|
Getting your Trinity Audio player ready...
|
This article was first published on Dr. Craig Wright’s blog, and we republished with permission from the author.
Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending…
The Bitcoin white paper notes the use of a digital signature algorithm and its need to prevent the deployment of trusted third parties or alternative systems. Yet, in systems such as the BTC Core network, alternative systems have been developed, including the Lightning Network (Antonopoulos et al., 2021) and SegWit (Pérez-Solà et al., 2019), whereby the requirement for a third party has been reintroduced (Faltibà, 2018, p. 16).
As the second sentence of the Bitcoin white paper notes, digital signatures provide part of the solution. This aspect of Bitcoin in itself is not new. Wayner (1996) documented multiple requirements for digital signatures (Wayner, 1996, p. 28) and digital signature algorithms (Wayner, 1996, p. 18), and multiple forms of digital or electronic cash, over a decade—before the launch of Bitcoin. One solution from this time involves signature-only public-key systems (Wayner, 1996, p. 17).
Wayner defines the use of signature-only public-key systems (1996, p. 17), noting that a system that can be used to verify a signature, but that is not used in encrypting messages and hence “keeping them out of the eyes and ears of the police”, can be created in a way that does not “tend(s) to annoy some governments that want to control the use of encryption”. Such systems differ from blinded digital signatures, which are used in creating anonymous cash (Wayner, 1996, p. 18).
As the second sentence of the white paper notes, “digital signatures provide part of the solution”. Many other aspects of Bitcoin are required to make it secure and functioning. Yet, some of the benefits remain misunderstood. Primarily, Bitcoin is a micropayment system. The system aims to provide the capability for electronic cash that can be distributed as “small casual transactions” (Wright, 2008, p. 1). At the same time, for large-value transactions, money laundering and financial-transaction rules require the use of intermediaries (Geiger & Wuensch, 2007).
Bryans (2014) noted that Bitcoin requires anti-money laundering (AML) provisions and that AML enforcement requires that large-value transactions (generally over USD10,000) require reporting and intermediaries. Such requirements are necessary for cash-based payments, too. In other words, the introduction of Bitcoin doesn’t mitigate such requirements. As cash in its physical form can be used for money laundering, the argument that Bitcoin is different because it’s cash-like is nonsensical. Rather, Bitcoin is cash-like, and thus necessitates using the same rules that exist for cash transactions. The distinction is that bitcoin is completely traceable, and any transactions that are made for large values can easily be monitored and reported. In accordance with the Bitcoin white paper, “[a]ny needed rules and incentives can be enforced with this consensus mechanism” (Wright, 2008, p. 8).
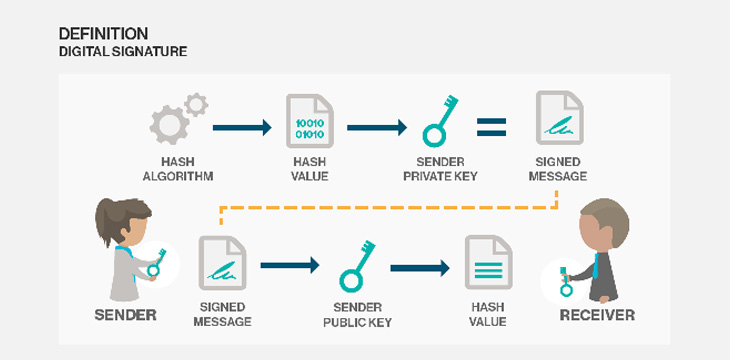
What is a digital signature
The various definitions and requirements related to electronic signatures and identities are documented in detail by Brazell (2018). In this work on electronic signatures and identities, the author documents the standards, technical requirements, identity issues, and jurisdictional challenges associated with digital signatures. Such definitions are provided in a global context. In the “new privacy model” (Wright, 2008, p. 6) provided through Bitcoin, identities remain a necessary part of the solution. The distinction is that the public can see somebody sending information but cannot link it to anyone.
Such a privacy model does not remove the necessity for identity (Bryans, 2014). Rather, the new privacy model offered by Bitcoin allows individuals to exchange identities where needed, and to a level that is needed. For example, two individuals engaged in a small trade, such as involving the purchase of a coffee, do not need to exchange a lot of information. Instead, the coffee shop can provide information concerning the business identity in the form of an invoice, and the user can be treated as someone paying in cash. In such a way, the transaction level dictates how much information must be exchanged, and none of the information must be put on-chain.
Signatures can always be repudiated (Brazell, 2018, p. 298). Repudiation, or non-repudiation, is not a technical issue, and anyone attempting to create non-repudiation through technical methodologies has failed to understand the legal requirements (Brazell, 2018, p. 90). As Brazell (2018, pp. 90–91) notes in section 4-054:
It is widely believed that a digital signature reduces the freedom of the signatory to repudiate an electronic signature on any grounds other than those equally available in respect of handwritten signatures, namely mistake, duress and the like. However, this is not the case because of the digital signature’s inability to identify the signatory. A digital signature only provides what a key was used to sign, not the circumstances under which it was used. This gap between signature and signatory leads to the need for legal assignment of responsibility for the consequences of signature, which is addressed in the UNCITRAL Model Law on electronic signatures. A biometric, on the other hand, may provide genuine non-reputability.
Nevertheless, as this review shows digital signatures have no particular advantage over other forms of electronic signature in respect of many of the functions for which a handwritten signature is used, and in particular, are significantly flawed when it comes to the function of identifying the signatory with confidence. In order to produce an electronic signature which can perform all the functions of a handwritten signature, a combination of biometric and digital signature technology is required.
Bitcoin can function as cash, for small incontestable values, where the cost of seeking to repudiate the transaction exceeds the value of the amount exchanged, compared to the amount needed to go to court and contest the exchange. For amounts under $10,000, there will be little possibility of recovering funds in any meaningful way. Even in small-claims courts, the recovery cost will exceed any benefit gained by seeking a court order to recover money distributed across Bitcoin. Conversely, for large amounts, it is possible to create a strategy for alerting nodes to reject blocks that have been frozen by court order.
“One such strategy to protect against this would be to accept alerts from network nodes when they detect an invalid block, prompting the user’s software to download the full block and alerted transactions to confirm the inconsistency” (Wright, 2008, p. 5). For example, creating a block that implements and allows a transaction from a frozen UTXO would be considered invalid. The process can be automated, allowing nodes to easily take action when it comes to criminal funds or money that has been seized through a court order.
Such a process would be completed in two parts, namely the freezing and the reallocation of funds. Yet, as noted above (Brazell, 2018), non-repudiation is not something that is at all possible in electronic systems, so it remains something that is legally required to be reversible through court-based processes. Importantly, the Bitcoin white paper does not note that the system protects possession, but rather says that it protects “ownership.”
The main benefits discussed in the Bitcoin white paper are related to the use of the system as electronic cash. When there are third parties, the system requires a means of managing access and uses that is more expensive than what can be delivered in Bitcoin. Here, rather than having an electronic cash system, “small casual payments”, we end up with a digital gold system that is expensive and less effective than banks and the existing financial infrastructure. The Holy Grail of the internet was always digital cash (Wayner, 1996). The distinction with Bitcoin is that rather than presenting an untraceable, anonymous system, such as eCash (Chaum, 1983), Bitcoin presented a private or pseudonymous system that maintains ends and traceability.
The distinction between such ideas, between a cryptocurrency, such as eCash, and digital cash, or an electronic cash system, is exemplified in Bitcoin. Bitcoin is private and pseudonymous. But, the nature of Bitcoin does not mitigate the need for identity. Brazell (2018, pp. 37–62) documented the requirements for identity and its reference to digital signatures. The key aspect of Bitcoin that many people forget or fail to understand is that a digital signature requires an identity.
The UNCITRAL Model Law on Electronic Signatures (2001) formed the foundation for much of the digital signature legislation enacted worldwide, including within the USA and the U.K. The European provisions also follow the model law. In each instance, it is important to note that a key function of a signature includes “identifying the author or sender of a document” (Brazell, 2018, p. 15). So, the use of digital signatures is not merely referred to as the use of a digital signature algorithm. A digital signature algorithm is a technological system that provides the capability to create a digital signature, but is not in itself a digital signature.
A digital signature still requires an identity. For high-end and high-value transactions, identity can be provided through certificate authorities and public key infrastructure (Hunt, 2001). Yet, for low-value transactions, it becomes possible to create a web of trust (Caronni, 2000) where detailed information about individuals is not required, or partial identities are exchanged (Brazell, 2018, pp. 39–40). The use of full or partial identities will be predicated on the size of the transaction and the level of necessity to exchange identity information in each scenario.
As Caronni (2000) observed, a web of trust allows a user of the system to choose, for him- or herself, who they deem to be trustworthy. In the exchange of small-value, casual transactions, the ability to facilitate an irreversible exchange is important. If an individual purchases a small-value item, the individual can still request a refund and negotiate accordingly—as with cash. The interactions between individuals using electronic cash do not change significantly compared to physical cash.
In the sentence of the white paper, the referenced requirement is to create a digital signature system. Here, keys may be derived using the homomorphic properties of ECDSA that allow a subkey to be created (Wright & Savanah, 2022). Such a system maintains identity, but also makes the broadcast of keys across the blockchain network publicly traceable—while not directly or publicly linking to the individual’s identity. So while traceability remains, equally small, casual transactions can be hidden from the world.
The benefits explained in the Bitcoin white paper are related to the ability to minimize the transaction size. In other words, electronic cash and micropayments. Bitcoin has falsely been promoted as digital gold (Popper, 2015), but the reality is that the system holds no such properties. Bitcoin scales, and has value as a payment system that solves the key problems associated with digital cash and electronic commerce (Wayner, 1996), which have been discussed for decades. Yet, Bitcoin can be expensive if the transaction volume is not maintained at a high rate. The trade-off lies in the number of nodes and the type of system.
But, the Bitcoin white paper does not mention ‘decentralisation’. The paper notes, in section 2 (Wright, 2008, p. 2), that “[a] common solution is to introduce a trusted central authority, or mint, that checks every transaction for double-spending”. Bitcoin removed the need for a central issuing authority, by automating the process. All Bitcoin tokens were issued in January 2009. At the same time, the single issue was coupled with an automated distribution process. Doing so removed the necessity to have a single trusted central authority or mint. Instead, a plurality of competing organisations audit and check one another.
In addition, any user of the system can view and audit transactions (Monrat et al., 2019). More importantly, in sending transactions between one another, individuals such as Alice and Bob can each validate their own transactions and maintain evidence of any alteration or change. Here lies an important part of Bitcoin. The simplified payment verification (SPV) functions of Bitcoin allow individuals to check and maintain the number of tokens they own, validate them, and ensure that nothing has been altered.
When Alice wants to transmit information to Bob, she can check her own set of tokens and ensure they are valid without changes. Bob can do the same thing when Alice hands him the transaction. The ability to trace transactions on the blockchain allows Bob to validate the input transaction from Alice without maintaining a full copy of the Bitcoin blockchain. The SPV functions of Bitcoin allow him to validate Alice’s transaction using the Merkle path and the hashed block headers. If anything changes in the block hash headers, then all system users will be alerted and know that something has been altered. They can perform checks without maintaining a full copy of the blockchain.
The part of the second sentence of white paper that says “[d]igital signatures provide part of the solution” refers to the first sentence, noting a “purely peer-to-peer version of electronic cash”. The first sentence was explained in the previous article. It notes the requirement that payments are “sent directly from one party to another without going through a financial institution”. As we are talking about a “purely peer-to-peer” (Schollmeier, 2001) version of electronic cash, the requirement means direct communication between the parties—and not communication through nodes.
For it to work, the solution requires Alice to send communications directly to Bob using the IP-to-IP exchange methodologies built into Bitcoin in the early days. While the BTC and other systems have removed IP-to-IP exchanges, they also removed the decentralised aspect of Bitcoin. Bitcoin is not decentralised because of nodes. Bitcoin is decentralised because individuals can directly communicate without using nodes for the exchange. In a series of communications, Alice and Bob can exchange and negotiate extensively, only settling the final transaction on-chain.
In the same process, they can create invoices and purchase orders, and save hashes of such documents, that demonstrate the exchange of information between the two parties—without such information ever going on-chain. Alice and Bob can prove their identity to each other while maintaining all such information off-chain and ensuring they follow the “new privacy model” advocated within Bitcoin (Wright, 2008, p. 6).
Bitcoin provides a solution to the provision of electronic cash and payments from one party to the other without using a financial institution. Electronic cash isn’t a system that should be designed for the transfer of millions of dollars without any supporting evidence. Just as cash requires the exchange of additional information, and AML compliance, electronic cash follows the same regulations. Bitcoin simplifies the process by automating many of the exchanges. It does not present an anonymous system; it presents a private or pseudonymous one, whereby the information concerning the exchange is not public. Yet, the fact that the information is not public does not mean it does not exist.
Conclusion
Digital signatures require a digital signature algorithm such as ECDSA and an ability to exchange identity. The exchange of identity-based information can occur in Bitcoin using the homomorphic properties of ECDSA, so that keys can be provably linked to an identity key while remaining private (Wright & Savanah, 2022). As the white paper notes, traditional electronic cash systems based on digital signatures have required the use of a trusted third party, alternatively referred to as a payment intermediary. Bitcoin removes such a requirement by having a distributed, competitive system of nodes that act as a timestamping server.
The nodes serve not as the primary methodology for disseminating and distributing transactions. Rather, the nodes timestamp and index the direct exchanges between Bob and Alice. Rather than having a trusted third party, Bitcoin utilises a competitive system where corporate entities running nodes attempt to find solutions to problems faster than their competition and earn more money. Taken together, digital signatures enable Bob and Alice to securely exchange value, while the node network indexes the transactions using an automated process that ensures the entire network is quickly alerted to any ‘double-spent’ transactions.
This article was lightly edited for clarity purposes.
References
Antonopoulos, A. M., Osuntokun, O., & Pickhardt, R. (2021). Mastering the lightning network: A second layer blockchain protocol for instant bitcoin payments. O’Reilly.
Brazell, L. (2018). Electronic Signatures and Identities: Law and Regulation. Sweet & Maxwell.
Bryans, D. (2014). Bitcoin and Money Laundering: Mining for an Effective Solution Note. Indiana Law Journal, 89(1), 441–472.
Caronni, G. (2000). Walking the Web of trust. Proceedings IEEE 9th International Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprises (WET ICE 2000), 153–158. https://doi.org/10.1109/ENABL.2000.883720
Chaum, D. (1983). Blind signatures for untraceable payments. Advances in Cryptology, 199–203.
Faltibà, Z. (2018). The Lightning Network—Striking clarity on third millennium economy. https://doi.org/10.13140/RG.2.2.25320.01283
Geiger, H., & Wuensch, O. (2007). The fight against money laundering: An economic analysis of a cost‐benefit paradoxon. Journal of Money Laundering Control, 10(1), 91–105. https://doi.org/10.1108/13685200710721881
Hunt, R. (2001). PKI and digital certification infrastructure. Proceedings. Ninth IEEE International Conference on Networks, ICON 2001., 234–239. https://doi.org/10.1109/ICON.2001.962346
Monrat, A. A., Schelén, O., & Andersson, K. (2019). A Survey of Blockchain From the Perspectives of Applications, Challenges, and Opportunities. IEEE Access, 7, 117134–117151. https://doi.org/10.1109/ACCESS.2019.2936094
Pérez-Solà, C., Delgado-Segura, S., Herrera-Joancomartı, J., & Navarro-Arribas, G. (2019). Analysis of the SegWit adoption in Bitcoin. URL: Https://Deic-Web. Uab. Cat/~ Guille/Publications/Papers/2018. Recsi. Segwit. Pdf (Visited on 06/13/2020). https://deic.uab.cat/~guille/files/papers/2018.recsi.segwit.pdf
Popper, N. (2015). Digital Gold: The Untold Story of Bitcoin. Penguin U.K.
Schollmeier, R. (2001). A definition of peer-to-peer networking for the classification of peer-to-peer architectures and applications. Proceedings First International Conference on Peer-to-Peer Computing, 101–102. https://doi.org/10.1109/P2P.2001.990434
UNCITRAL Model Law on Electronic Signatures (2001) | United Nations Commission On International Trade Law. (2001). https://uncitral.un.org/en/texts/ecommerce/modellaw/electronic_signatures
Wayner, P. (1996). Digital Cash: Commerce on the Net. AP Professional.
Wright, C. S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. SSRN Electronic Journal. https://doi.org/10.2139/ssrn.3440802
Wright, C. S., & Savanah, S. (2022). Determining a common secret for the secure exchange of information and hierarchical, deterministic cryptographic keys (United States Patent No. US11349645B2). https://patents.google.com/patent/US11349645B2/en?assignee=nchain&before=priority:20160301
Watch: The BSV Global Blockchain Convention presentation, Smart Contracts and Computation on BSV

 02-20-2026
02-20-2026