|
Getting your Trinity Audio player ready...
|
Cisco Talos, the threat intelligence team at Cisco Systems, discovered a new digital currency mining botnet attack called “Prometei,” which mines Monero (XMR) and steals data from the targeted system.
According to their report, the botnet has been active since March. It was found by examining telemetry information coming to Talos from Cisco AMP for Endpoints’ install base.
The new botnet is noteworthy since it uses a complex, extensive modular system and a mixture of techniques to compromise systems and hide its presence from end-users to mine for Monero (XMR). The malware also uses several crafted tools that help the botnet increase the number of systems taking part in its Monero mining pool.
Prometei’s attack starts with the attempted compromise of a machine’s Windows Server Message Block (SMB) protocol via SMB vulnerabilities, including Eternal Blue.
The botnet has over 15 executable modules that get downloaded and controlled by the central module. The central module talks with the command and control (C2) server over HTTP. It transfers the encrypted data using RC4 encryption while the module shares the key with the C2 using asymmetric encryption.
Aside from a significant focus on expanding across the environment, Prometei also tries to recover administrator passwords. The found passwords are sent to the C2 and then reused by other modules that attempt to confirm the validity of the passwords on different systems using SMB and RDP protocols.
The Prometei botnet is grouped into two main branches: one C++ branch devoted to block reward mining operations, and one—based on .NET—which focuses on password theft, the abuse of SMB, and obfuscation.
The main branch can operate independently from the second as it contains abilities for communicating with a C2, steal credentials, and Monero mining. Auxiliary modules are also bolted-on, the malware can be use to communicate over TOR or I2P networks.
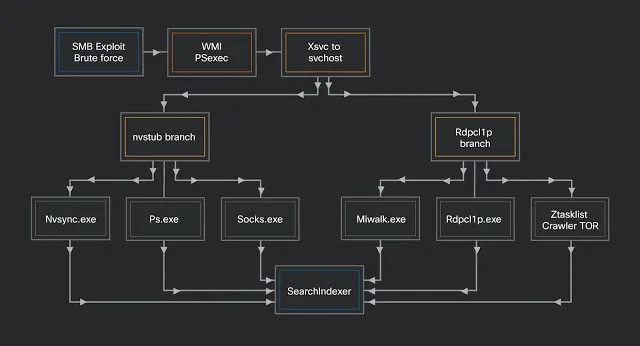
The auxiliary modules can also gather system information, check for open ports, spread across SMB, and scan for the existence of any digital currency wallets. Once systems have been compromised and added to the slave network, the attacker can perform a variety of actions or tasks.
Based on Talos’ analysis of the mining module, current numbers of Prometei-infected systems are in the “low thousands.” Prometei requests have been detected from countries including the U.S., Brazil, Turkey, China, and Mexico.
Organizations need to be constantly vigilant and monitor the behavior of systems within their network. While they need to be focused on protecting their most valuable assets, they should not ignore threats that are not targeted toward their infrastructure.

 08-14-2025
08-14-2025 




