|
Getting your Trinity Audio player ready...
|
Hackers are targeting Docker servers with a new digital currency mining malware, a new report has revealed. The criminals scan the internet for Docker servers running API ports without a password, infect them with the malware and mine digital currencies. The malware can also steal credentials, allowing the criminals to spread to other servers in the network.
This campaign has been ongoing since last year, researchers from cybersecurity firm Aqua Security stated in their report. It relies on persistence, with thousands of attempts taking place on a daily basis. These are among the highest number of attempts the researchers have seen, leading them to believe that the group behind the attacks have sufficient resources and infrastructure.
Once the hackers spot an exposed or misconfigured Docker API port, they then spin up an Ubuntu container. They use this to download a shell script that in turn downloads the malware and installs it. This malware is known as kinsing and is a Golang-based Linux agent, the report details. Before the malware begins mining digital currencies, it attempted to communicate with servers in Eastern Europe, leading the researchers to discover that “there are dedicated servers for each function that the malware executes.”
Kinsing’s primary purpose is to mine digital currencies. However, in order to increase its efficiency, it comes with other functions. They include disabling security measures and clearing logs, killing most applications, and especially other malware and digital currency miners and killing other running malicious Docker containers.
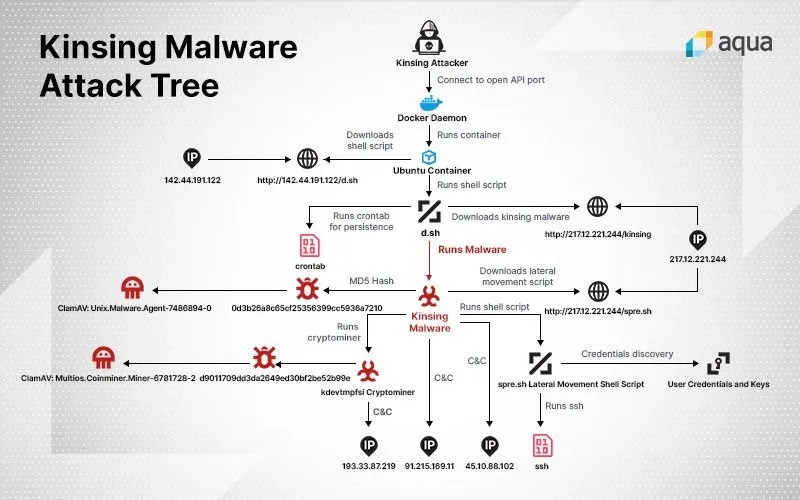
The researchers urged security teams to up their game as the attackers are unrelenting. They stated, “With deployments becoming larger and container use on the rise, attackers are upping their game and mounting more ambitious attacks, with an increasing level of sophistication.”
Some of the steps that security teams can take include reviewing authorization policies; scan all images used and avoid enhanced privileges; investigate logs for anomalies and consider using cloud security tools for their cloud resources.
Cybercriminals have continued to target Docker systems, lured by the vast computational resources that they stand to gain if they successfully infiltrate them. In October 2019, a digital currency mining worm was found using malicious images on Docker for propagation. Known as Graboid, it was the first of its kind and mined Monero.
Just a month later, Bad Packets LLC, an American cybersecurity firm discovered a new digital currency mining malware, once again targeting Docker systems. Just like with kinsing, the attackers targeted Docker servers whose API endpoints were exposed online. They also mined Monero, a darkcoin that has proven popular with criminals.

 07-14-2025
07-14-2025 





