|
Getting your Trinity Audio player ready...
|
No! The deprecation of P2SH in the Genesis protocol upgrade is not going to introduce a “replay attack” theft of coins allowing “anyone-can-spend” rules to be used against Greg Maxwell’s (or anyone else’s) unclaimed BSV sitting in old BTC or BCH wallets. The attack vector is a red herring in the same vein as practical double-spend or hyper-inflation attacks against bitcoin – meaning the attack, while technically possible, is improbable unless the network (or in this case, multiple networks) is controlled by dishonest nodes. For the sake of exceeding caution, Bitcoin SV node will add a consensus rule to the upcoming Genesis upgrade to make any such attack that much more improbable.
The update states,
“…due to this public disclosure and explicit description of the method, we believe there is now a significantly higher risk of a dishonest miner attempting to execute this theft attack with a large amount of hashpower and consequently the economic cost to honest miners of implementing the proposed mitigation method is likely to be substantially higher as well. As such the Bitcoin SV team has determined that a stronger mitigation is now required.” -The Bitcoin SV Node Team, December 23, 2019
The crucial point to understand in this situation, is that the weakest link in every consensus network is the threat of social subversion. Propaganda and social engineering has been the tool of choice from Bitcoin Core for many years now—pointing out edge cases that do not actually threaten bitcoin from a technical standpoint in order to limit bitcoin’s ability to scale because the actors within bitcoin are riddled with fear rather than being emboldened with entrepreneurial incentive to take on profit-driven risk.
It is no coincidence that this most recent social attack against Bitcoin SV’s deprecation of P2SH was led by Greg Maxwell. Maxwell is a master of social engineering with years of practice in manipulating cultural narratives through his time at Wikipedia. Many may not be aware that Maxwell was key in the establishment of the Wikimedia Foundation to steer the management of the previously free and open source Wikipedia project. Wikimedia Foundation was established primarily by a grant from the left wing social justice activist group, The Tides Foundation, and Maxwell led that charge because he believed that “…traditional consensus systems have needed an admissions control system,” presumably managed by himself.
In short, Greg does not believe that free market economics nor proof of work can sufficiently govern bitcoin or any distributed consensus, so he fancies himself a tyrant du jour over as much free information as he can manage. He is so deliberately subversive that he was eventually removed from his role at Wikipedia with the admin logs citing a litany of infractions including:
• “Gmaxwell did engage in sockpuppetry…” – Alhutch 00:05, 23 January 2006 (UTC)
• “threats, rude insults, impersonations of an admin,” -Husnock 03:18, 25 January 2006 (UTC)
• “His behaviour is outrageous. Frankly, he is out of control at this stage. This bullying behavour of his has to stop.” – FearÉIREANN (caint) 19:36, 22 January 2006 (UTC)
• “His contribs list is beyond the pale. It’s vandalism. It’s behaviour I’d expect from an editor on a rampage, which, frankly, Gmaxwell is.” – Splashtalk 20:00, 22 January 2006 (UTC)
• “pretends to be an admin, threatening to block people who disagree with him, regularly makes personal attacks” – SlimVirgin (talk) 12:22, 22 January 2006 (UTC)
After being forcibly removed from Wikipedia, Maxwell went on to found Blockstream and become a full-time Bitcoin Core developer, Github repo gatekeeper and provocateur – spearheading social attacks against scaling bitcoin on chain for years.
On Saturday, Maxwell went to Reddit to lobby a harshly worded criticism toward one of the features of the Genesis protocol upgrade. His accusation was that Unspent Transactions (UTXOs) in P2SH addresses on BTC and BCH are in danger of being replayed on BSV and absorbed by miners as soon as the P2SH standard is wiped out by the Genesis protocol. Unsurprisingly, he focused on what the said attack could do to the price of BSV in an attempt to manipulate markets, saying:
“This should result in a massive influx of circulating coins ready for dumping on the markets and lots of popcorn for everyone who has stayed clear of this mess.” -Greg Maxwell, Reddit r/bsv, December 21, 2019
The possibility of this attack caused BitGo drop BSV support and also invited some panic from Bitcoin Cash developers who took to twitter to mirror the fears of Maxwell. Respectfully, Mark Lundeberg was responsible enough to retract his criticism, but only after Steve Shadders publicly demanded it of him with links to the Genesis Specification.
We need a little more professionalism around responsible disclosure… Let start here and now… https://t.co/0yn8UNBdCv
— Shadders (@shadders333) December 23, 2019
This is far from the first time these sorts of P2SH (and Segwit) attacks have been discussed, so why does this keep coming up? Well, Craig Wright has mentioned a “flaw” with Segwit more than once in the past that can apply similarly to P2SH addresses. Interestingly, these sorts of P2SH attacks have been written off by many popular talking heads of Bitcoin Core. At the same time, others have simultaneously warned about their voracity. In contrast to Maxwell and Lundeberg’s warnings, in 2017 Andreas Antonopolous notably criticized the notion of a Segwit or P2SH attack saying:
I disagree with Craig Wright about Segwit. The exact same risk could be said to exist with P2SH. Neither can be exploited with a 51% attack
— Andreas (aantonop Team) (@aantonop) June 20, 2017
“I disagree with Craig Wright about Segwit. The exact same risk could be said to exist with P2SH. Neither can be exploited with a 51% attack.” Andreas Antonopolous, Twitter, June 19, 2017.
As Shadders pointed out, the problem with the baseless criticisms of the non-existent P2SH “exploit” is that the vectors for the attack are clarified in the Genesis Specification on UTXO management. In theory, a P2SH replay attack could occur in the same way that a double-spend or an inflation event could occur – which is to say that it is practically impossible as long as honest nodes control consensus.
The Genesis specification states:
“If a transaction is confirmed in a block that has a height which is greater or equal to the Genesis activation height, then the outputs of that transaction must comply with the Genesis Upgrade. If a transaction is confirmed in a block that has a height which is less than the Genesis activation height, then the outputs of that transaction must comply with the rules prior to the Genesis Upgrade.” -Daniel Connelly, Genesis Upgrade Specification, December 12, 2019.
So what is P2SH?
Pay-to-Script-Hash (P2SH) is a soft fork in the Bitcoin Core protocol coded by Gavin Andresen and merged as BIP16 in 2012. It is lightly used except to manage multisig transactions in Bitcoin Core, Cash and SV (until the return to Genesis.) However, it can also be used to initiate payments that hide output scripts at the time they are created, which tampers with bitcoin’s fundamental design as a complete ledger of truth.
Another differentiator that P2SH introduced is the developer-centric precedent of Bitcoin Core’s leadership ethos. BIP16 helped establish that contentious upgrades to bitcoin could be added to the repo via “soft fork.” In contrast to a hard fork that requires far more network cooperation to implement, a soft fork can be rolled out more simply by protocol developers who want to accomplish their own goals even if they are opposed by the miners. The successful merging of P2SH into Bitcoin Core helped pave the way for “Replace By Fee” (RBF) and then the Segwit network take-over in the following years.
Since P2SH has a spurious history and does not do anything valuable that cannot be done more simply and stably in standard bitcoin scripts, it will be eliminated in Genesis.
So is there also a Segwit attack?
Actually, Segwit *is* an attack. Like P2SH, Segwit was activated as another soft fork to the Bitcoin Core protocol as part of a compromise established in 2017’s New York Agreement to raise the block size limit. However, Bitcoin Core developers and their surrogates across social media reneged and incited a de facto coup d’etat against a super majority of miners who were signalling support for Segwit2X. This “User Activated Soft Fork,” (UASF) is an invalid governance change to the network, and it was the last straw for the big blockers who finally hard forked away from Bitcoin Core in 2017. UASF is also an example of the bitcoin network being controlled for the first time by dishonest nodes; inciting a network revolt to oppose Nakamoto consensus via sybil attack. This sort of dishonest signalling was warned against multiple times in the Bitcoin White Paper, and stated explicitly in section 4:
“If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs.” – Satoshi Nakamoto, Bitcoin, 2008
Interestingly, the criticisms of Segwit do not stop outside the fortress walls of Bitcoin Core’s inner circle. In fact, among the developers of Bitcoin Core, there are admitted problems with Segwit’s game theory. Peter Todd wrote his concerns about the soft fork, saying:
“…the UTXO set can be updated without the witness data, it would not be surprising if at least some of the wallet ecosystem skips witness validation.”
“With that in mind, what happens in the event of a validation failure? Mining could continue indefinitely on an invalid chain, producing blocks that in isolation appear totally normal and contain apparently valid transactions…” – Peter Todd. Segregated Witnesses and Validationless Mining, December 23, 2015.
In short, Segwit signatures existing outside the block make it plausible for miners to create a dangerously long invalid chain relying on witness data rather than bitcoin signatures. This could put miners in a precarious situation where they have been mining an invalid chain for so much time, that it is infeasible for them to come back into consensus with the valid chain. Restarting back at the last valid block would mean sustaining massive losses, so any solution would come with many political and logistical headaches.
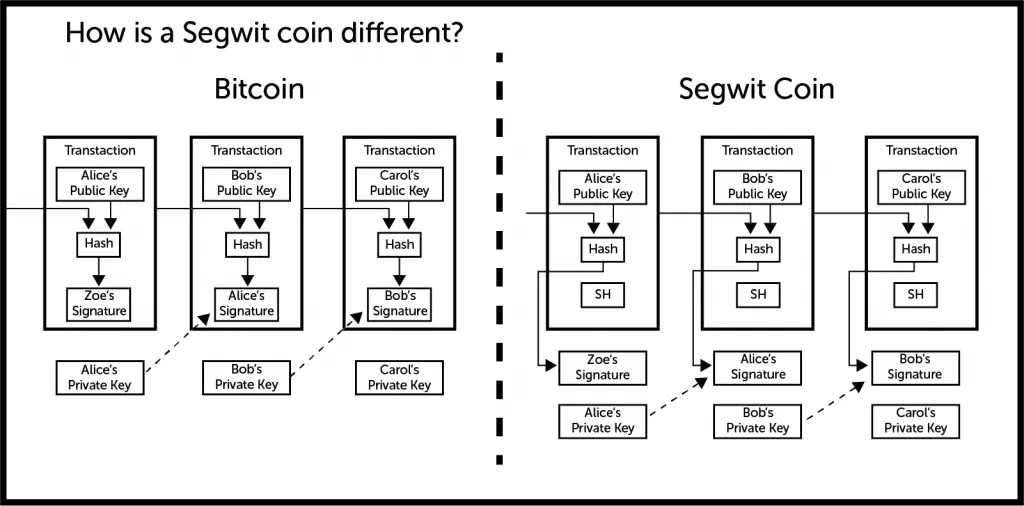
The other attack is the plausible forming of an anti-Segwit mining cartel purposely mining an invalid chain and then forcing a reversion back to the standard chain and confiscation of Segwit coins that users had transacted. This attack is in the same vein as the P2SH attack theorized this week by Greg Maxwell.
Segwit is also self-sabotaging of Bitcoin Core’s network effect in the cryptocurrency ecosystem. The classic assumption about altcoins is that they would test out new ideas that could ultimately be merged into Bitcoin Core if they were deemed viable. However, Segwit is such a fundamental change to the code that it negates most scenarios from which Bitcoin Core could benefit from work done on other blockchains.
What is the solution?
There are very real attack vectors for Segwit and P2SH wallets, but their execution relies on code that only exists in Bitcoin Core. Plus, for the plausible attacks to be successful, the networks need to be controlled by dishonest nodes who are willing to burn money for the sake of stealing replayed coins.
These attacks do not exist in bitcoin! In fact, bitcoin was created to eliminate sybil attacks and other types of problems caused by dishonest actors and their nodes. When dishonest nodes control the network like they do in Bitcoin Core, neither instant transactions nor SPV can be trusted, consensus rules cannot be guaranteed and the network falls into chaos because the incentives fall out of balance. The only recourse for such a network is for protocol devs to make careers out of micromanagement, and that is a very dangerous foundation for a network to be built upon! Incidentally, it is also a very profitable premise upon which to raise venture capital money to start a bitcoin micromanagement business like Blockstream.
For these reasons, Bitcoin SV will be taking a giant step closer to the original bitcoin rule set by sunsetting P2SH in Genesis and restoring a host of bitcoin’s largely forgotten basics. Once again, Bitcoin SV will show the world that the solution to bitcoin’s woes is always to become more closely aligned with bitcoin’s fundamental incentive model.
Editor’s note: This article has been updated.

 08-04-2025
08-04-2025 




