|
Getting your Trinity Audio player ready...
|
A new malware that’s hiding in software development kits on both Android and iOS apps is targeting digital asset users and wiping their wallets, a new report from Kaspersky reveals.
Dubbed “SparkCat,” the new malware was found on dozens of applications on the App Store and Google (NASDAQ: GOOGL) Play Store. On the latter, users had downloaded the infected apps over 242,000 times over the past year. It was the first instance such a stealer had been discovered on the Apple (NASDAQ: AAPL) App Store, debunking the myth that “iOS is somehow impervious to threats posed by malicious apps targeting Android.”
Researchers at Kaspersky first discovered the malware on a food delivery app in Indonesia and the United Arab Emirates, which had been downloaded over 10,000 times. They say that many of the infected apps are still online, but they’ve alerted Google about the malware.
The malware scans victims’ galleries for digital asset wallet recovery phrases using optical character recognition (OCR) technology. It comes equipped with a keyword processor that filters for screenshots and other images that contain a specified length and sends them to the criminals’ servers. The malware targets recovery phrases, known as mnemonics, and scans for a dozen languages, including English, Chinese, French, Korean, and Japanese.
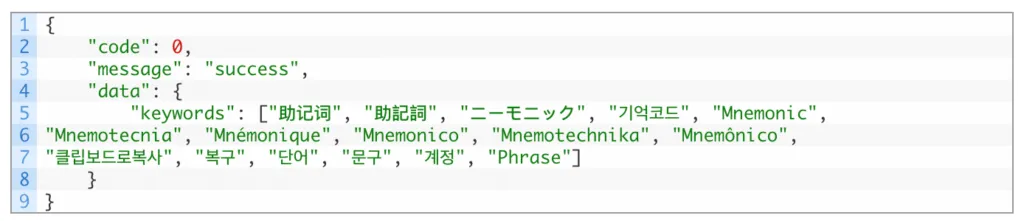
The researchers noted that the malware filtered the OCR outputs for keywords, word length, and through localized dictionaries, which it stored on the infected device.
Kaspersky says that the attackers behind SparkCat are likely based in China as the word processor code contained comments made in Chinese. It primarily targeted victims in Europe and Asia.
“Our investigation revealed that the attackers were targeting crypto wallet recovery phrases, which were sufficient for gaining full control over a victim’s crypto wallet to steal the funds,” the researchers said.
However, they noted that the malware wasn’t limited to recovery phrases and could steal “other sensitive data from the gallery, such as messages or passwords that might have been captured in screenshots.”
Cybersecurity experts say that SparkCat and other malware find their way into app stores as most of the checks Google and Apple conduct are automated and can be bypassed by criminals. Additionally, these criminals will sometimes submit a clean version of an app for approval and later introduce the malware through malicious updates.
Watch: Certihash Sentinel Node—Improving cybersecurity with blockchain

 08-25-2025
08-25-2025 





