|
Getting your Trinity Audio player ready...
|
Privacy seeking users who turn to the renowned Tor browser have been the target of an extensive campaign by attackers who aim to steal their BTC. According to a report by We Live Security, the attackers have been using a trojanized version of the Tor browser to target Russian-speaking users. The attack has managed to steal over $40,000 in BTC from the victims so far.
The attack has been propagated using two websites which claim to offer the Russian language version of the Tor browser. Their two domains—tor-browser.org and torproect.org—were created in 2014, but they became more active in 2017 and 2018 respectively. The second domain is quite close to the original Tor browser domain, torproject.org. For Russian speakers, the omission of the letter ‘j’ may not raise much of an alarm, a fact the attackers have exploited to their benefit.
However, the hackers haven’t relied on the mistype alone. They have actively promoted the two domains on popular Russian platforms and forums. Their messages included topics that resonate with internet users such as cryptocurrencies, darknet markets and censorship bypass. They have especially relied on assuring the potential targets of their right to internet privacy, an area that’s dear to Russians in the face of increased censorship by the government.
These tactics have proven effective, with the accounts promoting them being viewed more than 500,000 times. However, there’s no way of determining how many of these visitors went ahead to download the trojanized browser.
Once a user downloads the trojanized Tor browser, it displays an urgent message that notifies them that their browser is outdated. This message is displayed even if the user has the most up-to-date Tor browser version. Once the user clicks on the ‘Update Tor Browser’ icon, he is redirected to other websites run by the attackers.
The trojanized Tor browser is fully functional, with the attackers not making any changes to the source code of the official Tor browser. However, the criminals have tinkered with some of the default settings and extensions. These include disabling the ‘Update browser’ extension as this would give the victim the chance to update to the legitimate version.
The attackers have included a Javascript payload that targets three of the largest Russian-speaking darknet markets. The payload attempts to alter QIWI and BTC wallets located on pages of these markets. QIWI is one of the most popular money transfer services in Russia.
Once the user decides to add funds to the account directly using BTC payments, the trojanized browser automatically swaps the original BTC address for one controlled by the criminals.
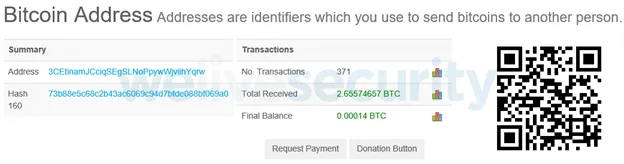
One of the BTC addresses used by the criminals in this attack has had 371 transactions, receiving 2.65 BTC, according to the report. Overall, the addresses linked to this scam have collected over 4.8 BTC, equal to over $40,000. The stolen amount is likely much higher as the trojanized browser also alters QIWI wallets.

 08-26-2025
08-26-2025 




