|
Getting your Trinity Audio player ready...
|
SecureWorks says the attack is “state-sponsored.”
Beware: even Word documents are not safe.
The same cyber crime group that shook the world with the infamous WannaCry ransomware is on to even more mischief. Information security service firm SecureWorks reported that the Lazarus Group is now circulating a spearphishing scam disguised as a job advert targeting workers in the cryptocurrency industry. The attack has been observed since last year, but attempts as recent as last month have also been seen.
The malware is being circulated through an email of a fake job advert, where a seemingly innocent Microsoft Word document attached to the email reportedly triggers the installation of a “Remote Access Trojan” inconspicuously in the background.
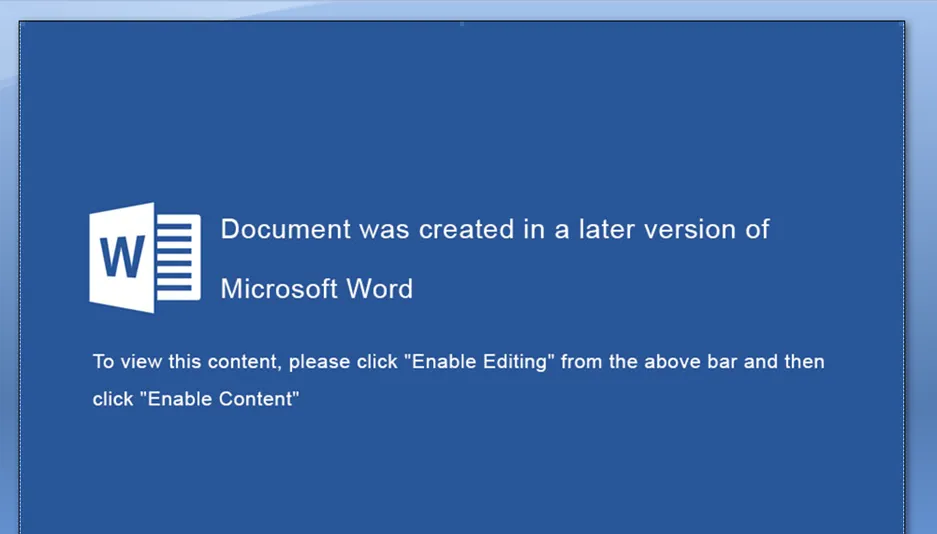
In an interview with Business Insider, SecureWorks senior security researcher Rafe Pilling says the malware assesses whether a particular computer is worth pillaging before possibly downloading more malware to assist in its operations.
“The malware that’s downloaded is the first stage RAT that gives them basic systems survey capability and the ability to download further malware if they find they’ve landed an interesting target,” Pilling said.
It is unclear if the malware has claimed any victims, and if so, how much the damage is. But SecureWorks says the operation is a big one:
“There’s a significant capability behind this threat actor — we’re not talking about five people in a room.”
Pilling believes the campaign was backed by the government, seeing as such operations in tightly controlled North Korea would be practically impossible—unless the government instigated it. The Lazarus Group has also previously been linked to the North Korean government’s operations.
“North Korea is perhaps unique in that there’s such tight control over all forms of communication,” Pilling said. “We don’t believe there’s anything that state organised cyber activity that comes out of that country. We would see it as having some degree of state direction or state approval.”

 07-02-2025
07-02-2025