactional space contribute to criminal behavior. Hayward (2012) explores the impact of virtual space on criminal behavior and emphasizes the importance of understanding the geographical dimensions of online criminal activities. Prevention strategies and environmental criminology concepts have been developed to address the challenges posed by cybercrime. Miró-Llinares and Moneva (2020) highlight the significance of applying the crime and place approach to cybercrime analysis and developing prevention strategies rooted in environmental criminology.
Understanding the psychological profiles of cybercriminals is another critical aspect of combating cybercrime. Mustapha and Bensalah (2019) analyze cybercriminal behavior among Moroccan youth and provide a framework for understanding the psychological profiles of cybercriminals, offering insights into the motives and behaviors driving online criminal activities. Lastly, the unique case study of North Korea demonstrates the correlation between limited Internet connectivity and high cybercriminal activity. Pagliery (2014) explores the North Korean government’s utilization of cybercrime as a tool for various purposes, highlighting the intersection of connectivity, state operations and cybercriminal activities.
In conclusion, the synthesis of research on geographic profiling, socioeconomic factors, money laundering, TOR network, virtual spaces, prevention strategies, psychological profiling, and connectivity provides a comprehensive understanding of the geographical dimensions of cybercrime. The insights gained from these studies contribute to developing effective strategies and measures for law enforcement agencies, policymakers, and researchers to combat cybercrime and create a safer digital environment for individuals and organizations worldwide. Continued research and collaboration in this field are crucial to keep pace with evolving cybercriminal tactics and ensure the effectiveness of future prevention and enforcement efforts.
5. References
Abdulai, M. A. (2022). The Paradox of Cybercrime Risk and Internet Use in Canada: A Socio-Criminological Perspective [Thesis, University of Saskatchewan]. https://harvest.usask.ca/handle/10388/14294
Anderson, R. (2020). Security Engineering: A Guide to Building Dependable Distributed Systems. John Wiley & Sons.
Asmar, A., Mariën, I., & Van Audenhove, L. (2022). No one-size-fits-all! Eight profiles of digital inequalities for customized inclusion strategies. New Media & Society, 24(2), 279–310. https://doi.org/10.1177/14614448211063182
Bada, M., & Nurse, J. R. C. (2021). Profiling the Cybercriminal: A Systematic Review of Research. 2021 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), 1–8. https://doi.org/10.1109/CyberSA52016.2021.9478246
Barn, R., & Barn, B. (2016, June 12). An ontological representation of a taxonomy for cybercrime. 24th European Conference on Information Systems (ECIS 2016), Istanbul, Turkey. http://aisel.aisnet.org/ecis2016_rp/45
Boes, S., & Leukfeldt, E. R. (2017). Fighting Cybercrime: A Joint Effort. In R. M. Clark & S. Hakim (Eds.), Cyber-Physical Security: Protecting Critical Infrastructure at the State and Local Level (pp. 185–203). Springer International Publishing. https://doi.org/10.1007/978-3-319-32824-9_9
Broadhurst, R. (2006). Developments in the global law enforcement of cyber‐crime. Policing: An International Journal of Police Strategies & Management, 29(3), 408–433. https://doi.org/10.1108/13639510610684674
Buil-Gil, D., & Saldaña-Taboada, P. (2022). Offending Concentration on the Internet: An Exploratory Analysis of Bitcoin-related Cybercrime. Deviant Behavior, 43(12), 1453–1470. https://doi.org/10.1080/01639625.2021.1988760
Burke, C. (2014). Virtual Communities and the Anarchist Movement: An analysis of WikiLeaks, Anonymous and Bitcoin. [PhD Thesis]. Loughborough University.
Butkovic, A., Mrdovic, S., Uludag, S., & Tanovic, A. (2019). Geographic profiling for serial cybercrime investigation. Digital Investigation, 28, 176–182. https://doi.org/10.1016/j.diin.2018.12.001
Chen, S., Hao, M., Ding, F., Jiang, D., Dong, J., Zhang, S., Guo, Q., & Gao, C. (2023). Exploring the global geography of cybercrime and its driving forces. Humanities and Social Sciences Communications, 10(1), 71. https://doi.org/10.1057/s41599-023-01560-x
Choo, K.-K. R. (2011). The cyber threat landscape: Challenges and future research directions. Computers & Security, 30(8), 719–731. https://doi.org/10.1016/j.cose.2011.08.004
Collier, B., Thomas, D. R., Clayton, R., Hutchings, A., & Chua, Y. T. (2022). Influence, infrastructure, and recentering cybercrime policing: Evaluating emerging approaches to online law enforcement through a market for cybercrime services. Policing and Society, 32(1), 103–124. https://doi.org/10.1080/10439463.2021.1883608
Croasdell, D., & Palustre, A. (2019). Transnational Cooperation in Cybersecurity. http://hdl.handle.net/10125/59996
Dijk, J. van. (2020). The Digital Divide. John Wiley & Sons.
Dupont, B. (2017). Bots, cops, and corporations: On the limits of enforcement and the promise of polycentric regulation as a way to control large-scale cybercrime. Crime, Law and Social Change, 67(1), 97–116. https://doi.org/10.1007/s10611-016-9649-z
Dupont, B. (2019). Enhancing the effectiveness of cybercrime prevention through policy monitoring. Journal of Crime and Justice, 42(5), 500–515. https://doi.org/10.1080/0735648X.2019.1691855
Durojaye, H., & Raji, O. (2022). Impact of State and State Sponsored Actors on the Cyber Environment and the Future of Critical Infrastructure (arXiv:2212.08036). arXiv. https://doi.org/10.48550/arXiv.2212.08036
Faccia, A., Moşteanu, N. R., Cavaliere, L. P. L., & Mataruna-Dos-Santos, L. J. (2020). Electronic Money Laundering, The Dark Side of Fintech: An Overview of the Most Recent Cases. Proceedings of the 2020 12th International Conference on Information Management and Engineering, 29–34. https://doi.org/10.1145/3430279.3430284
Faubert, C., Décary-Hétu, D., Malm, A., Ratcliffe, J., & Dupont, B. (2021). Law Enforcement and Disruption of Offline and Online Activities: A Review of Contemporary Challenges. In M. Weulen Kranenbarg & R. Leukfeldt (Eds.), Cybercrime in Context: The human factor in victimization, offending, and policing (pp. 351–370). Springer International Publishing. https://doi.org/10.1007/978-3-030-60527-8_19
Foley, S., Karlsen, J. R., & Putniņš, T. J. (2019). Sex, drugs, and bitcoin: How much illegal activity is financed through cryptocurrencies? The Review of Financial Studies, 32(5), 1798–1853.
Frank, R., & Mikhaylov, A. (2020). Beyond the ‘Silk Road’: Assessing Illicit Drug Marketplaces on the Public Web. In M. A. Tayebi, U. Glässer, & D. B. Skillicorn (Eds.), Open Source Intelligence and Cyber Crime: Social Media Analytics (pp. 89–111). Springer International Publishing. https://doi.org/10.1007/978-3-030-41251-7_4
Friend, C., Grieve, L. B., Kavanagh, J., & Palace, M. (2020). Fighting Cybercrime: A Review of the Irish Experience. International Journal of Cyber Criminology, 14(2), 383–399.
Ghazi-Tehrani, A. K. (2023). Mapping Real-World Use of the Onion Router. Journal of Contemporary Criminal Justice, 104398622311575. https://doi.org/10.1177/10439862231157553
Gundur, R. V., Levi, M., Topalli, V., Ouellet, M., Stolyarova, M., Chang, L. Y.-C., & Mejía, D. D. (2021). Evaluating Criminal Transactional Methods in Cyberspace as Understood in an International Context. In CrimRxiv. https://doi.org/10.21428/cb6ab371.5f335e6f
Hall, T., Sanders, B., Bah, M., King, O., & Wigley, E. (2021). Economic geographies of the illegal: The multiscalar production of cybercrime. Trends in Organized Crime, 24(2), 282–307. https://doi.org/10.1007/s12117-020-09392-w
Hayward, K. J. (2012). Five Spaces of Cultural Criminology. British Journal of Criminology, 52(3), 441–462. https://doi.org/10.1093/bjc/azs008
Ho, H., Ko, R., & Mazerolle, L. (2022). Situational Crime Prevention (SCP) techniques to prevent and control cybercrimes: A focused systematic review. Computers & Security, 115, 102611. https://doi.org/10.1016/j.cose.2022.102611
Holt, T. J. (2023). Understanding the state of criminological scholarship on cybercrimes. Computers in Human Behavior, 139, 107493. https://doi.org/10.1016/j.chb.2022.107493
Horgan, S., Collier, B., Jones, R., & Shepherd, L. (2021). Re-territorializing the policing of cybercrime in the post-COVID-19 era: Towards a new vision of local democratic cyber policing. Journal of Criminal Psychology, 11(3), 222–239. https://doi.org/10.1108/JCP-08-2020-0034
Ife, C. C., Davies, T., Murdoch, S. J., & Stringhini, G. (2022). Bridging Information Security and Environmental Criminology Research to Better Mitigate Cybercrime (arXiv:1910.06380). arXiv. https://doi.org/10.48550/arXiv.1910.06380
Jahankhani, H., Al-Nemrat, A., & Hosseinian-Far, A. (2014). Chapter 12—Cybercrime classification and characteristics. In B. Akhgar, A. Staniforth, & F. Bosco (Eds.), Cyber Crime and Cyber Terrorism Investigator’s Handbook (pp. 149–164). Syngress. https://doi.org/10.1016/B978-0-12-800743-3.00012-8
Kethineni, S., Cao, Y., & Dodge, C. (2018). Use of Bitcoin in Darknet Markets: Examining Facilitative Factors on Bitcoin-Related Crimes. American Journal of Criminal Justice, 43(2), 141–157. https://doi.org/10.1007/s12103-017-9394-6
Koziarski, J., & Lee, J. R. (2020). Connecting evidence-based policing and cybercrime. Policing: An International Journal, 43(1), 198–211. https://doi.org/10.1108/PIJPSM-07-2019-0107
Kraemer-Mbula, E., Tang, P., & Rush, H. (2013). The cybercrime ecosystem: Online innovation in the shadows? Technological Forecasting and Social Change, 80(3), 541–555. https://doi.org/10.1016/j.techfore.2012.07.002
Lavorgna, A. (2020). Cybercrimes: Critical Issues in a Global Context. Bloomsbury Publishing.
Lusthaus, J., Bruce, M., & Phair, N. (2020). Mapping the Geography of Cybercrime: A Review of Indices of Digital Offending by Country. 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), 448–453. https://doi.org/10.1109/EuroSPW51379.2020.00066
Maghaireh, A. (2009). Jordanian cybercrime investigations: A comparative analysis of search for and seizure of digital evidence. University of Wollongong Thesis Collection 1954-2016. https://ro.uow.edu.au/theses/3402
Márquez Carrasco, C., Churruca Muguruza, C., & Alamillos Sánchez, R. (2016). Case study: Common Security and Defence Policy (CSDP). FRAME. https://doi.org/20.500.11825/97
Menon, S., & Guan Siew, T. (2012). Key challenges in tackling economic and cyber crimes: Creating a multilateral platform for international cooperation. Journal of Money Laundering Control, 15(3), 243–256. https://doi.org/10.1108/13685201211238016
Miró-Llinares, F., & Moneva, A. (2020). Environmental Criminology and Cybercrime: Shifting Focus from the Wine to the Bottles. In T. J. Holt & A. M. Bossler (Eds.), The Palgrave Handbook of International Cybercrime and Cyberdeviance (pp. 491–511). Springer International Publishing. https://doi.org/10.1007/978-3-319-78440-3_30
Mohebbi, S., Zhang, Q., Christian Wells, E., Zhao, T., Nguyen, H., Li, M., Abdel-Mottaleb, N., Uddin, S., Lu, Q., Wakhungu, M. J., Wu, Z., Zhang, Y., Tuladhar, A., & Ou, X. (2020). Cyber-physical-social interdependencies and organizational resilience: A review of water, transportation, and cyber infrastructure systems and processes. Sustainable Cities and Society, 62, 102327. https://doi.org/10.1016/j.scs.2020.102327
Mustapha, E. H., & Bensalah, F. (2019). Cybercrime in Morocco A Study of the Behaviors of Moroccan Young People Face to the Digital Crime. International Journal of Advanced Computer Science and Applications, 10, 457. https://doi.org/10.14569/IJACSA.2019.0100457
Nouh, M., Nurse, J. R. C., Webb, H., & Goldsmith, M. (2019). Cybercrime Investigators are Users Too! Understanding the Socio-Technical Challenges Faced by Law Enforcement. Proceedings 2019 Workshop on Usable Security. https://doi.org/10.14722/usec.2019.23032
Nukusheva, A., Zhamiyeva, R., Shestak, V., & Rustembekova, D. (2022). Formation of a legislative framework in the field of combating cybercrime and strategic directions of its development. Security Journal, 35(3), 893–912. https://doi.org/10.1057/s41284-021-00304-3
O’Callaghan, J. (2014, June 26). Map shows the amount of cyber attacks around the world in real time. Mail Online. https://www.dailymail.co.uk/sciencetech/article-2670710/Think-youre-safe-internet-Think-Map-reveals-millions-cyber-attacks-happening-world-real-time.html
Only 37% of the organizations have cyber incident response plan. (2017, January 24). SAFETY4SEA. https://safety4sea.com/only-37-of-the-organizations-have-cyber-incident-response-plan/
Onyeneke, C. C., & Karam, A. H. (2022). An Exploratory Study of Crime: Examining Lived Experiences of Crime through Socioeconomic, Demographic, and Physical Characteristics. Urban Science, 6(3), Article 3. https://doi.org/10.3390/urbansci6030043
Pagliery, J. (2014, December 22). A peek into North Korea’s Internet. CNNMoney. https://money.cnn.com/2014/12/22/technology/security/north-korean-internet/index.html
Park, J., Cho, D., Lee, J. K., & Lee, B. (2019). The Economics of Cybercrime: The Role of Broadband and Socioeconomic Status. ACM Transactions on Management Information Systems, 10(4), 1–23. https://doi.org/10.1145/3351159
Peters, A., & Jordan, A. (2019). Countering the Cyber Enforcement Gap: Strengthening Global Capacity on Cybercrime. Journal of National Security Law and Policy, 10(3), 487–524.
Qi, Q., Chen, G., Ye, F., Lin, Z., & Liu, Q. (2022). Intelligence Analysis of Crime of Helping Cybercrime Delinquency Based on Knowledge Ggraph. 2022 IEEE 5th Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), 5, 690–695. https://doi.org/10.1109/IMCEC55388.2022.10019848
Raff, E., & Nicholas, C. (2020). A Survey of Machine Learning Methods and Challenges for Windows Malware Classification (arXiv:2006.09271). arXiv. https://doi.org/10.48550/arXiv.2006.09271
Ragatz, L., & Fremouw, W. (2010). A Critical Examination of Research on the Psychological Profiles of White-Collar Criminals. Journal of Forensic Psychology Practice, 10(5), 373–402. https://doi.org/10.1080/15228932.2010.489846
Robinson, L., Cotten, S. R., Ono, H., Quan-Haase, A., Mesch, G., Chen, W., Schulz, J., Hale, T. M., & Stern, M. J. (2015). Digital inequalities and why they matter. Information, Communication & Society, 18(5), 569–582. https://doi.org/10.1080/1369118X.2015.1012532
Ruohonen, J. (2023). Recent Trends in Cross-Border Data Access by Law Enforcement Agencies (arXiv:2302.09942). arXiv. https://doi.org/10.48550/arXiv.2302.09942
Smeets, M. (2022). No Shortcuts: Why States Struggle to Develop a Military Cyber-Force. Oxford University Press.
Stein, A. A. (1982). Coordination and collaboration: Regimes in an anarchic world. International Organization, 36(2), 299–324. https://doi.org/10.1017/S0020818300018968
Stoddart, K. (2022). Non and Sub-State Actors: Cybercrime, Terrorism, and Hackers. In K. Stoddart (Ed.), Cyberwarfare: Threats to Critical Infrastructure (pp. 351–399). Springer International Publishing. https://doi.org/10.1007/978-3-030-97299-8_6
Sudhakar, & Kumar, S. (2020). An emerging threat Fileless malware: A survey and research challenges. Cybersecurity, 3(1), 1. https://doi.org/10.1186/s42400-019-0043-x
Tompsett, B. C., Marshall, A. M., & Semmens, N. C. (2005). Cyberprofiling: Offender profiling and geographic profiling of crime on the internet. Workshop of the 1st International Conference on Security and Privacy for Emerging Areas in Communication Networks, 2005., 22–25. https://doi.org/10.1109/SECCMW.2005.1588290
Vandeviver, C., & Bernasco, W. (2017). The geography of crime and crime control. Applied Geography, 86, 220–225. https://doi.org/10.1016/j.apgeog.2017.08.012
Whyte, C., & Mazanec, B. M. (2023). Understanding Cyber-Warfare: Politics, Policy and Strategy. Taylor & Francis.
Zagaris, B., & Mostaghimi, A. (2022). Transnational Fraud and Cybercrime. International Enforcement Law Reporter, 38, 460.
Watch: William Callahan: Blockchain as a valuable tool for law enforcement

 02-23-2026
02-23-2026 




